- Home
- Microsoft Teams
- Microsoft Teams Community Blog
- Microsoft Ignite Live Blog: BRK219H – M365 Governance and Security Practices, Teams, Viva, and Loop
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This is a session recap from BRK219H – Governance & Security Practices for Microsoft 365, including Microsoft Teams, Viva and Loop Guidance… at Microsoft Ignite 2022
Speakers: Karuana Gatimu, John Gruszcyk
Thirteenth of October: It´s the end of the second day of #msignite in the Washington Convention Center in Seattle. In front of a breakout room is a very long row of attendees, and they are waiting to get in the room for the session with Karuana Gatimu and John Gruszcyk about Governance and Security Practices for Microsoft 365. Some attendees in line are discussing B2B direct identities and the expiring policy of Microsoft Teams.
After a few minutes, the room is full of people, and the session starts.
The session begins with an introduction and reasons why Governance and Security are so important for Microsoft 365. Karuana is telling us more about Governance in Microsoft 365 Groups. Frictionless, managed governance, for Microsoft 365 Groups is essential to provide a seamless collaboration and communications experience that your employees will love. Leveraging the capabilities of Microsoft 365 will ensure that your data is safe and well managed by your IT professionals.
This is the central link : https://aka.ms/TeamworkGovernance
The on-demand session is recorded with transcription along with a translation in sign language, which was used by some attendees in the room.
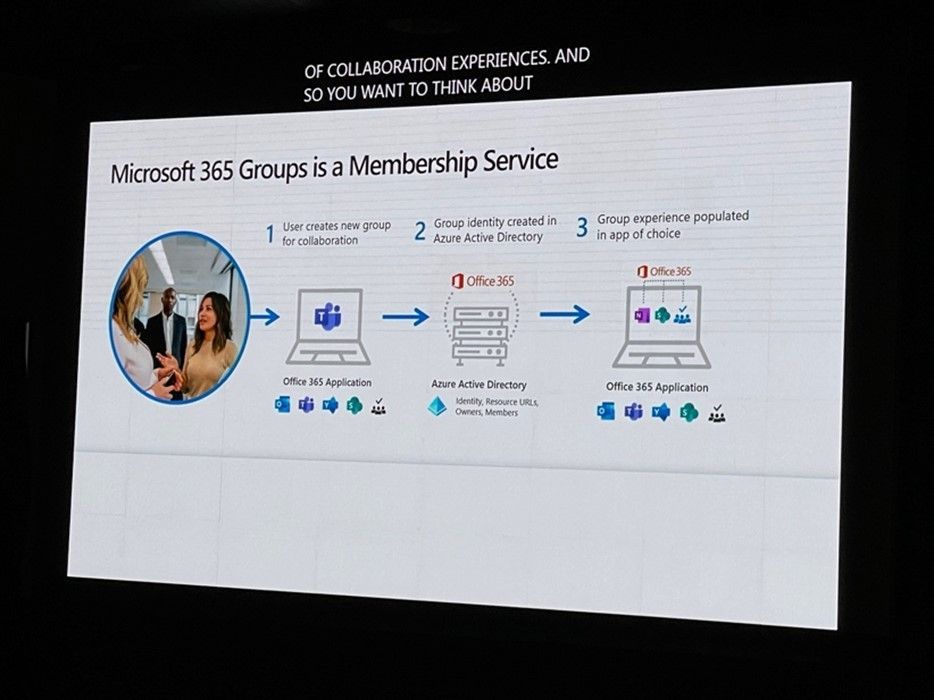
In the next topic, Karuana talks about the Microsoft 365 Group as a Membership Service in Microsoft 365. The Group is the basement of a Team as a Membership Service across the Office 365 Applications with Azure Active Directory in the backend. Members of a Group have access to a shared Mailbox, to the Group site in SharePoint Online, to Planner and as an Upgrade to Teams Groups and Yammer Communities.
