- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Re: Error when running playbook Block-AADUser-Alert
Error when running playbook Block-AADUser-Alert
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 13 2022 02:36 AM
Hello,
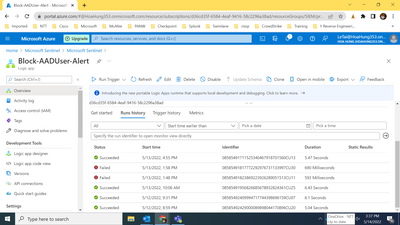
I have personal account and I am trying Microsoft Sentinel. My senario is when user account (not admin) changes his authentication method, an alert is triggered and then I run built-in playbook Block-AADUser-Alert to disable this account. I get following error when running this playbook:
{
"error": {
"code": "Request_ResourceNotFound",
"message": "Resource '[\"leloc@hoahung353.onmicrosoft.com\"]' does not exist or one of its queried reference-property objects are not present.",
"innerError": {
"date": "2022-05-13T03:06:46",
"request-id": "84bab933-eb79-4352-9bdf-e6d5444a1798",
"client-request-id": "84bab933-eb79-4352-9bdf-e6d5444a1798"
}
}
}
I have tried to assign all required permissions (User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All), authorized api connection,.. but it can not solve the issue.
Would anyone help advise how to solve ? Is it because of personal account ?
Best Regards,
An
- Labels:
-
SOAR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 13 2022 03:42 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 13 2022 07:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 13 2022 09:04 AM
Do you use this playbook from GitHub? https://github.com/Azure/Azure-Sentinel/tree/master/Playbooks/Block-AADUser
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 12:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 01:20 AM
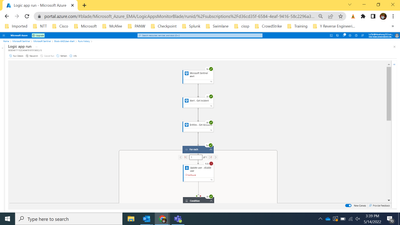
Click on "Failed" and you will be able to debug the playbook. Find the part where you have a red X and open it. Share the results here.
And ensure that you do not have an "Invalid connection" message for any of the blocks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 01:42 AM
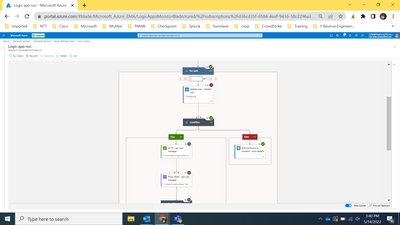
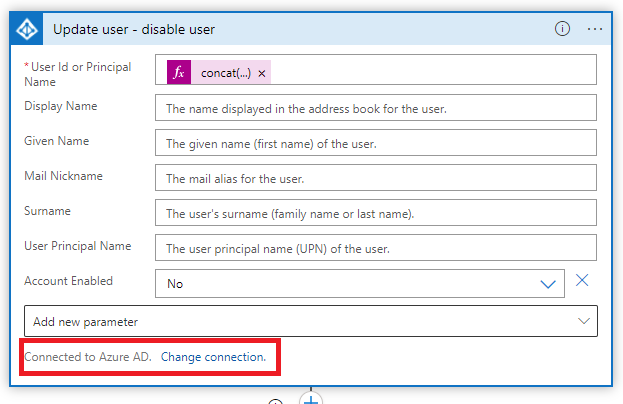
The playbook run succeeded, but the workflow get error at the operation that disable user:
Best Regards,
An
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 02:09 AM
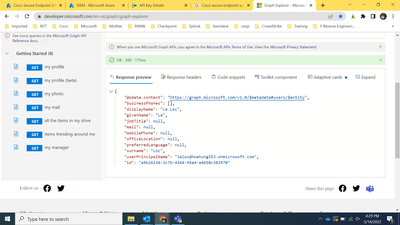
On the left sid Sign-in to your account and then, run this query: GET https://graph.microsoft.com/v1.0/users/{id | userPrincipalName} -> https://graph.microsoft.com/v1.0/users/leloc@hoahung353.onmicrosoft.com.
And check if you get 200 or 404.
