- Home
- Microsoft 365
- Microsoft 365 Blog
- Released: Office 365 Audited Controls for NIST 800-53
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We say this all the time, but it’s worth repeating here: we believe that transparency is key to earning customer trust. When you entrust your data to the Microsoft Cloud, we use advanced security technology and cryptography to safeguard your data. Our compliance with US and international standards is independently audited, and we’re transparent on many levels—from how we handle legal demands for customer data to the security of our code.
We do these things not just to be transparent, but to also make it easier for you to perform your own risk assessment of our cloud services. And we do these things to help you understand how the controls within our cloud services meet the security, compliance, and privacy requirements of your organization.
Service Assurance
Many of our customers in regulated industries are subject to extensive compliance requirements. To perform their own risk assessments, customers often need in-depth information on how Office 365 maintains the security and privacy of their data. Office 365 is committed to the security and privacy of customer data in its cloud services and to earning customer trust by providing a transparent view of its operations, and easy access to independent compliance reports and assessments.
The Service Assurance area of the Security & Compliance Center provides information about how Microsoft’s cloud services maintain security, privacy and compliance with global standards. It includes independent, third-party audit reports for Office 365, Yammer, Azure, Dynamics 365, and Intune, as well as implementation and testing details for the security, privacy, and compliance controls used by Office 365 to protect Customer Data.
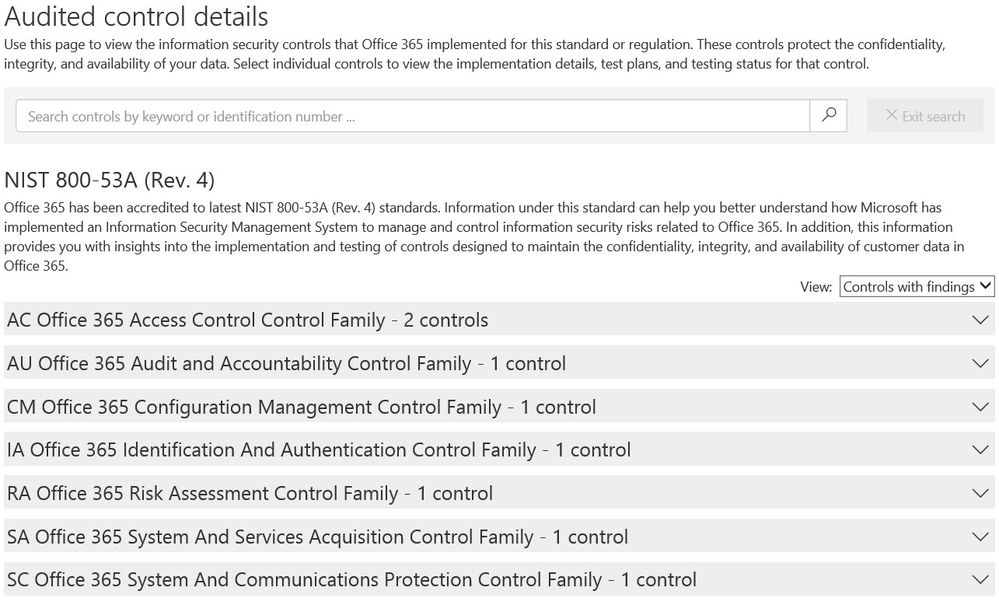
Audited Controls
The Audited Controls area of Service Assurance provides information about how the controls used within Office 365 meet security, compliance, and privacy requirements. With Audited Controls, we have mapped our internal control system to other standards, including International Organization for Standardization (ISO) 27001:2013, ISO 27018:2014, and now NIST 800-53.