Moreover, Karuana discusses the What’s New blog and what changed in the last years with the Pandemic—what is different now. She explains the new world of hybrid world scenarios and that people also work with their private or business devices at their homes or cafés. They use laptops and phones outside of the company building as the result of Microsoft 365 Groups with Zero Trust, enrollment of devices, and the journey of hybrid work.
Furthermore, Karuana talks about using Microsoft 365 Groups to fulfill the requirements of the changing times, where you can work at the same time, same place, but in different time zones.
Microsoft 365 Groups are the solution for this work model, but she sees customers make some mistakes. One example is the Prefix in the Group naming. Since the work is flexible today and there are no silos like departments, please stop using the department Prefix.
We can see Best Practices in the next slide:
This is the Microsoft Stack of using Microsoft 365 Groups to fulfill the requirements where people work everywhere and outside of the Company Building.
Control is the key!
The control comes with Microsoft 365 Groups. The Membership of a Group defines different topics, so that only the people with a Membership have file access to the SharePoint backend. Moreover, there are Guest Policies to prevent Guest invites, or in a lifecycle of a group, these Invites are possible in a new situation. In this topic, it´s possible to control who can add guests to a Team.
In an example of a marketing department, shared Channels will be more important than ever. They can use these new Channels to add people from other companies into a team in a separate channel without adding them into the team. The External B2B direct user does not need to switch the tenant and can work with the company marketing team together.
We are bringing the Group Experience to a company level, which also means we need different Policies for different situations. There is not a one size fits all policy, but there are options like Teams Group Templates and Microsoft Purview Information Protection Labels for Groups. These help organize and bring the right policies to the people who need them.
In the next part of the Session John start with his demo.
He shows the Azure Active Directory (AAD) Admin Center to explain the security defaults. It´s the recommendation to activate them, and with them, the Multi Factor Authentication (MFA) for internal and external people. In the combination with the MFA App, it´s easy to implement and use MFA to protect identities and the company itself.
AAD brings more, such as Conditional Access and Zero Trust principles, into the company. He asks about who of the attendees are using Conditional Access and nearly 80% raise their hand. It´s amazing.
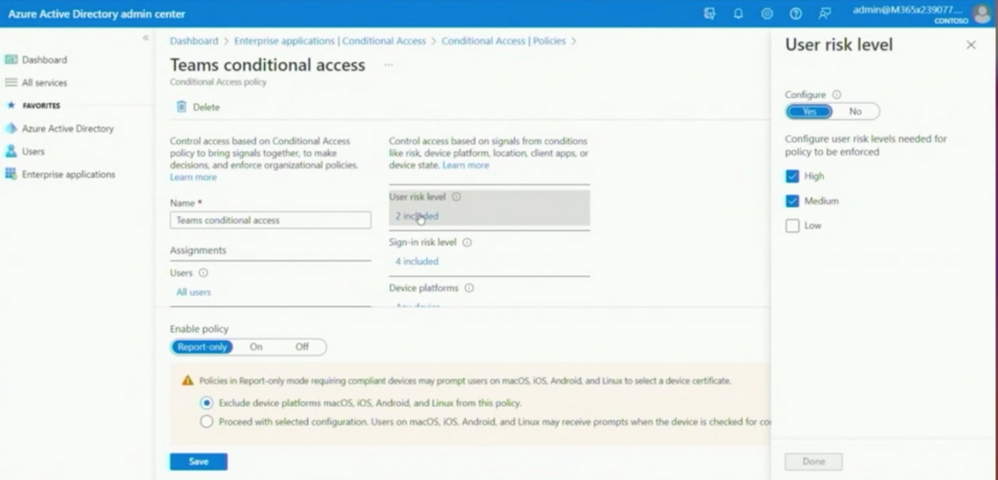
In the following, John explains the new Teams Conditional Access options. It´s a recommendation to use them to protect Teams; for example, having the user risk level set to High and Medium to block risky Identities, like Microsoft does.
Hint: test policies in a Microsoft 365 test tenant
It´s also a recommendation to test all of these policies and rules before they are implemented into the production environment. John has 5 different Test tenants to test all settings and features in different rings.
