- Home
- Microsoft 365
- Microsoft 365
- How Microsoft thwarts phishing attacks with Office 365
How Microsoft thwarts phishing attacks with Office 365
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2017 05:38 AM - edited Sep 08 2017 05:39 AM
It's no surprise Office 365 phishing attacks are on the rise, Office 365 is a nice juicy target for the bad guys. If just one account is compromised, it potentially provides access to so much data, that could snowball and risk major data leakage etc.

How many users would fall for a fake login screen taking the above into account, like this:

Or this perhaps:

Microsoft has published "Microsoft thwarts phishing attacks with Office 365", that is well worth reviewing and getting a better understanding of what Microsoft is doing about this.
- Labels:
-
Exchange
-
Office 365
-
Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2017 06:25 AM
Awesome - thanks for sharing this success story on ATP!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2017 10:03 AM
I believe the most-impactful, user-facing improvement they've made on this front is to finally start rolling out the functionality to not display user photos is spoofed messages: https://blogs.msdn.microsoft.com/tzink/2017/09/05/showing-a-question-mark-in-the-sender-photo-when-a...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2017 10:24 AM - edited Sep 08 2017 10:32 AM
Thanks Vasil, that's a useful feature that should help and sounds like it's overdure. If I understand correctly, does that mean if someone spoofs your emaill address (for example), currently it shows your photo to the recipient, lending more credence that's it's a really a legitimate email when it's actually from the spoofed sender? With this feature, there will be a question mark on the sender photo instead, as it's unauthenticated.
It would be nice to see it across all Outlook plaforms, assuming it's OWA/Outlook.com only, which it sounds like.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 08 2017 02:23 PM
This is the same feature as Gmail has had since February 2016 and will be implemented in OWA first. Whether it shows up in the other Outlook clients is in the hands of the developers...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 15 2018 03:52 AM
A few updates that might be of interest including the risk of ransomware infecting Office 365 mailboxes and the corresponding mitigation.
Ransomware is a well-known threat that usually comes in via phishing links or via email attachments. Taking this to the next level there is a risk of Office 365 mailboxes from being encrypted and held for ransom. Other cloud services may also be affected.
This was shown a couple of days ago on an Office 365 mailbox, while it was simulated it's still alarming and well worth reviewing.
Here is a demonstration, which shows a link in a phishing email being clicked and the user agreeing to grant rights, then all emails being encrypted and then finally the ransom being paid and all emails restored:
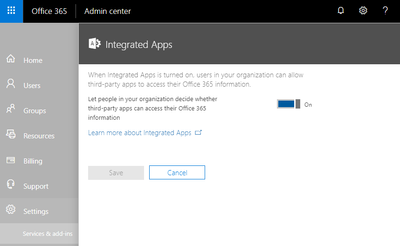
It's possible to mitigate this threat but it does have implications, as it requires turning Integrated Apps off on a tenant per these instructions, this setting is on by default:
Obviously, review the impact before changing this setting. Coaching/training staff in how to spot phishing emails is crucial and not to act upon when they are instructed to carry out actions, like clicking links etc. Make sure staff know about Safety tips and how to take them into account - Safety tips in email messages in Office 365.
Also, it's important that when harmful spam/phishing does get through that these are reported properly, here are are some instructions on how to do this - When creating support tickets about spam, be sure to include message headers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 15 2018 04:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 17 2018 06:26 PM - edited Jan 17 2018 06:27 PM
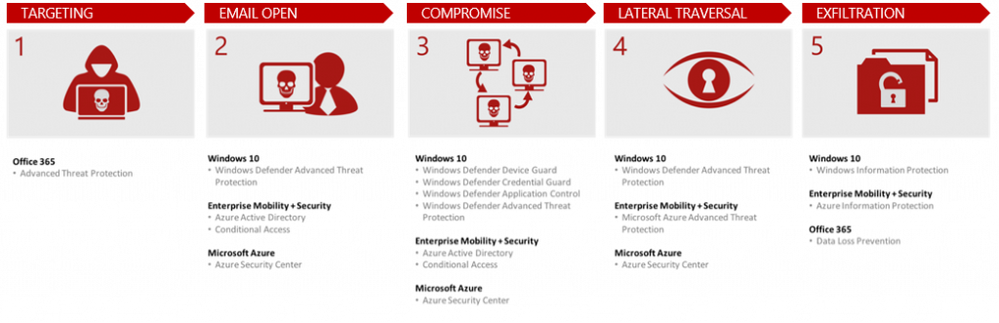
This article and illustration is a useful summary of how the solutions in Microsoft 365 (EMS, Windows 10 & Office 365), as well as Azure, can disrupt the different stages of phishing attacks:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 25 2018 09:30 AM
That's true Petr, it's always a balancing act and is important to get the right approach, that doesn't unnecessarily diminish productivity but also protects from different types of threats. Things like conditional access and MFA are great in those regards.
Microsoft has talked more about what they are calling Illicit Consent Grants, which was the approach used in that proof of concept to encrypt a user's Office 365 mailbox for ransom.
"Office 365 Security has been tracking an emergent threat to customer data in the Office 365 cloud over the last year. This blog post is intended to help IT Administrators of Office 365 organizations detect, monitor, and remediate this threat."
Microsoft is recommending admins proactively run at least weekly a script to unearth applications with illicit permissions. Further advice here - Defending Against Illicit Consent Grants.
It would be great if these are added in Azure AD reporting, as currently this can only be viewed on a per-user basis in the portal. Then get them added to Secure Score, as an additional check.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 25 2018 10:22 AM
The problem for us is only options provided:
- Allow and "grant" all apps to users (and after that checking added apps)
- Allow only set of apps explicitly added by IT (and hoping that we do not miss important app)
But users do not want to contact IT about asking for access. They likely to start complain within kitchens. :)
I liked if there will be the third option: Let user add the app, IT receive this request and accept or deny the app, then user is notified and app is granted to him.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 26 2018 06:14 PM
Agreed, the options are rather basic and could do with more finessing, like what you have suggested. In other news, security attack simulation is coming to Office 365 for phishing and brute force testing with end-users. Not much to go on yet but it's already looking very promising!