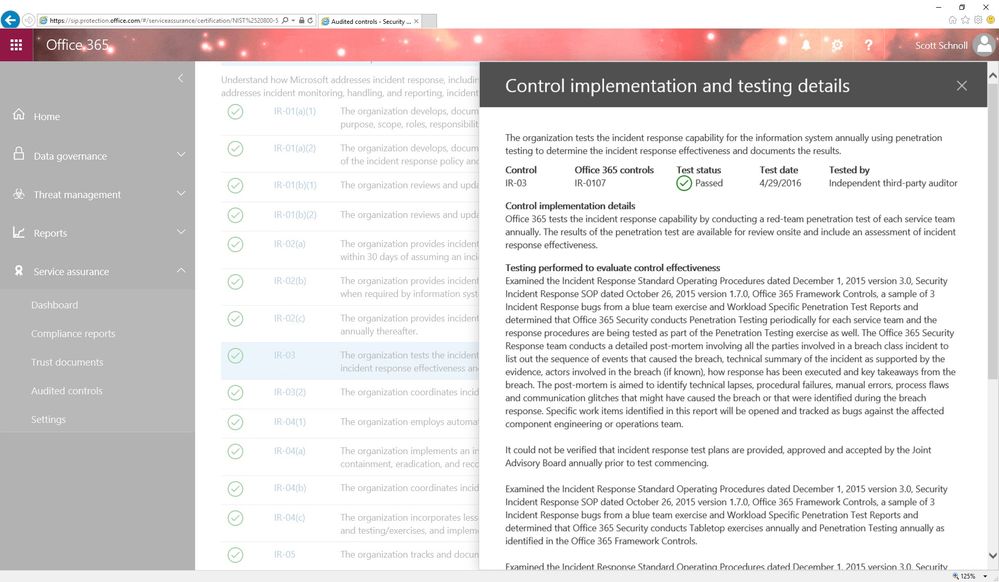
Using the Audited Controls feature, customers can perform their own assessment of the risks of using Office 365. Customers view the details of a given control, that includes:
- Control ID (as assigned by the mapped standard)
- Test status (whether the control has passed testing)
- Test date (when the control was last tested)
- Tested by (typically third-party auditors or Microsoft)
- Control implementation details (how the control is implemented)
- Testing performed to evaluate control effectiveness (how the control was tested)
- Management responses (for any findings from any audits)
Office 365 Audited Controls for NIST 800-53
Microsoft’s internal control system is based on the National Institute of Standards and Technology (NIST) special publication 800-53, and Office 365 has been accredited to latest NIST 800-53 standard as a result of an audit through the Federal Risk and Authorization Management Program (FedRAMP) using the test criteria defined in NIST 800-53A (Rev. 4).
Today, we are pleased to announce the release of the Office 365 Audited Controls for NIST 800-53. The information we have published for this standard represents the results of a third-party audit of Office 365 and can help you better understand how Microsoft has implemented an Information Security Management System to manage and control information security risks related to Office 365. In addition, this information provides you with insights into the implementation and testing of controls designed to maintain the confidentiality, integrity, and availability of Customer Data in Office 365.
The Office 365 Audited Controls for NIST 800-53 include 695 individual controls across 17 control domains:
|
Control Domain |
Intended to Help You To… |
|
Access Control |
Understand how Microsoft addresses access control policies and procedures, account management, access enforcement, information flow enforcement, separation of duties, least privilege, unsuccessful login attempts, system use notification, previous login notification, concurrent session control, session locks and termination, access control supervision and review, permitted actions without identification or authentication, automated marking, security attributes, remote and wireless access, access control for mobile devices, use of external information systems and information sharing, publicly accessible content, data mining protections, access control decisions and reference monitors for Office 365.
|
|
Awareness and Training |
Understand how Microsoft addresses security awareness and training policies and procedures for Office 365 personnel, and how Microsoft addresses role-based security, security training and security training records, and contacts with security groups and associations.
|
|
Audit and Accountability |
Understand how Microsoft addresses audit and accountability policies and procedures for Office 365, including audit events, contents of audit records, audit storage capacity, processing failures, review, analysis, reporting, reduction and protection of audit information, non-repudiation, audit generation and record retention, monitoring for information disclosure, session audits, and cross-organizational audits.
|
|
Security Assessment and Authorization |
Understand how Microsoft addresses security assessments for Office 365, including system interconnections, security certification, security authorization, continuous monitoring, penetration testing, and plans of actions and milestones.
|
|
Configuration Management |
Understand how Microsoft addresses configuration management for Office 365, including baseline configuration management, change control, security impact analysis, access restrictions for change, information system inventory, configuration management plans, and software-usage restrictions.
|
|
Contingency Planning |
Understand how Microsoft addresses contingency planning related policies and procedures for Office 365, including contingency plans, plan testing, plan updating, alternate storage and processing sites, contingency plans for telecommunications services, information system backup, recovery and reconstitution, alternate communication protocols and alternative security mechanisms.
