- Home
- Microsoft 365
- Microsoft 365 Blog
- How to secure your remote workers using the Cloud Policy service
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
With more and more users working from home, organizations are facing new security and privacy challenges. One of them might be, that users are working on unmanaged, maybe personal devices accessing corporate data. Classic technologies like Active Directory Group Policy Management do not help in such scenarios, as these do not apply to unmanaged devices.
This blog post will provide guidance on how to leverage the Cloud Policy service (CPS) to address those scenarios. CPS allows an admin to target a user with policies which follow them across all devices, regardless of the way the devices are managed (if at all). We will also share some recommended security settings which might be worth considering.
Step 1 – Enable CPS
The Cloud Policy service (CPS) is a cloud-based service that enables you to apply policy settings for Microsoft 365 Apps for enterprise (formally known as Office 365 ProPlus) on a user’s device. The policy settings roam to whichever device the user signs into and uses Microsoft 365 Apps for enterprise. This applies whether the device is managed through on-premises domain devices, as a Azure AD registered, Azure AD Joined, or Hybrid Azure AD joined device.
You should start by verifying the requirements:
- Supported version of Microsoft 365 Apps for enterprise deployed
- Licensed for Microsoft 365 Apps for enterprise
- At least one Azure AD group which contains the users you're targeting.
- An admin user with at least the Office Apps Admin role assigned
- Clients must be able to reach these URLs: *.office.com, *.office.net over 443. Refer to
Office 365 URLs and IP address ranges - Microsoft 365 Enterprise | Microsoft Docs for more information.
Sign in on https://config.office.com. If you're using Intune, you can also use the Policies for Office apps blade. That’s it. No more prep work needed.
Step 2 – Create a policy configuration and assign to users
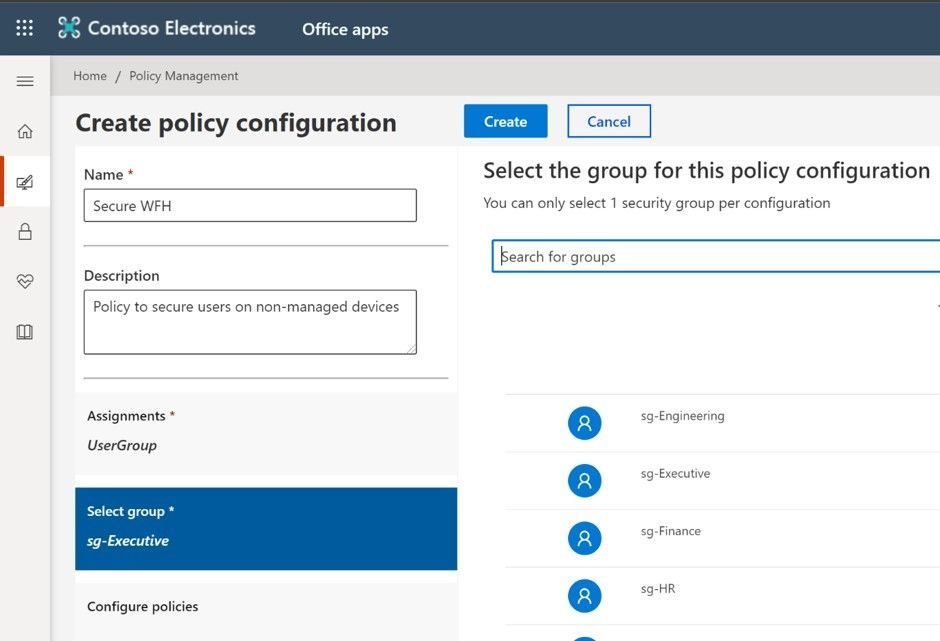
Now you should create your first policy configuration and assign it to a group of users:
- Expand the Customization node and select Policy Management
- On the Policy configurations page, choose Create and provide a name and a description (optional)
- In Assignments, choose whether this policy applies to users of locally installed Microsoft 365 Apps for enterprise, or just to users who anonymously access documents using Office for the web.
- Select the AAD-based security group that is assigned to the policy configuration. Each policy configuration can only be assigned to one group, and each group can only be assigned one policy configuration.
We also have a video ready for you which walks you through these steps.
Step 3 – Set policies
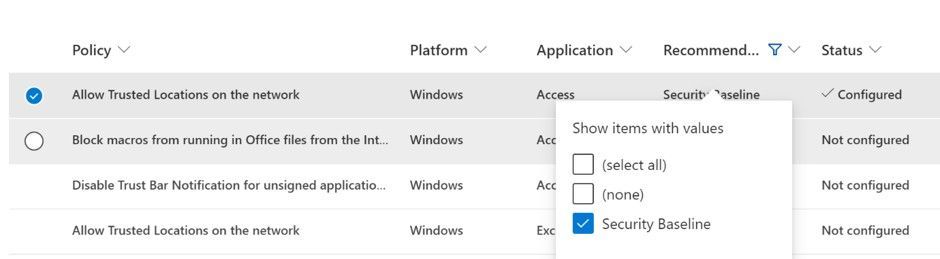
After clicking on Configure policies you can start to search for and configure policies. Please note that most policies are only applicable to Office on Windows, but some are applicable cross-platform as noted in the platform column in the policy list.