If you get 200, everything is fine. And I assume the issue is with the Playbook itself.
1. Check the permissions of the user that is used to connect the Playbook to AAD.
2. Check the fields in "Update user" and "Entities - Get Account" blocks. Ensure that they don't have any extra symbols like / " [ etc.
I am going to try to simulate the same error in my environment and update you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 02:31 AM
The user that connects the block "Update user" with Azure AD must have sufficient permissions and not the app itself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 02:32 AM
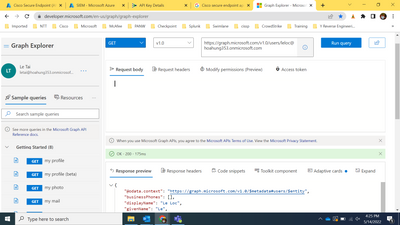
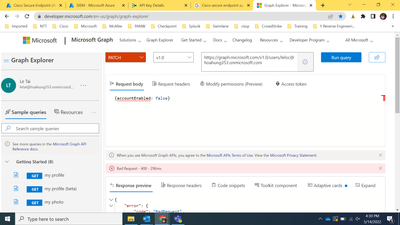
@mikhailf Yes I tried graph explorer and when I use method GET then it works, but when I use method PATCH with request body { accountEnabled: false} as in the playbook, then I get not insufficient privilege although I have assigned all required permissions:
Regards,
An
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 02:43 AM
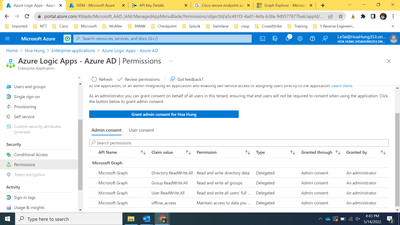
@mikhailf I go to Azure AD -> Enterprise Application -> Azure Logic App -> permission, I found following permissions. I don't know how to assign more permissions, and I guess User.ReadWrite.All, Directory.ReadWrite.All cover User.Read.All, Directory.Read.All:
Best Regards,
An
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 03:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 03:21 AM
@mikhailf I did that but it does not help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 07:53 AM
SolutionCould you try the second playbook for disabling AAD users? The one that is based on Incident.
And please, check this: https://github.com/microsoftgraph/microsoft-graph-docs/blob/main/api-reference/v1.0/resources/securi...
There is a table with supported methods and systems.
Does that mean that PATCH method is not supported by Sentinel alerts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 06:20 PM
@mikhailf There are 2 api for the "Update user" and I authroized both of them:
Regarding the support table from the link you mentioned, I don't see Azure AD there, There is Azure AD IP which is different from Azure AD, I guess. I have tried Incident instead of alert but I still get the same error
Best Regards,
An
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 06:22 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 15 2022 11:46 PM
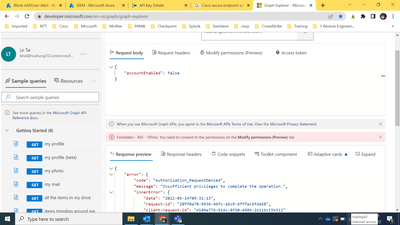
I know the reason why - there is no attribute "accountEnabled" . If we use GET then we can see all attributes returned for this call and there is no "accountEnabled". I try other attribute like "mobiPhone", "mail", "officeLocation" and it works !@mikhailf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 15 2022 11:52 PM
I used GET now with my user and I don't see any parameter that allows me to disable my account.
Have you found anything?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2022 12:07 AM - edited May 16 2022 01:05 AM
But I don't think that this is the reason. The playbook below works well and I can disable users using it. (Only two parts Sentinel Alert and Update User).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2022 02:19 AM
One more thing. You don't need to provide Azure Logic Apps - Azure AD with any permissions.
What is the user that connects "Update user" part with AzureAD?
Does it have permission to disable other accounts?
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 14 2022 07:53 AM
SolutionCould you try the second playbook for disabling AAD users? The one that is based on Incident.
And please, check this: https://github.com/microsoftgraph/microsoft-graph-docs/blob/main/api-reference/v1.0/resources/securi...
There is a table with supported methods and systems.
Does that mean that PATCH method is not supported by Sentinel alerts?