- Home
- Microsoft 365
- Microsoft 365
- Re: Multi-factor Authentication breaks outlook
Multi-factor Authentication breaks outlook
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 16 2017 12:36 PM
Just wondering if anyone has run into this issue.
I have been Turning on MFA for users a group at a time all was going smooth. The next morning after turning on MFA for the last hand full of users I had to force a password change company wide due to an internal issue. After doing this it caused outlook to start prompting only for the last hand full of users. No matter which password was entered it continued to prompt. I tried the domain credentials and i even popped in the app password as I read an article that mentioned this but this did not work for me. Just wondering if anyone has run into something similar or can shed any light that may have caused this issue while i wait for 2nd level support to call me.
- Labels:
-
Admin
-
Exchange
-
Office 365
-
Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 17 2017 12:06 AM
If you have MFA enabled, you should use an Outlook version that supports Modern authentication. 2013 SP1+ should do, but Modern auth must also be enabled client-side and server-side:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 17 2017 01:09 PM
We have been using office 2013 pro plus with the ADAL Reg keys in place. This setup has been in place for months. Then out of the blue after we forced a password change this issue occured.
MS says they are having issues with Outlook and ADAL ATM but there is nothing on the Portal in ref to this. I dont think OUtlook version is the issue here as this was all working fine for months until last Wednesday.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 18 2017 12:34 AM
Well, the least they can do is push this info to the SHD, so make sure you give them some grief :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 23 2017 11:45 AM
Agreed, turns out that turning on MFA for these 41 users breaks outlook. MS confirmed the issue on MS side. THey are suppose to be updating our tenant but Im still waiting. I was told that this issue is affecting other tenants in o365.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 25 2017 07:07 AM
Well i found in testing something is absolute being cache as to what that is i don't know. I also don't know if i want to spend anymore time on this than i have. I took 2 users turned on MFA, broke outlook and i then wiped the Windows Profile and that seemed to fix the issue for me. I don't think I should have to go to such extreme to have the end user recreate the windows and then the mail profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 21 2018 08:14 PM - edited Mar 21 2018 08:18 PM
Thanks for the discussion here. I ran into this problem on our RDS server which runs alongside a domain controller in Azure. I checked the Autodiscover settings in the Domain Controllers DNS server and they reflected those in the public DNS.
I was able to connect outlook to Office365 on another computer and so knew the MFA was working. I tried connecting the account using an Admin login account which I knew had been used to access a different users Office365 account but never my account and definitely no account with MFA enabled.
I deleted the Outlook profile but still could not connect.
I deleted the entire user profile off the RDS server and logged in again. This time Outlook connected to Office365.
Knowing it would work I now backed up all data from my own user profile and deleted that. Logged back in and Outlook now connects ok.
So, the autodiscover and setup process is storing something in the users profile or User registry that do not get deleted just by deleting the Outlook profile.
It would be nice to be able to put my finger on it and just delete that part without having to delete the entire user profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 26 2018 01:23 PM
Unbelievable. A reghack to be a fix to MFA on Office 365 accounts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 30 2018 10:36 AM
I was never able to put my finger on it, nor was MS for that matter which is sad!
I reached a point where I am down to 2 users left with this issue and our help desk has been pushing out Outlook 2016 which has Modern Auth on by default.
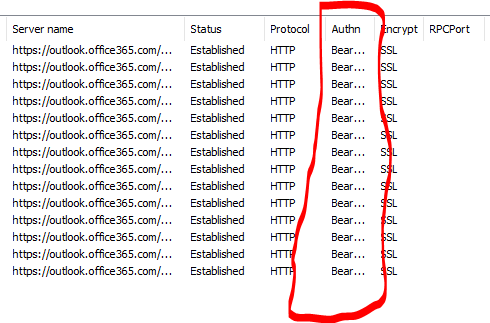
The issue that caused this was Outlook2013 stuck on legacy AUTH and not using Modern Auth. How can you tell? If you open Outlook Connection Status, under the AuthN field if it says clear (Legacy Auth) If it says Bearer* (Modern AUTH).
I found another fix as well but its more time consuming. I ran MS SARA and chose outlook keeps prompting for credential which also happened. Running thru that and just telling SARA to continue to fix the issue and get to a point where it asks did I want it to recreate the profile I said yes and that also did it. After letting SARA create the profile After a few minutes all the connections would start changing from Clear to BEARER. THis part took about 10 to 15 min just had to let it sit and monitor it.
If i just recreated the profile myself without sara it would not work. So that tells me that MS SARA was also wiping something out in the windows profile as 9 times out of 10 I used sara it would work.