Furthermore, Access Governance is one of the main topics John explains to control the work with other organizations. While he could explain 12 hours about this topic, in this session, he will show the important ones.
B2B direct are the new External Identities to use with shared channels. To use them, the administrator configures policies and rules after the addition of the external tenant.
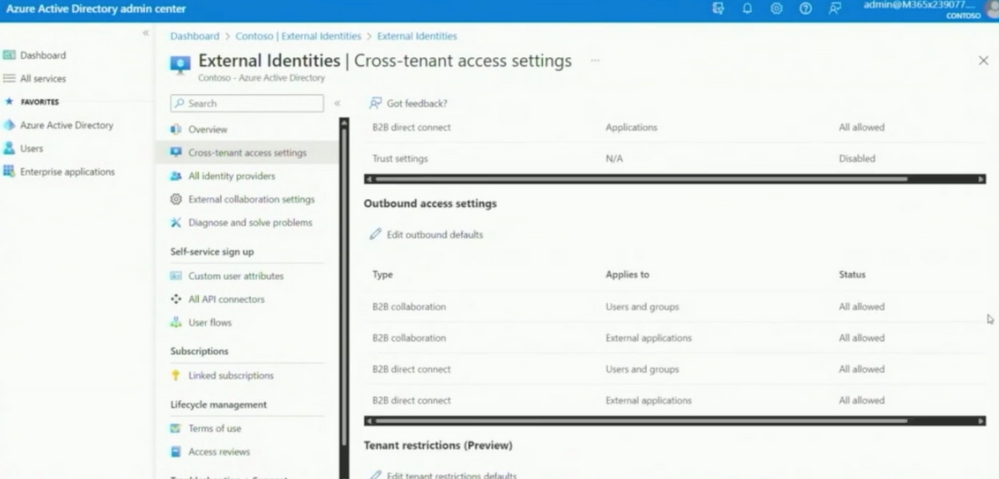
Here in the screenshot above, you see the Cross-tenant-Access Settings in Johns tenant. It´s recommended to start with a high restricted one—preventing availability of collaboration, and open these federations, groups and users, who can collaborate. In this result, you can define who can invite and have access to your groups and data.
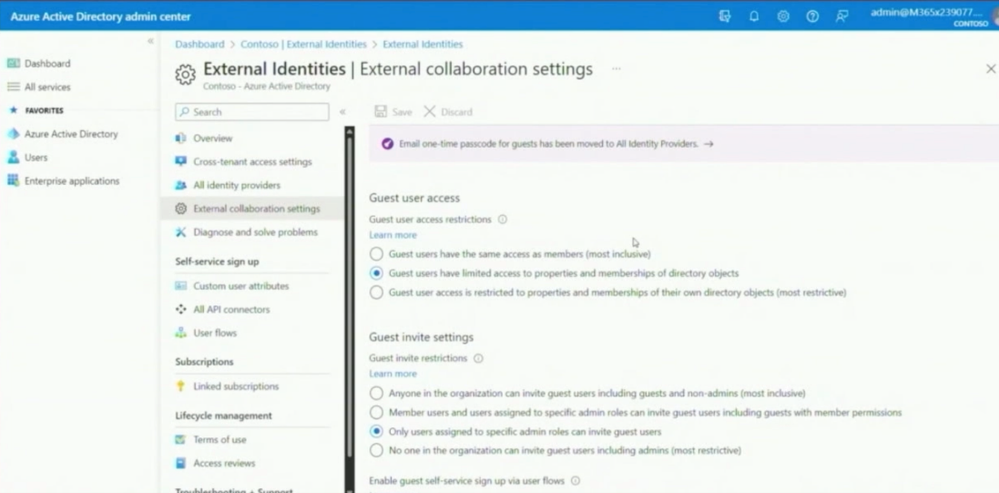
Microsoft itself is very strict in this configuration with External collaboration. John shows us the test tenant and the External collaboration settings.
