- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Re: KQL Queries: Fortinet
KQL Queries: Fortinet
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2023 02:02 AM
I am looking to extract from Fortinet log(s), any DNS events which are deemed high risk.
I have written this query BUT could do with some advice on how to improve it or identify other related queries, that shows those high-risk elements...
//List DNS entries with risk-related Log Severity
CommonSecurityLog
| where TimeGenerated > ago (6h)
| where DeviceVendor =~ "Fortinet"
| where ApplicationProtocol == "DNS"
| where LogSeverity has_any ("0","1","2","3")
| where isnotempty(SourceIP) and isnotempty(DestinationIP) and SourceIP != "0.0.0.0"
| where DeviceAction !in ("close", "client-rst", "server-rst", "deny") and DestinationPort != 161
| project DeviceProduct, LogSeverity, DestinationPort, DestinationIP, Message, SourceIP, SourcePort, Activity, SentBytes, ReceivedBytes
| sort by LogSeverity
ANY help is appreciated...
- Labels:
-
KQL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2023 03:48 AM
Solution@JMSHW0420
Maybe look at ASIM,
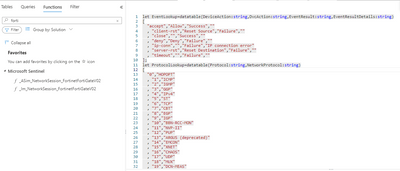
1. Look at the ASIM parser for Fortigate, to get some of the Columns you may need in a normalized way (you may want to adopt the column naming to get your finished query aligned to ASIM now - that way if Forti release a parser you are probably virtually ready to use it).
2. look at the other DNS ASIM parsers, whilst there isn't one for Forti (yet), you may get some ideas.
3. Also look at the DNS Queries that use ASIM Azure-Sentinel/Detections/ASimDNS at master · Azure/Azure-Sentinel (github.com)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2023 05:04 AM
Thank you for the rapid response.
Not really used ASIM parsers in anger. So assume this means deploying the related parser from the GitHub repository provided at: https://github.com/Azure/Azure-Sentinel/tree/master/Parsers?
Your first screen-shot is generated from where?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2023 05:16 AM
@JMSHW0420
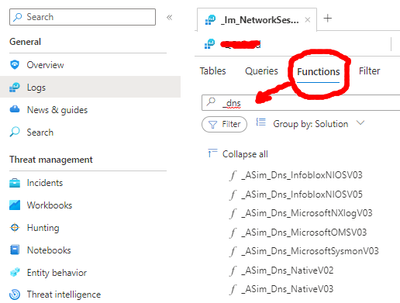
Many are now enabled by default - thanks to Microsoft. Look in Sentinel --> Logs
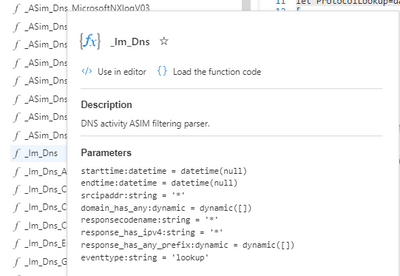
Most ASIM parsers are duplicated, one starts with _IM_ ,and the other style _ASim_ The difference is that the _IM_ version allows parameter to be passed (you can see which parameters when you hover over the name), you can also use the function or load the function code to see what its doing!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2023 05:22 AM
Sorry mate, I actually do know what you mean. Thanks for the clarification though. Much appreciated.
Jason
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2023 03:48 AM
Solution@JMSHW0420
Maybe look at ASIM,
1. Look at the ASIM parser for Fortigate, to get some of the Columns you may need in a normalized way (you may want to adopt the column naming to get your finished query aligned to ASIM now - that way if Forti release a parser you are probably virtually ready to use it).
2. look at the other DNS ASIM parsers, whilst there isn't one for Forti (yet), you may get some ideas.
3. Also look at the DNS Queries that use ASIM Azure-Sentinel/Detections/ASimDNS at master · Azure/Azure-Sentinel (github.com)