- Home
- Microsoft 365
- Microsoft 365 Blog
- Getting the best connectivity and performance in Office 365
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Traditional enterprise networks are designed primarily to provide users access to applications and data hosted in company operated datacenters. A secondary use has been as a gateway for access to the Internet for communications and web browsing. In this model, there is minimal or no network security between users and the company operated datacenters, and a substantial security perimeter between users and the Internet with many network devices such as firewalls, anti-virus scanners, data loss prevention, and intrusion detection devices.
Because of the large network security stack, Internet connectivity for branch offices is commonly centralized and backhauled over the customer’s wide area network (WAN). This model worked well for secure access from users within the office to corporate on-premises apps such as email and document sharing where bandwidth could be assured, and minimal network security within the WAN meant network traffic was not impeded.
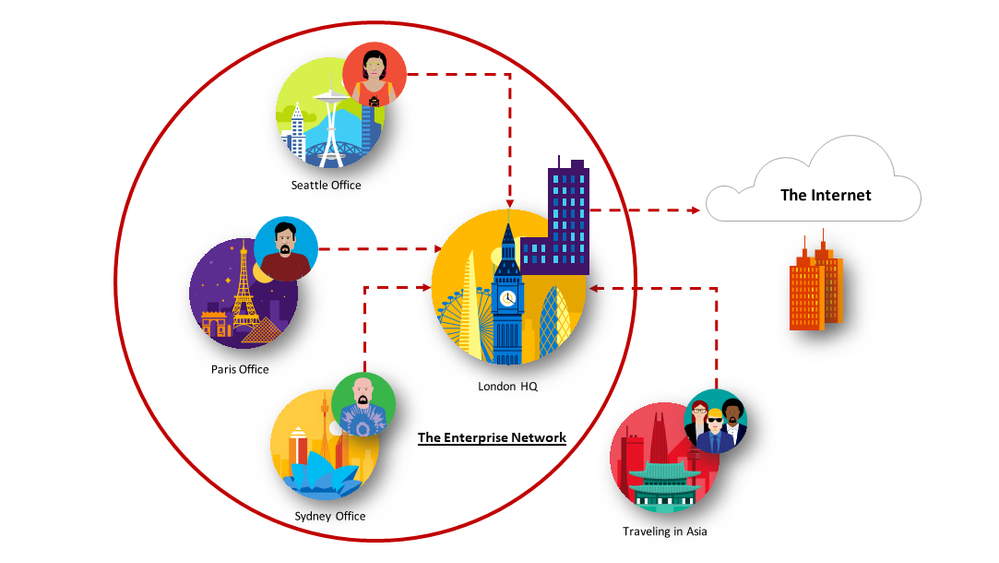
As enterprise adoption and reliance on SaaS apps like Office 365 continues to grow, and as employees work from more varied locations, the old methods of backhauling traffic to a central location for inspection creates latency and leads to a poor end user experience. The shift from accessing enterprise applications in a customer operated central datacenter to Office 365, and the differences in traffic patterns, performance requirements, and endpoint security needs to be acknowledged and planned differently when compared with simple Internet communications and web browsing research connectivity.
