- Home
- Microsoft Teams
- Microsoft Teams
- Re: View users assigned to an App Setup Policy
View users assigned to an App Setup Policy
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 03 2020 04:38 AM
Hi everyone
I have created a custom app setup policy to allow a subset of users to allow the upload of custom apps. This is working fine but as I'm adding more users I need an easy way to see everyone who has been assigned this policy. If I click Manage Users on the policy this only gives me the option to add new users and I can't see who is currently assigned:
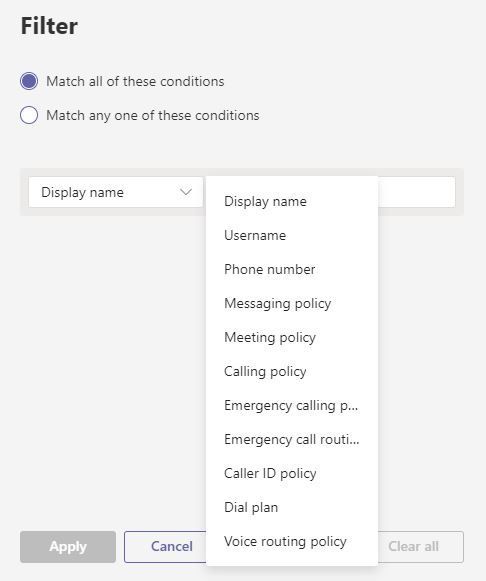
I thought I could use the filter in the Users section of the Teams admin portal but although this has some options to show certain policies, it doesn't include app setup policies:
At the moment the only way I can see who is in my custom policy is by going into their user details in the Teams admin portal and then viewing the policies assigned to them. This means that as I add more users I'll need to keep a manual list as I won't be able to remember everyone who gets added.
I'm hoping I'm just missing a simple way of viewing this information, as I can't seem to find a way of viewing it either using the UI or PowerShell? I thought I could use Get-CsTeamsAppSetupPolicy but according to this link this shouldn't be used at the moment? Any help would be gratefully received.
- Labels:
-
Administrator
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 03 2020 05:01 AM - edited Jul 03 2020 05:27 AM
Solution@gcjuw84 Hey, just use it anyway. It won't break anything :)
You can use the Get-CsOnlineUser cmdlet by the way.
e.g. Get-CsOnlineUser-Filter {teamsappsetuppolicy -eq "enterpolicynamehere"} but you'd probably want to adjust it to get a clean result and to fit your requirements.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 14 2022 07:10 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 28 2023 03:15 AM
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 03 2020 05:01 AM - edited Jul 03 2020 05:27 AM
Solution@gcjuw84 Hey, just use it anyway. It won't break anything :)
You can use the Get-CsOnlineUser cmdlet by the way.
e.g. Get-CsOnlineUser-Filter {teamsappsetuppolicy -eq "enterpolicynamehere"} but you'd probably want to adjust it to get a clean result and to fit your requirements.