- Home
- OneDrive
- Discussions
- Silently configure OneDrive using Windows 10 or domain credentials
Silently configure OneDrive using Windows 10 or domain credentials
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Oct 12 2017 12:48 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 12 2017 12:48 PM
Hi ,
In reference to :
(Preview) Silently configure OneDrive using Windows 10 or domain credentials
I have a few questions;
The article states that "This policy lets you configure the OneDrive sync client silently using the primary Windows account on Windows 10, and domain credentials on Windows 7 and later."
What is a primary windows account on windows 10? I have a Win 10 and i sign in using a domain account.
I created the registries for EnableADAL and SilentAccountConfig , restarted the sync client and also the machine.
This does not sign me in to my account automatically. Is there something i am missing?
I noticed a few things after adding the registries;
1.Theres a new file added under C:\Users\username\AppData\Local\Microsoft\OneDrive\settings called PreSignInSettingsConfig.json
2..Everytime i launch the onedrive app and the sign in screen appears; it creates a new update file at:
C:\Users\username\AppData\Local\Microsoft\OneDrive\setup\logs and the contents of the file say its trying to refer to the .json file mentioned in 1.
I am not sure what i am doing wrong, any help would be appreaciated.
- Labels:
-
OneDrive for Business
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 16 2018 02:06 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 11 2018 09:01 AM
I would like to know this too. We don't have ADFS, will this work without it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 30 2018 12:52 PM
Any idea when this will come out of preview?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 09 2018 01:01 PM - edited May 09 2018 05:54 PM
I was also having this problem and it sounds like my environment is similar to yours (ADFS and MFA) In addition to setting the GPOs you have set and setting the reg value "ClientEverSignedIn" to 0, I also had to set "SilentBusinessConfigCompleted" to 0.
Once that was done, it began to work when OneDrive is launched.
It's a requirement that all my users be logged into OneDrive whether they want to or not, so I've created another GPO to check if the user is configured and reset the above reg keys to 0 if they are not.
OneDrive creates a new key in the format of Business<digit> under "HKCU\Software\Microsoft\OneDrive\Accounts" for any business accounts that have been logged into OneDrive. Under that key, you can use "ConfiguredTenantID" to check that they're configured for your tenant and "UserFolder" to see where it is configured to sync to.
Also, if OneDrive does not start in the foreground, it will not configure using ADAL. The OneDrive startup reg key has the "/backgroud" parameter set, so my GPO checks to see if the user is configured and if they are not, it adds a RunOnce entry without the "/background" parameter.
It would seem HTM files are not allowed to be attached, so I've attached a screenshot of my GPO report.
The HTML can also be found here if you'd prefer that:
https://pastebin.com/1ebujuU5
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 09 2018 05:32 PM
If this method auto signs the current window domain user into onedrive, can it be set to auto login to any office 365 deployed apps locally installed on the machine? I'm using shared computer activation method for o365 deployment. All domain users have o365 accounts, we are deploying o365 apps onto images for rollout throughout school district. Once the user logs into the computer with their domain account, I'd like them to be able to launch any of the installed o365 apps and be auto logged in. I'm wondering if some variation of this onedrive technique would work. Right now users are still getting prompted to sign in to activate office, so it can pull a shared license key from o365.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 09 2018 06:03 PM
I have not tried setting it up for other office apps.
From here:
https://support.office.com/en-us/article/How-modern-authentication-works-for-Office-2013-and-Office-...
It looks like it should be enabled in Office 2016 by default.
You may also want to look here:
https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnect-sso
As it explains some of the other pre-reqs for ADAL auth if you're syncing with on-prem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 13 2018 01:22 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 13 2018 01:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 17 2018 11:59 AM
We are now getting consistent results if we run %localappdata%\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe, wait for it to finish, then launch OneDrive and it logs in with Modern Auth (No prompting)
Hope this helps. This thread was extremely helpful!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 01 2018 04:01 AM - edited Oct 19 2018 11:40 AM
I have almost all working on latest client 18.151.0729.0012 apart from the actual "Silently redirect Windows known folders to OneDrive"
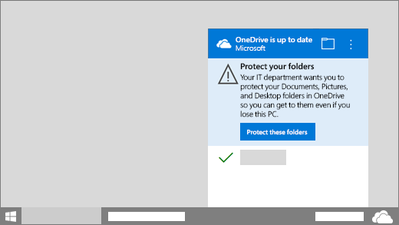
I have it enabled with tenant ID & show notification YES, but instead this happening on the client I have "... a reminder notification will appear in the activity center until they move all known folders."
If I click Protect these folders it work fine, but I do NOT want my users to have any input!
Seb
edit
I see it now, it is VERSION number that needs to change!
Silently move Windows known folders to OneDrive
Use this policy with the sync client build 18.171.0823.0001 or later to move your users' known folders to OneDrive without user interaction. (You can choose to display a notification to users after their folders have been redirected.)
EDIT 2
That is NOT true at all, as I have it working even on current version fine following my own setup:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 09 2018 12:36 AM
Hi,
Did you have any problems installing the One Drive client on your windows 10 PC's? Mine looks to install and then just closes without the OneDrive client being available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 09 2018 03:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 09 2018 05:28 AM
The specific key is HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\OneDrive\DisableFileSyncNGSC = DWORD:1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 13 2018 01:31 PM - edited Nov 13 2018 01:35 PM
Hello,
you need to run GPRESULT with admin rights. Launch a command prompt with administrator rights, and in the cmd window launch your GPRESULT command (including the option "/scope computer" if you only want to report on the GPO affecting the computer)
Michel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 15 2019 12:50 AM
in GPO explanation:
If you enable this setting, users who are signed in on the PC with the primary Windows account (the account used to join the PC to the domain) can set up the sync client without entering the credentials for the account. Users will still be shown One Drive Setup so they can select folders to sync and change the location of their One Drive folder.
So only admin, who have joined PC to domain can set up Onedrive silently???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 01 2019 02:11 AM
Does anybody know if we need an Azure AD Sync with an ADFS infrastructure or if Azure AD Sync with Password Sync will work as well?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 30 2019 06:38 PM
@Manuel_Martinez either should work whether it's a federated domain or managed. There are separate steps for federated vs managed, but the same process through azure ad connect hybrid setup wizard.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 21 2023 01:44 AM
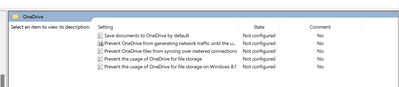
@Jeremy Friesen In my Group Policy does not have the OneDriveGroupPolicy (Silently sign in users to the OneDrive sync app with their Windows credentials) like you've mentioned in the picture. I am using Windows Server 2012 R2. Below is the picture you can see it.
Would be appreciated if you could advise on that. Because I need the OneDrive to silently sign-in with Computer credential When the users logged in to the computer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 21 2023 06:59 AM
You'll need to update your Onedrive Policies. Here's a link with instructions.
Use OneDrive policies to control sync settings - SharePoint in Microsoft 365 | Microsoft Learn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 25 2023 10:01 AM
- « Previous
- Next »