- Home
- Microsoft 365
- Microsoft 365 Blog
- Big Updates to Office 365 Identity
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
At Microsoft, we understand that ideas aren’t formed in a vacuum. Office 365 is designed to allow users to engage and collaborate with employees and trusted partners inside and outside your organization. In this cloud-first world, effective identity management is the key to enabling secure, mobile, productive working scenarios.
Over the past months, we’ve made some big updates to Azure Active Directory (Azure AD) that will enable a number of important new scenarios for Office 365 customers. We’re really excited by the possibilities these new features will bring to Office 365 administrators and users. To learn more, join us for a live webcast on March 7 where we’ll cover what’s new in Azure AD and dive into our latest B2B collaboration features!
Pass-through Authentication and Seamless Single Sign-on reach Public Preview!
When we talk to organizations about how they want to augment their identity in the cloud, we hear a recurring set of priorities:
- Single sign on for all users
- Keep passwords on-premises
- Make it super easy!
That’s where pass-through authentication and seamless single sign-on are game changers! Azure AD pass-through authentication provides a simple, secure, and scalable model for validation of passwords against your on-premises Active Directory via a simple connector deployed in the on-premises environment. User passwords are validated against your on-premises Active Directory, without needing to deploy ADFS servers!
Furthermore, with the new single sign-on additions in Azure AD Connect you can enable seamless single sign-on for your corporate users (users on domain joined machines on the corporate network). In doing so, users are securely authenticated with Kerberos, just like they would be to other domain-joined resources, without needing to type passwords.
Download the latest version of Azure AD Connect now to get these new capabilities! You’ll find the new options in a custom install for new deployments, or, for existing deployments, when you change your sign-in method.
As with all previews there are some limits to what we currently support. We are working hard to ensure we provide full support across all systems. You can find the full list of supported client and operating systems in the documentation, which we’ll be updating consistently as things change.
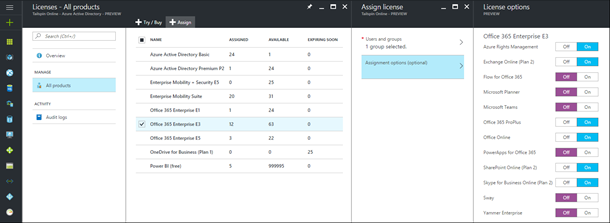
Group-based license management for Office 365 (and more)
One of the top requests we hear from Azure AD and Office 365 customers is for richer tools to manage licenses for Microsoft Online Services like Office 365 and the Enterprise Mobility + Security. Admins need easier tools to control who gets a product license and which services are enabled.
Recently, we announced the public preview of a much-anticipated new capability in Azure AD: group-based license management! With this new feature, you can define a “license template” and assign it to a security group in Azure AD. Azure AD will automatically assign and remove licenses as users join and leave the group.
This preview also includes the highly-requested ability to selectively disable service components in product licenses, making it possible to stage the deployment of larger suites like Office 365 E5. While group-based license management is in public preview you will need an active subscription for Azure AD Basic (or above) in your tenant to assign licenses to groups. If you don’t have one, just sign up for an Enterprise Mobility + Security trial. Later, when this functionality becomes generally available it will be included for free in Office 365 Enterprise E3 and other enterprise products. Look out for more information on this very soon!
You can find more details about Group-based Licensing and the preview period limitations in our documentation.
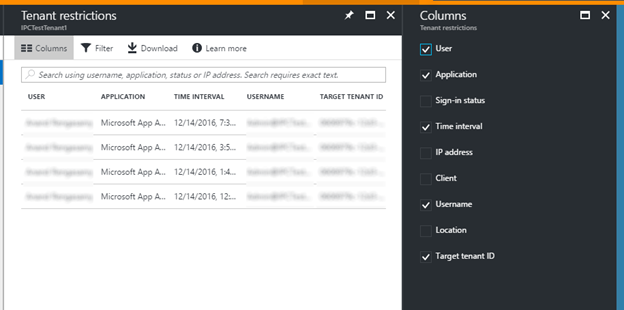
Tenant Restrictions is now Generally Available
Certain organizations choose to restrict Internet destinations by filtering on Fully Qualified Domain Names (FQDNs) and/or IP addresses using proxy and/or firewall devices. However, this approach is not effective in a world where SaaS applications are hosted in a public cloud, running on shared FQDNs such as outlook.office.com (Outlook on the Web) and login.microsoftonline.com (Azure AD). Blocking these FQDNs would effectively block access to every instance of the service, including the organization's.
The new tenant restrictions feature enables organizations to control access to SaaS cloud applications, based on the Azure AD tenant the applications use for single sign-on. For example, you may want to allow access to your organization’s Office 365 applications, while preventing access to other organizations’ Office 365 applications.
Tenant Restriction is a new feature being introduced to Azure AD Premium P1 subscribers and all Office 365 customers. To make use of this feature, Office 365 subscribers must enable Modern Authentication as the default authentication protocol for the cloud service and access the service using a Modern Authentication enabled client. When you’re ready to get started, see Use Tenant Restrictions to manage access to SaaS cloud applications for more information.
Certificate Based Authentication is Generally Available
In December we announced that Certificate-Based Authentication (CBA) for Exchange Online reached general availability for customers on Office 365 Enterprise, Business, Education, and Government plans. On-premises Exchange environments traditionally use CBA to enable authentication by AAD with a client certificate on Windows, Android or iOS devices when connecting to:
- Office mobile applications such as Microsoft Outlook and Microsoft Word
- Exchange ActiveSync (EAS) clients
Configuring this feature eliminates the need to enter a username and password combination into certain mail and Microsoft Office applications on your mobile device. This feature is only available in preview for Office 365 US Government Defense and Federal plans with general availability later this year. For more information visit the Azure Active Directory documentation.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.