- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- New Blog Post | Analyzing Endpoints Forensics - Azure Sentinel Connector
New Blog Post | Analyzing Endpoints Forensics - Azure Sentinel Connector
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 11 2021 09:46 AM
Analyzing Endpoints Forensics - Azure Sentinel Connector - Microsoft Tech Community
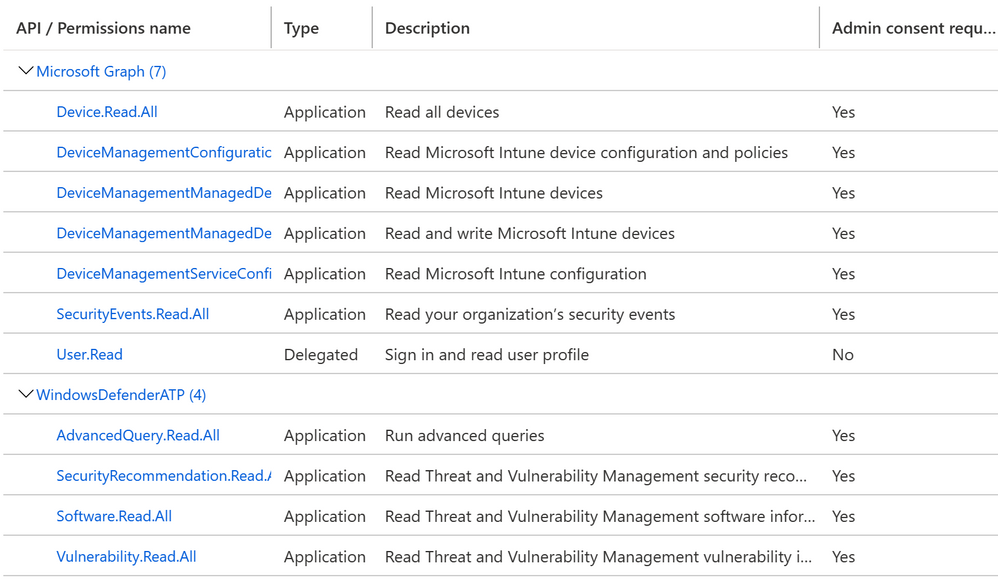
The field of Endpoint forensics seeks to help investigators reconstruct what happened during an endpoint intrusion. Did an attacker break in because of a missing definition / signature / policy / setting or a configuration, and if so, how? What havoc did the attacker wreak after breaking in? Tools that help investigators answer these types of questions are still quite primitive and are often hindered by incomplete or incorrect information. Analyzing Endpoints Forensics - Azure Sentinel Connector can enable more-powerful forensic analysis through techniques such as streaming a computer’s EPP (Endpoint Protection) health status, policies, settings, and configuration in addition to IoT vulnerable assets, data events & vulnerabilities.
Devices (IT/OT) health state and security configurations policies and settings (Microsoft Defender for Endpoint & Azure Defender for IoT) are critical to SOC team helping them to address the following use cases:
- Identifying onboarded devices and their health status
- Activity and a security posture for IT/OT assets
- Viewing the compliance status of the devices based on the security recommendations
- Identifying devices vulnerabilities and hence provide a triage – matrix remediation framework
Original Post: New Blog Post | Analyzing Endpoints Forensics - Azure Sentinel Connector - Microsoft Tech Community