- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Updating existing ThreatIndicator
Updating existing ThreatIndicator
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 25 2022 06:29 AM
Hi all,
Has anyone had any success with updating an existing ThreatIndicator via REST?
Threat Intelligence Indicator - Create - REST API (Azure Sentinel) | Microsoft Docs
Creating an indicator is fine:
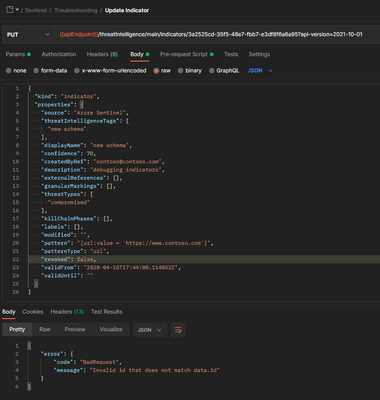
But when I try to update it using the same name/id and the example RequestBody in the docs:
From what I understand data.id is the ARM id for the indicator
https://management.azure.com/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.OperationalInsights/workspaces/{workspaceName}/providers/Microsoft.SecurityInsights/threatIntelligence/{name}
but neither id, nor data.id are required parameters in the request.body
I get the feeling I've been looking at this so long I've missed something obvious...any ideas?
- Labels:
-
APIs
-
Automation
-
SIEM
-
Threat Intelligence
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 25 2022 07:05 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 25 2022 07:46 AM
I wish that was the case!
I store the baseUri, sub, rg, and workspace as an Environment variable in Postman and the requests have a pre-request script run that concats these and populates the {{apiEndpoint}} variable:
let baseUri = pm.environment.get("baseUri");
let subscriptionId = pm.environment.get("subscriptionId") ;
let resourceGroupName = pm.environment.get("resourceGroupName");
let workspaceName = pm.environment.get("workspaceName");
uri = baseUri+"/subscriptions/"+subscriptionId+"/resourceGroups/"+resourceGroupName+"/providers/Microsoft.OperationalInsights/workspaces/"+workspaceName+"/providers/Microsoft.SecurityInsights";
pm.environment.set("apiEndpoint", uri);
So the {{apiEndpoint}} that was used for the POST request to create the indicator is the same as the one being used to PUT the update, as well as in other calls to Sentinel.
To sanity check it though I can confirm that it's being populated as:
So in the example the request really should just be a
PUT request to {{apiEndpoint}}/threatIntelligence/main/indicators/3a2525cd-35f5-48e7-fbb7-e3df8f6a6a95?api-version=2021-10-01 with my request.body
Sentinel allows indicators to use values/patterns it already knows about, and there's lots of overlap between various OSINT feeds, so I was hoping to create my own input validation using something like
the externalId or externalRef bound to the UUID in MISP or whatever to prevent duplication and just update/refresh existing.
Thinking a workaround for this is to just POST to /queryIndicators?api-version=2021-10-01-preview with keyword then delete and re-create the matching IOC as use case here is to prevent duplicates from systems like MISP, whereby a modified attribute in MISP would update the timestamp so an interval based restSearch on timestamp would pick up a pre-ingested IOC.
More than open to suggestions if there's a better method though.