- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- New Blog Post | Microsoft Threat Intelligence Matching Analytics
New Blog Post | Microsoft Threat Intelligence Matching Analytics
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 28 2021 10:29 AM
Microsoft Threat Intelligence Matching Analytics - Microsoft Tech Community
Azure Sentinel is a cloud native SIEM solution that allows various ways to bring your own threat intelligence data (BYOTI) like STIX/TAXII and from various Threat Intelligence Platforms.
Apart from bringing in your own threat intelligence data, you can also reference threat intelligence data produced by Microsoft for detection and analysis.
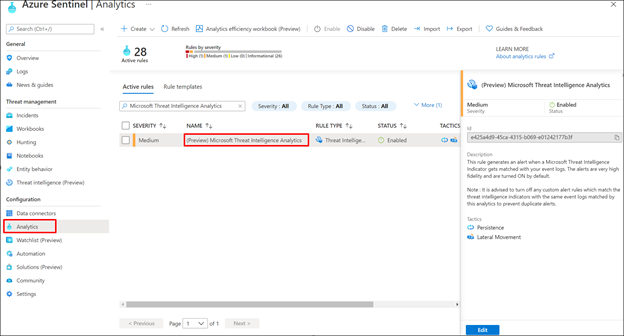
Today we are announcing launch of a new analytic rule called Microsoft Threat Intelligence Matching analytics that matches Microsoft generated threat intelligence data with your logs and generates high fidelity alerts/incidents with appropriate severity based on the context of the log. Once a match is generated, the indicator is published to your threat intelligence repository in Azure Sentinel.
In this blog, we will cover:
- Details and working of the Microsoft Threat Intelligence Matching analytics
- How to enable Microsoft Threat Intelligence Matching analytics
- Log sources and threat intelligence types used for matching by this rule
- Alert grouping for incident generation and searching IOC’s published by this rule
Original Post: New Blog Post | Microsoft Threat Intelligence Matching Analytics - Microsoft Tech Community