- Home
- Microsoft 365 Groups
- Microsoft 365 Groups
- Hide Groups from a Guest User
Hide Groups from a Guest User
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 02:27 AM
How can I hide the list of Office 365 Groups in my tenant.
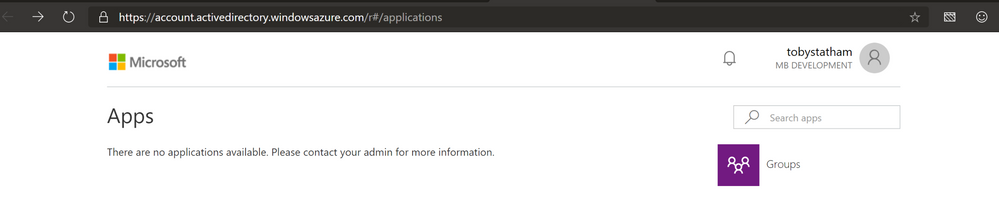
When a guest account is added through Azure AD and the invite email is sent, they follow the instructions to login into the Guest tenant and end up on this landing page.
https://account.activedirectory.windowsazure.com/r#/applications
The Guest User can then click on Groups and Join Group and see a list of all the tenant groups and the members of any of the groups.
How is this possible? A guest user shouldn't be able to see a list of internal groups. The names alone could possibly give away important information (internal project, other third party companies, etc.)
Surely there should be a boundary for listing groups between an internal and external user?
- Labels:
-
Admin
-
Office 365
-
Office 365 Groups
-
SharePoint
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 02:48 AM
Yes there boundaries but they will have read on for example groups etc! This is the way it works! Surely you can hide from Gal etc..
Please see the following docyment:
Adam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 03:04 AM - edited May 16 2019 03:05 AM
Understand that's the way it works, doesn't necessarily mean it the right way.
I would have thought that when a guest user is added to a tenant it should be given the least permissive permissions by default and then further permissions can be added if needed dependent on the role of the Guest User.
Is there a setting or policy that can be applied to remove browse permissions on groups you are not a member of? So for example if I had a Security Group setup that has dynamic membership for all Guest Users that say that members of this group can not browse Office 365 Groups (or any other groups)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 03:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 03:59 AM
@adam deltinger not sure if I understand you correctly.
As it stands currently, by default (i.e. no changes have been made to Azure AD permissions) a Guest User can see all the Office 365 Groups in a tenant they have been invited to, nothing has to be changed to enable this.
To me this isn't least permissive, a guest user should only be able to see the groups they are a member of.
Either way, can I change this in anyway to a guest user can only see the groups they are a member of.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 08:46 AM
You should be able to control this via the Azure AD blade -> User Settings -> External collaboration settings -> Guest users permissions are limited. Here's the description of the setting:
Yes means that guests do not have permission for certain directory tasks, such as enumerate users, groups, or other directory resources.
No means that guests have the same access to directory data that regular users have in your directory.
Should be being the keyword..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 09:00 AM
@Vasil Michev Thanks for the information
I have "Guest users permissions are limited" already set to Yes. I think this must be the default setting as I haven't changed this.
Is this a bug? It says that a guest user does not have permissions to enumerate groups and a guest user can clearly do this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 09:04 AM
According to the link earlier , guests have read to non hidden groups:
“Read all properties of groups
Read non-hidden group memberships
Read hidden Office 365 group memberships for joined groups
Manage owned groups
Add guests to owned groups (if allowed)
Delete owned groups
Restore owned Office 365 groups
Read properties of groups they belong to, including membership.”
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 09:10 AM
So my assumption would be that a Guest User can't enumerate Security Groups, but can enumerate Office 365 Groups. Seems like a flaw to me
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 10:39 AM
I can enumerate every type of Group as a guest with that setting on. Looks like a bug in my book, but I've asked some folks to clarify on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 12:25 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 01:11 PM
Hi Toby, great finding and thank you for the post! This is not as it should be in my opinion.
But... You can modify it in the Azure portal.
Azure Active Directory -> Groups -> General (settings)
Change the 'Restrict acces to group membership requests in the Access Panel' to Yes
Also you can change the following settings:
- 'Users can create security groups in Azure portals'
- 'Users can create Office 365 groups in Azure portals'
If posted this feedback on uservoice for us all to vote on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2019 01:17 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 09 2020 06:58 AM
@adam deltingerThis setting still doesn't hide the Groups icon from the panel. A guest user can see all my Azure AD user accounts because they are a member of the "All Users"
Is there anyway to hide the whole app ? There is no reason for a user I am sharing a OneDrive file to be able to see.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 20 2020 06:15 AM
I am facing the exact same issue. I want our guests to see the applications but not have access to any of the groups they are part of.
There is no useful information there for them. It is also possibly a personal information protection violation for our employees.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 21 2020 01:37 AM
You can edit the dynamic membership rules of the group "All users" to exclude Guest users.
Go to Azure Active Directory -> Groups
Select the "All users" group and go to "Dynamic membership rules".
Edit the "Rule syntax"
To only include users of type Member enter the following query:
(user.objectId -ne null) and (user.userType -eq "Member")
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/use-dynamic-groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 25 2023 06:46 AM - edited Sep 25 2023 06:49 AM
From my perspective, your approach should be the standard and not the other way around.
I come across this article many years later and still: Group membership enumeration is possible and causes risks for organisations. It's easy to identify C-Level or Admin accounts by just poking around in a default setup.
I found some settings via Powershell to hide group memberships, but would assume that many customers share their memberships without knowing it. The description left the taste that I would assume something "super secretive", but it a general measure which is nothing special.
The term "non-hidden groups" causes confusion to me, since it leaves the feeling that an admin would have to "unhide" memberships and causes a wrong sense of security.
Edit: Ah and of course: There is a more restrictive option now, but it isn't default. Which leads back to poking around in default setups.