In this result it´s hard to find the right setting. This must be a decision of the leaders of the different departments with IT, SecOps, and Legal. He does not recommend changing the setting often, but the middle way is often the best way to use.
The decision must consider the risk level of the data and that it is in the Microsoft 365 environment. John sees that customers also have very strict settings.
Collaboration is very important
He switches to the Microsoft Teams admin center to show the Guest and External options.
External Sharing is a recommendation and is activated in the most tenants, but there are restrictions—such as on the domain level.
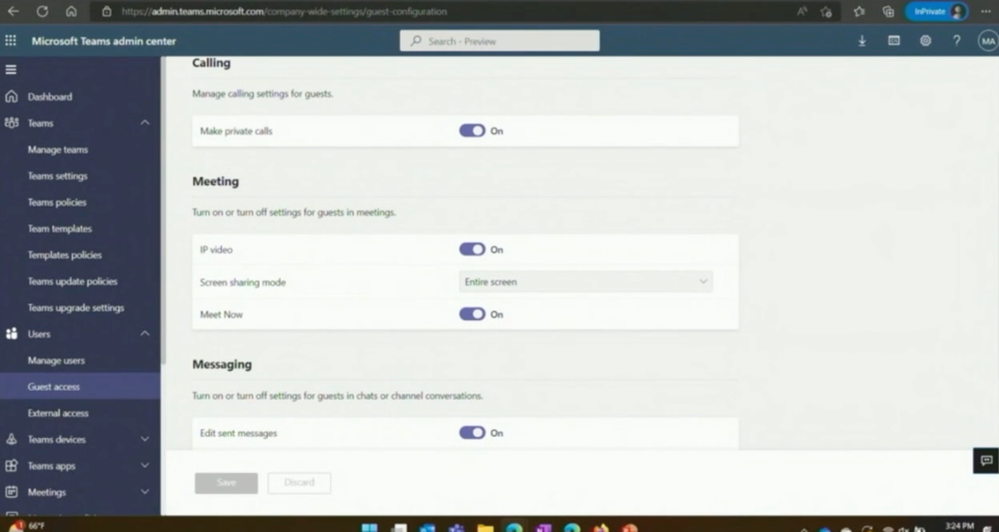
Moreover, he explains detailed restrictions and settings in the Guest Access Settings.
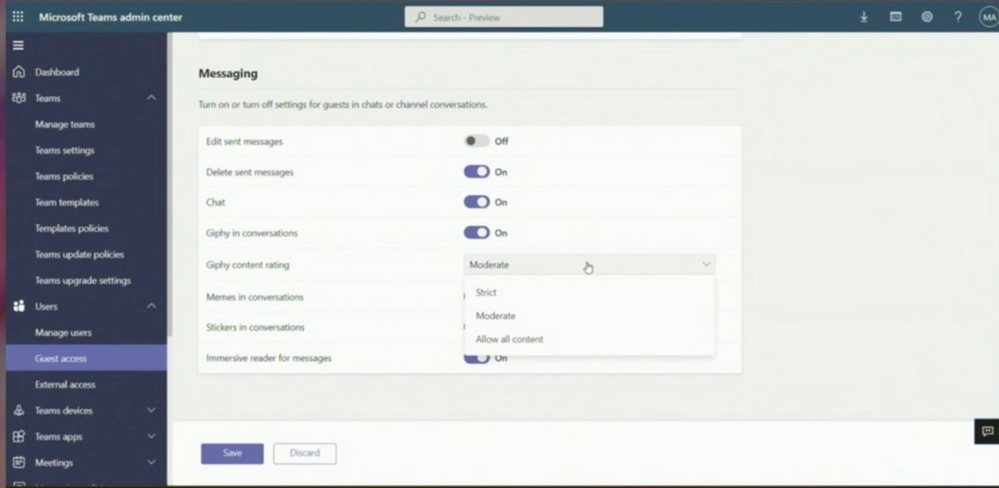
Because guests must be controlled in their own tenant, they may only be given the rights that they absolutely need. This means, for example, that guests cannot delete their messages in the Microsoft tenant. There are many different settings for this in the messaging area alone:
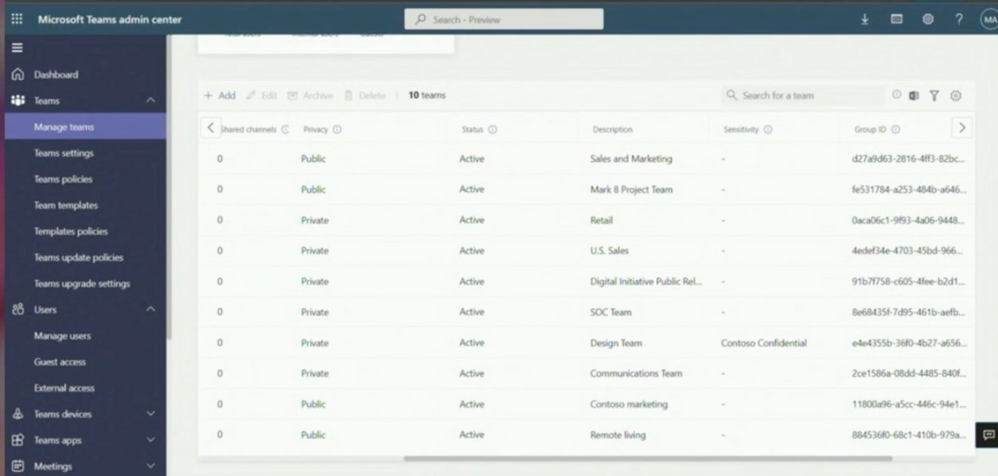
