- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Excluding specific events from log analytics agent (Windows)
Excluding specific events from log analytics agent (Windows)
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 21 2021 11:58 AM
Hello everyone,
We are in phase of creating a PoC to possibly replace our SIEM. So far I believe we have done a good job presenting capabilities of Sentinel. However, there is one main issue for us right now, which is not being able to find a solution to log noise. We have Log Analytic Agents deployed on our on-prem servers and workstations. Installation was really straight forward and we have chosen the "common" events filter instead of all events. We have tried all events but AppLocker events were too noisy to handle (increasing the cost as well)
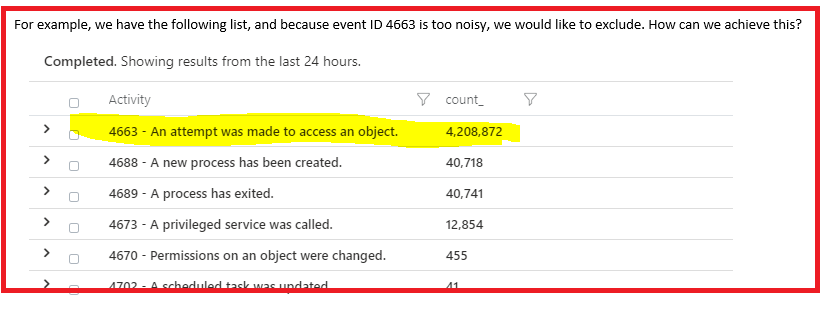
However, since we have deployed agents into another network zone, we have seen a single windows event constantly triggering (90% of the log usage is coming from this one event). I have tried looking at the documentation to see if we are able to exclude specific events from being collected but I no luck so far. Although I did see you can do this with agents installed on azure VMs, nothing about on-prem servers.
below is the event we would like to exclude
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 21 2021 12:24 PM
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/data-collection-rule-azure-monitor-agent
For on-prem installations, the system must have Azure Arc installed and enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 22 2021 03:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 22 2021 04:58 AM