Those times I SARA did not work and outlook still connected using legacy Auth is where I would wipe the Windows Profile.
You can also verify by going to registry HKCU\Software\microsoft\office\16.0\Common\Identity\identities
Under here you should have
https://autodiscover-s.outlook.com/
https://domain.sharepoint.com/
https://domain-my.sharepoint.com/
https://outlook.office365.com/
https://dataservice.o365filtering.com
Users who connect using Legacy Auth who also have CLear in the AUTHN column in connection status will have only 2 of these reg keys.
Alot of time wasted but at least i got to the bottom of it sort of.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 24 2018 06:37 PM
I actually dealt with a similar issue today where a users Outlook would stay at "Disconnected" in the bottom right while outside of our whitelisted network IP range. Our organization turned on Multi-Factor auth through the modern Azure portal about 3 months ago. We had prepared the organization by making sure the registry keys were being pushed out via group policy AND confirming that our machines were patched with the latest Office 2013 patches (that should get the required files to the right versions; outlined here in the "MSI-based installations" section). Today we began enforcing multi-factor auth through the classic Azure portal because even when you turn on MFA, your users can still use 'Legacy Auth'. That's when this behavior began - the user simply could not connect when outside of our white-listed network.
I ran the incredibly helpful Office CAT and this pointed me in the right direction. It turns out that I was missing the files that the patches mentioned above should have installed. I installed those missing KB's (in this case, the Csi.dll and MSO.dll files were missing from the C:\Program Files(x86)\Common Files\Microsoft Shared\OFFICE15\ directory) and it connected finally.
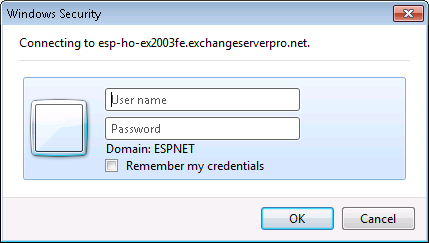
Another red flag that you should keep in mind is when you setup an Outlook profile OR your user is prompted for their password (in your case after changing the password), that the password box is the basic username/password box. This means your client is attempting to connect with Legacy/Basic Auth, instead of modern auth. Make sure your registry keys are set AND you have the right file versions and Office 2013 patches.
Modern Auth Prompt GOOD:
Legacy/Basic Auth Prompt (attached) BAD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 01 2018 08:05 PM
Mike, can you share what hotfixes you are talking about? I found modern auth works on office pro plus; if does not work on our volume versions of standard. If there was a way to fix this it would be great!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 02 2018 03:40 PM
As I mentioned above, there is a website (https://support.office.com/en-us/article/Plan-for-multi-factor-authentication-for-Office-365-Deploym...) that outlines what is required for this to be successful. Scroll down to the "MSI-based installations" section and it will highlight what patches are required based on what file version you have in your "Program Files" or "Program Files (x86)" folders.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 29 2018 10:53 AM
Has anyone actually figured this out? We use Outlook 365 (Office 365) turned MFA and it "breaks" Outlook 365. As mentioned above, it keeps asking for a password and it will not take it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 05 2018 07:55 AM
Yes, the issue was outlook was not connecting to O365 using Modern Auth. IF you check outlook connection and it says "Clear". Then outlook is NOT connecting using modern auth. IF it displays "BEARER" like below then it is using Modern Auth. The only fix that I found that works 100% of the time is wipe the User Windows Profile and recreating which means its something in the Windows profile. I used MS SARA and that was a process I just kept telling SARA the fix didnt work until it reached a point where it asked if I wanted it to recreate the Outlook Profile and that also worked but it take over 10 to 15min and sometimes didnt work.
There was something in the Windows profile that gets wiped and allowed outlook to connect over modern auth. I was only running outlook 2016 which has Modern auth built in so no reg keys needed.
I chose to do redo the Windows Profile it was faster to do this than sitting for 15min for MS SARA to possibly fix it. I only had 55 to 60 users out of 300 that had this issue when I turned on MFA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 21 2018 09:28 PM - edited Nov 21 2018 09:28 PM
Have you tried going into Windows Credential Manager under the user profile and removing the stored Outlook credentials and then starting Outlook again?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 22 2018 05:20 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 22 2018 05:22 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 11 2018 11:36 PM
When setting up MFA you have to possibility to retrieve or create an app password. You should use that one during login in Outlook.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 02 2019 08:48 AM
Unfortunately, the app password does not work in this case. If you get the old Auth screen you will not be granted access in Outlook no matter what password you use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 02 2019 12:16 PM
I never use app password, with Outlook 2016 all auth goes to ADFS.
Ap passwords i usually use on mobile devices etc.