Labels for teams provide another level of control. These can also be viewed in the Manage Teams area. All that is required is that the column is shown. This is used to protect teams with sensitive data and in the area of data protection.
Many customers also use this in the area of provisioning because no one should wait for a team. From experience, this provokes only shadow IT and other ways that users find to collaborate quickly. You can find a governance solution with labels for teams and groups to make teams available quickly while enforcing rules accordingly. This even works in conjunction with conditional access policies.
Microsoft Loop is the next topic in the session. Microsoft Loop is a Collaboration container, which can be used in Teams Chat, Outlook, Mail, and on Websites in the future. Here, Governance is also an important topic and using Governance principles in Microsoft Loop is easy. You have to know that these will come from OneDrive and SharePoint Online.
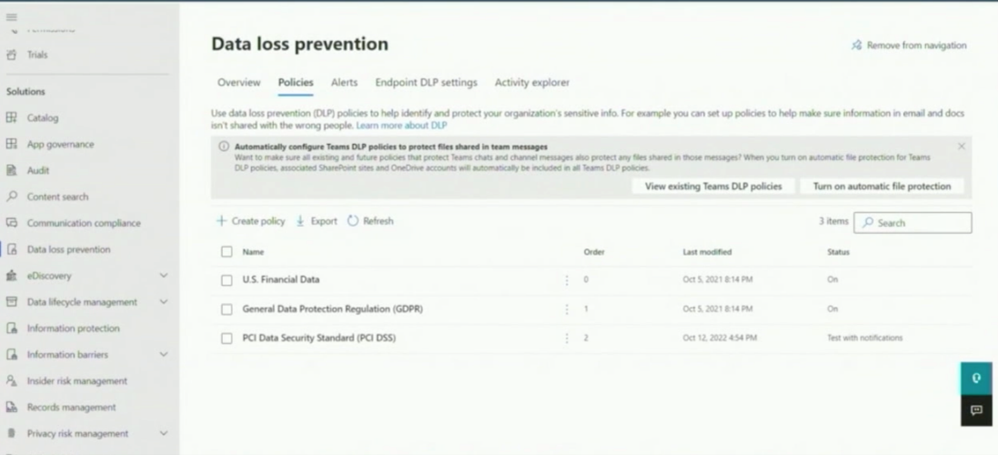
Viva and Loop are using the functionality, which is implemented today like DLP.