|
|
Identification and Authentication |
Understand how Microsoft addresses identification and authentication in Office 365, including device and user identification and authentication, identifier and authentication management, cryptographic module authentication, service identification and authentication, adaptive identification and authentication, and re-authentication. |
|
Incident Response |
Understand how Microsoft addresses incident response, including policies and procedures, training, and testing in Office 365. Also understand how Microsoft addresses incident monitoring, handling, and reporting, incident response plans and assistance, and information spillage response.
|
|
Maintenance Control |
Understand how Microsoft addresses maintenance in Office 365, including policies and procedures, maintenance tools and personnel, non-local and timely maintenance.
|
|
Media Protection |
Understand how Microsoft addresses media protection in Office 365, including policies and procedures and media access, marking, storage, transport, sanitization, use, and downgrading.
|
|
Physical and Environmental Protection |
Understand how Microsoft addresses physical and environment protection for Office 365, including policies and procedures, physical access authorization, access control, access monitoring, visitor control, emergency shutoff, power, and lighting, fire and water damage protection, temperature and humidity, information leakage, and asset monitoring and tracking.
|
|
Planning |
Understand how Microsoft addresses security planning for Office 365, including system security plans and updates, rules of behavior, security-related activity planning, information security architecture, and central management.
|
|
Personnel Security |
Understand how Microsoft addresses personnel security for Office 365, including policies and procedures, personnel screening, termination, transfer, and sanctions, access agreements, and third-party personnel security.
|
|
Risk Assessment |
Understand how Microsoft addresses risk assessment for Office 365, including risk assessment planning and updates, vulnerability scanning, technical surveillance and countermeasures.
|
|
System and Services Acquisition |
Understand how Microsoft addresses system and services acquisitions for Office 365, including allocation of resources, system development lifecycle, information system documentation, supply chain protection, trustworthiness, developer configuration testing and security management, tamper resistance and detection, component authenticity, developer screening, and security engineering principles.
|
|
System and Communications Protection |
Understand how Microsoft addresses system and communications protection for Office 365, including denial-of-service and boundary protection, transmission confidentiality and integrity, cryptographic key protection, public access protection, protection of information at rest, honeypots, honey-clients, concealment and misdirection, operations security, port and I/O device access, mobile code, secure name and address resolution, and detonation chambers.
|
|
System and Information Integrity |
Understand how Microsoft addresses system and information integrity for Office 365, including flaw remediation, malicious code protection, information system monitoring, security alerts and advisories, information input handling and restrictions, error handling, memory protections, and fail-safe procedures. |
You can use the information published for this control set in two ways:
- In the Audited Controls area of the Security & Compliance Center, where you can search controls using keywords and control ID numbers, and filter controls to see only those controls that have findings.
2. You can also download the Audited Controls in Excel format and search them offline.
Accessing Service Assurance and Audited Controls
Anyone—and I mean anyone—can access Service Assurance and Audited Controls, including existing customers of Office 365 for business, new customers, and customers evaluating Microsoft online services. When you access Service Assurance for the first time, the first step is to configure your industry and regional settings. Once you have selected regions and industries, you can review and download content, including compliance reports and trust documents, and Audited Controls. For detailed steps to access Service Assurance, see Service assurance in the Office 365 Security & Compliance Center.
You can also download Audited Controls workbooks from the Compliance Guides section of the Service Trust Preview, which is available to anyone with a paid or trial tenant.
Audited Controls Roadmap
The release of the Office 365 Audited Controls for NIST 800-53 represents another milestone in our efforts to be transparent with you about how we operate our cloud services. Our upcoming journey includes work to develop and release Office 365 Audited Controls for Service Organization Controls (SOC) 2, and to develop and release Audited Controls for both Azure and Dynamics 365. In addition, we are developing tools that will allow you to upload your own control framework and map it to Microsoft’s control framework and various standards.
Tens of thousands of organizations already use Office 365 Service Assurance and have indicated that they are saving a significant amount of time in evaluating the security, privacy and compliance of Office 365. We hope you find the Office 365 Audited Controls for NIST 800-53 useful, and we look forward to your feedback.
-- Scott Schnoll, Senior Program Manager, Office 365 Customer Experience
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.