The Microsoft global network and Office 365
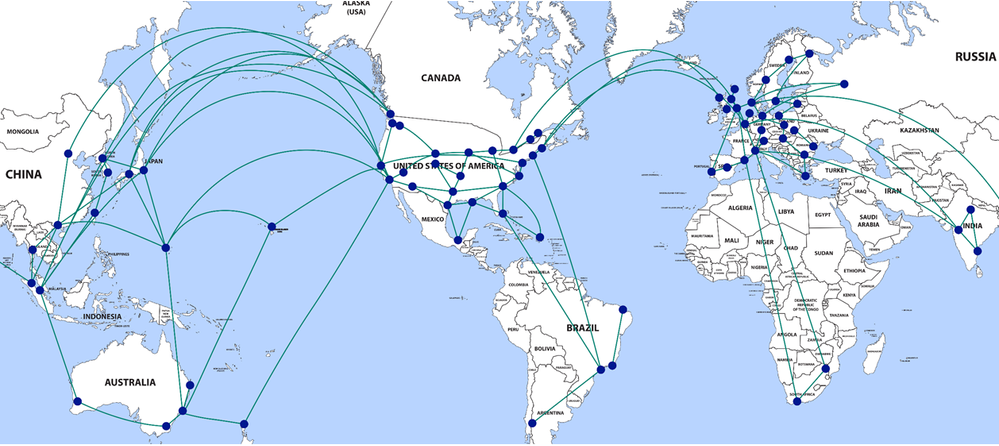
The Microsoft global network is one of the largest network backbones in the world consisting of high bandwidth links that have minimal network congestion, with thousands of miles of privately owned dark fiber, multi-terabit network connections between datacentres, and application front doors servers spread around the world. Over 100 public Internet peering interconnection locations on this network makes it easy for all users, regardless of location, to connect into the network using the Internet and access services such as Office 365, Azure, Xbox, Bing, Skype, Hotmail and more.
Microsoft continues to invest in the network, the geographical locations of the application front doors, public peering partnerships with ISP’s, and traffic backhauling capabilities. This allows user network traffic to enter the Microsoft global network very close to the user, and then the traffic is backhauled at Microsoft’s cost over high bandwidth lines within the network to the location where the user’s data is stored.
Office 365 connectivity principles
Microsoft recommends using the Internet and a simple network design for optimal connectivity and performance in Office 365. A key goal in the network design should be reducing the round-trip time (RTT) from your network into the Microsoft global network and ensure that the network traffic is not hair pinned or centralized to specific locations. Use the Office 365 connectivity principles to manage your traffic and get the best performance when connecting to Office 365.
1. Identify and differentiate Office 365 traffic using Microsoft published endpoints
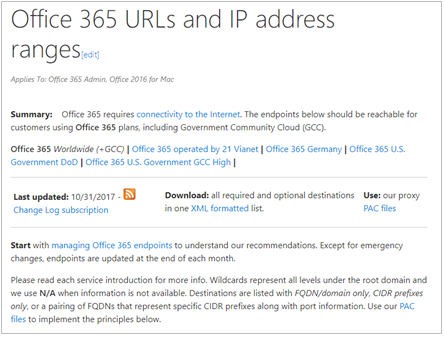
Identifying Office 365 network traffic is the first step in being able to differentiate that traffic from generic Internet-bound network traffic. Microsoft publishes the Office 365 endpoints and guidance on how best to use this data. An Office 365 administrator can use a script to fetch the endpoint details and apply it to a perimeter firewall and other network devices. This will ensure that traffic bound for Office 365 is identified, treated appropriately and managed differently to network traffic bound for generic and often unknown Internet web sites that employees may browse. See the Office 365 endpoint categories and Office 365 IP Address and URL web service to automate endpoint management.
2. Egress Office 365 data connections as close to the user as practical with matching DNS resolution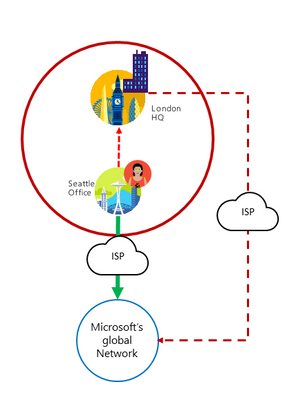
When compared to backhauling data across the corporate WAN, the user is most likely going to get better performance by egressing Office 365 network traffic to the Internet close to their location where it can be connected to Microsoft’s global network. Additionally, many Office 365 applications use DNS requests to determine the user’s geographic location. If the users DNS lookups are not done at the same point as the network egress the user may be directed to a distant Office 365 front end server.