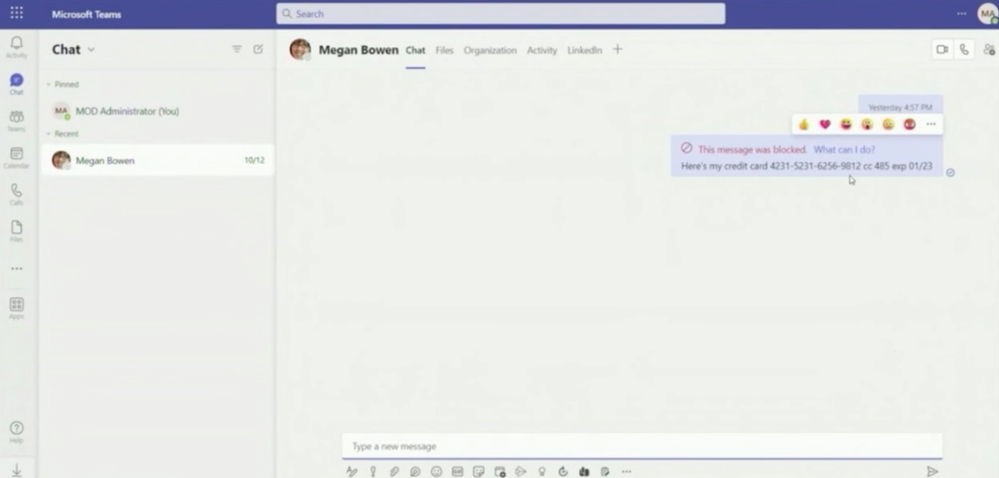
DLP also works in Teams Chats.
John shows us that it´s not possible to post a credit card number. The user receives an information pop-up, and the compliance admin will too.
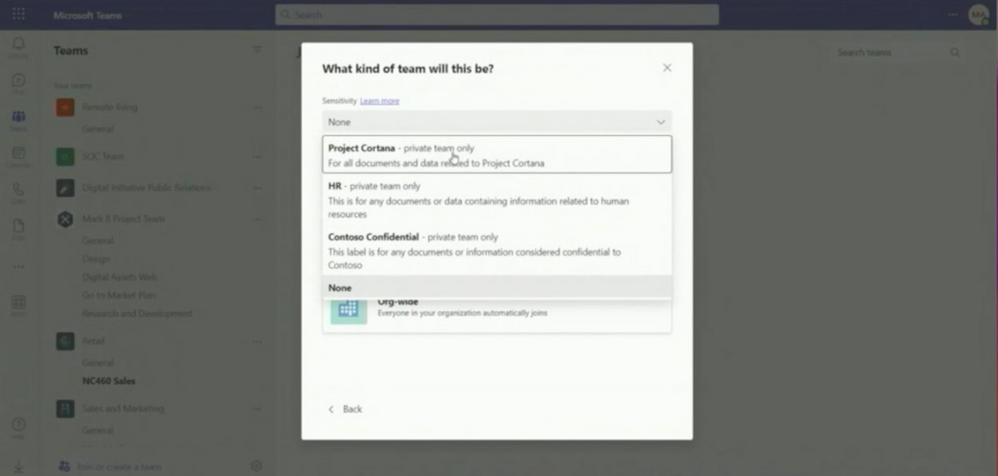
In addition to DLP, Labeling brings you the Governance you need. He explains that before showing us the automation behind the Container Label, you create a new team.
This is only possible when Labels are activated and combined with SharePoint Online. After choosing a label, this uses a short PowerShell Script, and then you can create Teams, SharePoint Sites, or Yammer Communities. The label gives the parameter of which team can be created.
