- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Re: Extract json from windows event log (SecurityEvent)
Extract json from windows event log (SecurityEvent)
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 01 2023 09:30 AM
Hello everyone,
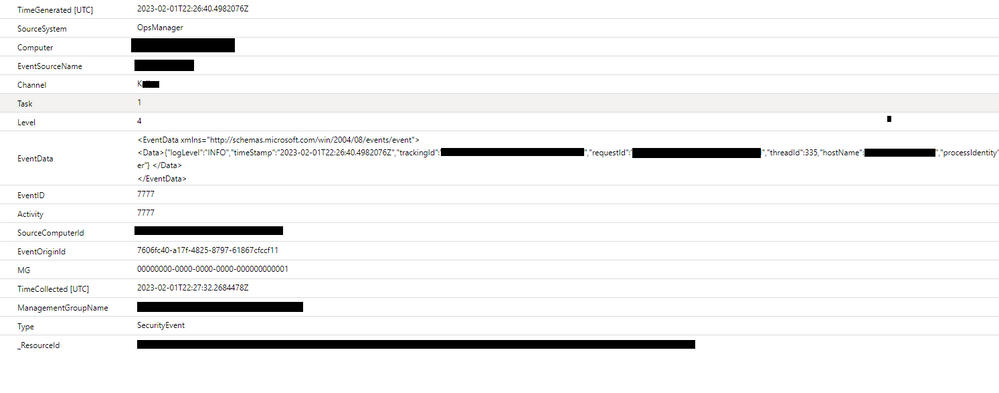
We are currently trying to parse logs that are being ingested into SecurityEvent table with following information all being in a single field called "EventData". We have tried using parse_json and extractjson but not sure how to construct the right query.
<EventData xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<Data>{"logLevel":"INFO","timeStamp":"2023-01-31T16:49:21.5973429Z","trackingId":"value","requestId":"value","threadId":34,"hostName":"value","processIdentity":"domain\\user","endpoint":"url","referrer":"ip","operation":"operationName","AccountId":38127231211,"identity.loginName":"domain\\user","identity.authenticationType":"domain.domain","identity.uniqueId":"randomid","identity.accountName":"user name","logger":"SecurityLogger"} </Data>
</EventData>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 01 2023 10:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 01 2023 02:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 02 2023 04:05 AM - edited Feb 02 2023 04:16 AM
SolutionHello @Ciyaresh,
Have you tried to use parse_xml()?
parse_xml() - Azure Data Explorer | Microsoft Learn
For example, try to launch this query and see if it returns a parsed EventData xml. Send the result.
YourTableName
| extend Data=parse_xml(EventData)
| project Data
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 02 2023 04:05 AM - edited Feb 02 2023 04:16 AM
SolutionHello @Ciyaresh,
Have you tried to use parse_xml()?
parse_xml() - Azure Data Explorer | Microsoft Learn
For example, try to launch this query and see if it returns a parsed EventData xml. Send the result.
YourTableName
| extend Data=parse_xml(EventData)
| project Data