As a starting point, you can filter the Recommendation column to view the recommended Microsoft Security baseline policies. Click on each policy name to view the description and decide if you want to keep the baseline’s recommended value or manually configure it. The reviewed items will switch the Status to Configured when applied.
Especially for the scenario of remote workers, here are some policies you might want to have a closer look at:
| Policy Name | Comment |
| Block signing into Office | Can be used to prevent users from being signed in with a corporate and personal account at the same time in order to prevent data leakage to e.g. a personal OneDrive. |
| Hide file locations when opening or saving files | Setting to “Hide local PC” will discourage users from saving corporate data to the maybe non-corporate device. |
| Disable VBA for Office applications | VBA/macros are powerful tools and can help automate data processing or entry. But it is also used for malicious attacks and might be better prevented to run on non-managed/remote devices. |
| Do not open files from the Internet zone in Protected View | If set to “Disabled”, Office files downloaded from the internet will always be opened in Protected View first. |
| Set document behavior if file validation fails | Admins can enforce Protected View for files which failed validation. Those files could e.g. try to exploit Office through malformed documents. |
| Allow the use of connected experiences in Office, et al. | Admins can control if Office is allowed to leverage cloud services for downloading and analyzing content. Review documentation for available controls. |
| Force Runtime AV Scan | If enabled, all files opened by Office will be passed to the installed AV engine for scanning. |
| Use Cached Exchange Mode for new and existing Outlook profiles | You can use this policy to enforce Online Mode for Exchange in order to prevent users from syncing down their inbox content to a maybe insecure device. Note that this setting will apply to all devices the user is signing into. |
| Block all unmanaged add-ins | This setting allows you to block all add-ins from being loaded by Office. |
Step 4 – Additional considerations
As policies configured through CPS are following the user across all devices, it is not limited to remote workers or users on un-managed devices. You should consider folding your on-prem policies into CPS policies and go forward with a single solution for both on-prem as well as off-prem users.
If multiple sets of policies are applied to a user/device, Office will evaluate the applicable settings following these rules:
- Winning configuration is evaluated per individual setting, not per object.
- CPS policies win over AD-based settings.
- If multiple CPS policies are applied, the priority configured in the CPS service is applied.
Overview of blog post series
This post is part of a series which is covering different stages and phases in the Office lifecycle in remote worker/work from home scenarios. The others are:
- How to upgrade from legacy to Microsoft 365 Apps for remote workers using VPN
- Configuring Microsoft 365 Apps updates for remote workers using VPN
- Maintaining installations in terms of adding e.g. Project, Visio or additional Language Packs for re...
We hope this will help you to minimize the impact of deploying, servicing and managing Microsoft 365 Apps for enterprise on your own network and your user’s VPN connections.
FAQ
Q: Am I secure after enabling OCPS and setting the Microsoft recommended policies?
A: “Being secure” is a relative state where you can try to achieve a high bar, but basically never be 100% secure. Using OCPS is one building block in a broader strategy to secure remote workers. In addition make sure to review Azure Multi-Factor Authentication, Azure Conditional Access and the user’s sign-in risk assessment to further protect the user’s identity. For guidance on protecting your corporate data, please review Azure Information Protection.
Q: I’ve got issues with OCPS, how can I troubleshoot the service?
A: We got you covered, please review Troubleshooting OCPS on Windows.
Q: Can I fully secure a device not owned by my organization?
A: There are limits on how secure a device that you don’t own or manage can be. Each employed security technology raises the bar for an attack/exploit on the device/user/data successfully, but unless you fully manage the device there is a risk to your data. Security is sometimes not about secure/not secure, but more about the right level of security for a given scenario. You can use Intune to manage devices that you don’t own.
Q: Can I also secure and control Office on iOS or Android using OCPS?
A: While some policies also apply to Office on Android or iOS, there are more advanced controls available through Intune Application policies. These allow you to e.g. enforce a PIN, local data encryption of cloud-only storage of data for the Office apps on mobile devices.
Q: We’re an Intune shop, can I also use Intune to manage OCPS policies?
A: Sure thing. You can manage the Policies for Office apps from the Intune portal as well.
Q: Can we use OCPS to block syncing OneDrive for Business content on devices which aren’t managed?
A: No. However, we can address this concern by having your Office 365 tenant administrator running Set-SPOTenantSyncClientRestriction cmdlet. This permits adding restrictions on whether users can sync items to non-domain joined machines.
The Authors
This blog post is brought to you by the Microsoft 365 Apps for enterprise Ranger Team at Microsoft. Feel free to share your questions and feedback in the comments below.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.