By providing users with local Internet egress and local DNS resolution their network traffic destined for Office 365 can connect to Microsoft’s global network and Office 365 front end servers as close as possible to the user. Shortening the network path to Microsoft’s global network and to Office 365 front end servers in this way should be expected to improve connectivity performance and the end user experience in Office 365.
3. Avoid network hairpins and optimize connectivity directly into the nearest entry point into Microsoft's global network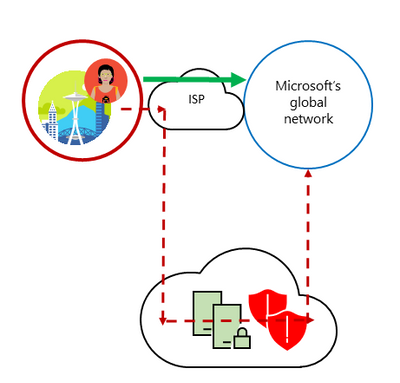
As discussed, the second type can result from a cloud based network security infrastructure device. If the network device vendor has limited hosting locations and directs a user to a specific one that is distant from them they may create a hairpin route where network traffic goes from the user to the distant network device and back to an Office 365 front end server that is near the user. This can be avoided by asking cloud based network security vendors about the specific locations of their hosting and being critical of the network paths that this creates that may be different to the direct route to Office 365 endpoints on Microsoft’s global network.
The first type results from misaligned network egress and DNS lookups for a user. This can result in the user being directed to an Office 365 front end server that is close to them, but via a distant corporate egress location at a head office. This can be avoided by local egress and local DNS as outlined in the principle above.
4. Assess bypassing proxies, traffic inspection devices and duplicate security which is available in Office 365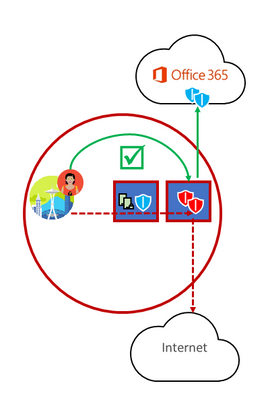
Generic Internet web browsing traffic to unknown Internet sites can have substantial security risk and most enterprises implement network security, monitoring, and traffic evaluation technology at their Internet egress locations. Network security technology includes proxy servers, inline SSL break and inspect of network traffic, network layer based data loss prevention, and more. Network security devices is a strongly growing industry. Unfortunately, whilst all this equipment reduces the enterprise risk of Internet connectivity, it also increases the cost and resources required for Internet connectivity, and it reduces the performance for network connections.
Office 365 servers are all hosted in Microsoft datacenters and Microsoft is very transparent about datacenter security, operational security and risk reduction around those servers and the network endpoints that they represent. These security details can be found in the Microsoft Trust Center. Office 365 also has many other methods available for reducing that network security risk including the built-in security features in Office 365 such as, Data Loss Prevention, Anti-Virus, Multi-Factor Authentication, Customer Lock Box, Advanced Threat Protection, Office 365 Threat Intelligence, Office 365 Secure Score, Exchange Online Protection, Network DDOS Security, and other many other security features.
Enterprise customers should review these risk reduction methods specifically for Office 365 bound traffic and use the Office 365 in-built security features to reduce the reliance on intrusive, performance impacting, and expensive network layer security technologies for network traffic that is identified as Office 365.
The Office 365 networking product group would like to learn about your networking challenges when connecting to Office 365. Please comment on this blog to start a conversation.
Resources
- Office 365 Connectivity Principles in greater detail: https://aka.ms/PNC
- Office 365 product group videos expanding on the Office 365 connectivity principles:
- Strategy: https://youtu.be/19a8s90HboQ
- Planning: https://youtu.be/cJDpB59gk3M
- Implementation: https://youtu.be/lZwvitkvg6A
- Guidance on network planning and perf tuning in Office 365: aka.ms/tune
- Office 365 URLs and IP addresses: aka.ms/O365IP
- Managing bandwidth requirements for Office 365: aka.ms/O365networkconnectivity
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.