- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Re: Close MCAS alert via API
Close MCAS alert via API
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 01 2020 08:55 AM
Good afternoon people.
I am drawing a flow in the Logic App to close the alert in MCAS.
I have little experience with API and would like to get help.
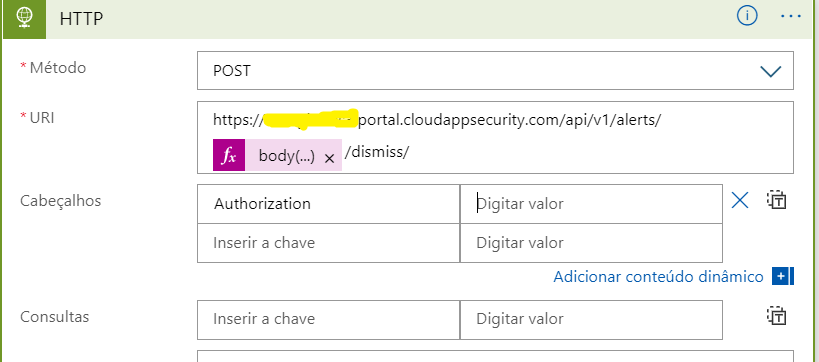
I was using the API call via the path [
[XXXX.us3.portal.cloudappsecurity.com/api/v1/alerts/ID_ALERT/dismiss/]to end the alert as a false positive.
The documentation updated and reported that this feature is obsolete,
passing using the path [api / v1 / alerts / close_false_positive /] with filters, as reported here [ docs.microsoft.com/en-us/cloud-app-security/api-alerts-close-false-positive ]
The point is that I am not sure how to pass the filters through the Logic APP in HTTP POST of this new format.
Can anyone help me in this regard?
Old process:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 02 2020 05:43 AM
@Luizao_f Hello,
This is what I've been doing from my end and it seems to be working fine. Please give it a try and see how it goes.
Where MCASTenant is the name of the tenant. Make sure that you have a token for authorization. I assume that you are well aware as to how the token has to be generated. Make no changes value of the header should be (Token followed the token generated). In case you do not know how to generate a token here's the link(https://docs.microsoft.com/en-us/cloud-app-security/api-tokens)
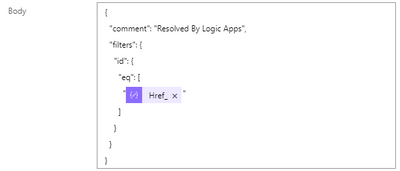
Add this to your Body
where Href is the alert id generated in MCAS. For testing copy the id from Sentinel incident and try to execute, at a later stage pass this as a variable.
Hope this works for you!!.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 03 2020 04:10 PM
@Pranesh1060
Very good. I tested your process and it worked correctly. Thank you. Show.
My second step is to close open incidents in Defender ATP. Do you have something like that? Are you ending incidents on another technology through the Logic App?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 06 2020 05:55 AM
@Luizao_f , @Pranesh1060 : note that incident synchronizatoin with all Microsoft 365 defender sources is already in private preview.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 06 2020 04:01 PM
Is this reverse closure mentioned above about Micrososft 365 Security Center (https://security.microsoft.com)? I use Azure Sentinel as a centralizer, so I am trying to create integrations for the reserve closure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 07 2020 05:26 AM
@Luizao_f We do have the connector available which can update the alert directly in MDATP and perform other operations like Run AV scan, Collect packages for investigation etc etc. The action you are looking for is update alert. Maybe you can use the same logic to split and isolate the alert id and then close it.