- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Re: fooUser appearing in Sentinel device logs
fooUser appearing in Sentinel device logs
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 19 2023 06:43 AM - edited Apr 26 2023 11:38 PM
Hi,
I noticed from an alert in MS Security Center there is an account called fooUser@<domain> that seems to do a lot of client operations outside of what I understand the account is for, which is Intune enrollment in Autopilot. https://call4cloud.nl/2022/09/foouser-meets-the-cosmic-autopilot-user/
But I'm seeing process creations, file creations etc.. This started the 11th of April on a single device and has since escalated to over a hundred. The first device was actually in an Autopilot process when the events started to get logged, but now there are a lot of machines that have been active for a long time where the logs are coming in from as well.
The following query is what I used to find the events in Advanced hunting:
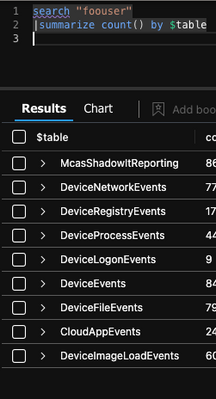
search in (DeviceEvents,DeviceFileCertificateInfo,DeviceFileEvents,DeviceImageLoadEvents,DeviceInfo,DeviceLogonEvents,DeviceNetworkEvents,DeviceNetworkInfo,DeviceProcessEvents,DeviceRegistryEvents) "fooUser" | sort by TimeGenerated asc
Do anyone else see this behavior?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 19 2023 07:03 AM
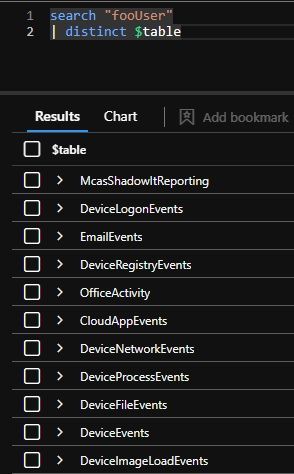
Also, run the following to show exactly which tables fooUser is showing up in:
search "fooUser"
| distinct $table
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 20 2023 01:53 AM
Hi Rod, it occurs to my organisation as well. It appears in the following table.
Most of them are in the InitiatingProcessAccountUpn field name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 20 2023 02:05 AM
I spotted this today in our logs too. Had me very confused.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2023 07:10 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 24 2023 04:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 25 2023 10:57 AM
Replying to keep abreast of this as well. Just noticed this new user in our Cloud Apps portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2023 10:16 AM - edited Apr 26 2023 10:34 AM
Same as everyone else here. Seeing fooUser in some tables and in Defender for Cloud apps. Most will understand why this would be alarming to anyone who administers a domain. I've opened a ticket with Azure support and will report back what I learn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2023 02:54 PM - edited Apr 26 2023 02:55 PM
Hello. Just a bit of an update to those other worry warts out there. This is definitely NOT a security issue. I did some preliminary troubleshooting with the Defender Team and I do not fully understand the whole issue as of yet, but the fooUser is a part of the Intune MDM enrollment process. If you take a look at this doc, you will see the fooUser mentioned. https://techcommunity.microsoft.com/t5/intune-customer-success/support-tip-understanding-auto-enroll... We also found fooUser in my registry. I am planning to jump back into it with the Defender Team tomorrow to see if we can get that username to not show up in the data somehow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2023 02:59 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2023 11:43 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 27 2023 01:12 AM
Have a support ticket open with MS for this also.
Some things that I was concerned with was the huge amount of data seen in use by the foouser account across over 500+ apps seen in Defender for Cloud Apps (MCAS)
Example, why is foouser account seen to be using (upload and download) for Gmail if it's just used for Intune enrollment? How can we determine which actual user is involved in certain activity when MCAS just shows the foouser account?
If we ever did have a major incident and the foouser UPN account was being shown in the logs instead of the actual users UPN (as we are currently seeing at times) wouldn't this be a big issue in regards to collecting forensic investigation logs in regards to the actual user, as all we can see is the foouser instead. This would also be a great way for a bad actor to hide their tracks, by hiding in plain sight. It's that part that concerns me, especially when thinking about potential data exfiltration.
I can also see that it is seen on 128 devices (never more) but less at the W/E (potentially where users machines are off) - what is significant about the number 128 as we have way more Intune enrolled machines that that, so would have expected this to be seen on all devices?
It shows in 11 tables for us when checking @Rod_Trent query:
search "fooUser"
| distinct $table
Glad this is getting some traction though from MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 27 2023 01:39 AM
Even though the name is used in certain Intune processes, that's definitely not what it is mostly known for.
Good catch with the 128 devices, I see the exact same thing.
I noticed that when I opened a file on a computer, fooUser would show up in events for creating the link to the file in the "Recent files" section in Explorer and similar actions that the system performs behind the scenes during such user activites.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 27 2023 06:07 AM
@Brok3NSpear Very good and valid points made here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 28 2023 02:45 PM
SolutionThe backend Team at inTune is working on a fix for the issue currently. Here was the official answer of what occurred:
'This user does not represent a security threat. As part of the DLP (Data Loss Prevention) service, an attempt is made to identify users associated with machines. Recently, changes were implemented to the fallback method for WAM user fetching. In hybrid join scenarios, there are instances in which a domain user cannot successfully be resolved to an AAD (Azure Active Directory) user identity and in these instances, the auto-join identity (foouser) is returned. Microsoft is evaluating both short- and long-term solution to filter out DLP requests and alerts associated with foouser.'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 08 2023 05:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 08 2023 07:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 08 2023 03:24 PM
Microsoft's response of "does not represent a security threat" may be true, but is doesn't stop this being a security risk for alerts we can't attribute, or alerts that aren't firing at all because of the broken relationship between tables.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 28 2023 02:45 PM
SolutionThe backend Team at inTune is working on a fix for the issue currently. Here was the official answer of what occurred:
'This user does not represent a security threat. As part of the DLP (Data Loss Prevention) service, an attempt is made to identify users associated with machines. Recently, changes were implemented to the fallback method for WAM user fetching. In hybrid join scenarios, there are instances in which a domain user cannot successfully be resolved to an AAD (Azure Active Directory) user identity and in these instances, the auto-join identity (foouser) is returned. Microsoft is evaluating both short- and long-term solution to filter out DLP requests and alerts associated with foouser.'