- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- New Blog Post | Bring Threat Intelligence from SEKOIA.IO using TAXII data connector
New Blog Post | Bring Threat Intelligence from SEKOIA.IO using TAXII data connector
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 10 2022 01:02 PM
Bring Threat Intelligence from SEKOIA.IO using TAXII data connector - Microsoft Tech Community
Microsoft Sentinel is a cloud native SIEM solution that allows you to detect and hunt for actionable threats. Microsoft Sentinel provides a rich variety of ways to import threat intelligence data and use it in various parts of the product like hunting, investigation, analytics, workbooks etc.
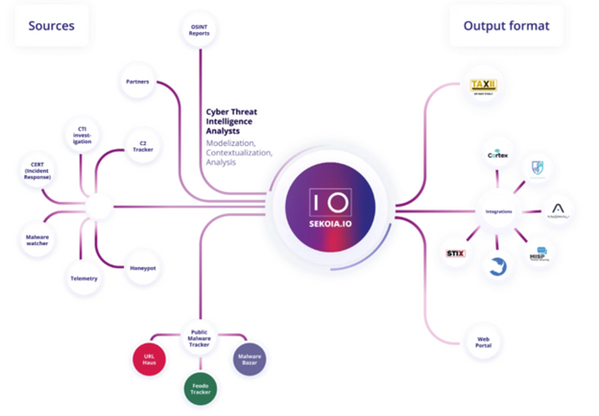
Cyber threat intelligence is the new oil of cybersecurity: if SIEM are engines, CTI is the fuel that makes you faster than attackers. It is now time to move from crude oil (raw streams of IOCs) to jet fuel: using intelligence to describe precisely how threats occur and get a bird’s eye view of your threat landscape.
Microsoft Sentinel was one of the early adopters of STIX/TAXII as the preferred way to import threat intelligence data. Microsoft Sentinel has built a data connector called the “Threat Intelligence -TAXII” connector that uses the TAXII protocol for sharing data in STIX format. This data connector supports pulling data from TAXII 2.0 and 2.1 servers. The Threat Intelligence – TAXII data connector is essentially a built-in TAXII client in Microsoft Sentinel to import threat intelligence from TAXII 2.x servers.
Today we are announcing the availability of the SEKOIA.IO Cyber Threat Intelligence into Microsoft Sentinel using the TAXII data connector.
Original Post: New Blog Post | Bring Threat Intelligence from SEKOIA.IO using TAXII data connector - Microsoft Tech...
- Labels:
-
Blogs
-
Threat Intelligence
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 15 2022 12:01 AM
Hello
I have a question.
How i can bring the indicators from SEKOIA though TAXII data connector, bcz there are not collection ID in TAXII related to SEKOIA.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 17 2022 04:49 AM
Hello @Qusai_Ismail,
You can refer to the documentation that describes how to obtain the collection ID: https://docs.sekoia.io/intelligence_center/integrations/microsoft-sentinel/
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 17 2022 06:11 AM