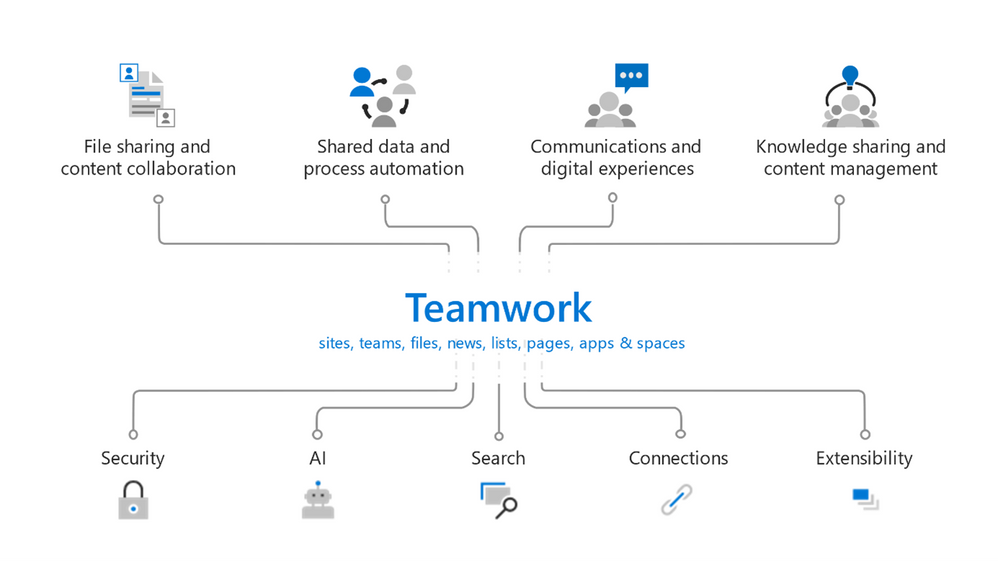
In the end, Teamwork is the key along with the roles and needs of people in the departments. Then they explain the Teamwork model.
We must understand the options for guided self-service provisioning, classification, reporting, auditing, and lifecycle management that will impact Microsoft Teams, Microsoft Viva, Microsoft Loop, Planner, and other Microsoft 365 services. This session has a special focus on recent capability updates and includes guidance for team/channel configuration and management.
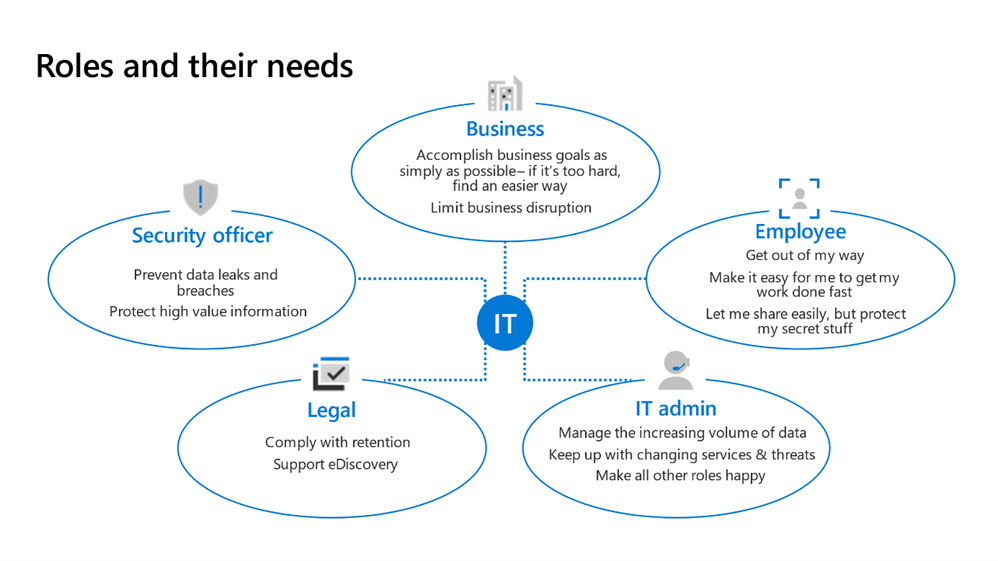
And finally, we must understand the Roles and their needs for the Governance toolset in Microsoft 365.
Thank you very much for the session Karuana and John!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.