- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- What's new with Microsoft Sentinel at Secure
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Sentinel: What’s new at Microsoft Secure
Microsoft Sentinel taps into the power of AI, automation, and Microsoft’s deep understanding of the threat landscape, empowering defenders to hunt and resolve critical threats at machine speed, at a lower TCO than other SIEM solutions. It is the consolidated SecOps platform for teams that want a next-gen, cloud-native SIEM solution to help them to proactively protect their digital estate. As an industry leader in the security analytics space, companies of all sizes, MSSPs and MDRs trust Microsoft to keep them safe.
We continue to invest in solutions that will help defenders scale their security operations, stay ahead of evolving threats, and secure more of their digital assets. Some recent and upcoming innovations that we are excited to share include:
- Expanded SAP app coverage and SAP certification defenders scale their security operations, stay ahead of evolving threats, and secure more of their digital assets
- New Incident Management, Investigation and Response Features
- Connections to Microsoft Defender Threat Intelligence
- Increased Multi-cloud protection
Expanded coverage for business applications and SAP certification
Security doesn’t stop at cloud and infrastructure protection. Business applications pose a unique security challenge with highly sensitive information that can make them prime targets for attacks. Microsoft is ready to address the growing need for business application security solutions with expanded support business applications within Microsoft Sentinel. Read on for the latest on SAP coverage.
We’re pleased to announce that SAP has certified the Microsoft Sentinel solution for SAP® applications for integration with SAP S/4HANA®Cloud, private edition (RISE with SAP), SAP S/4HANA (on-premise software) and SAP ECC via the External Alert and Monitoring interface. The certified integration scenario is evidence of our deep commitment to providing security for SAP software products. This joint effort between SAP and Microsoft validates the technical capabilities and quality of integration of Microsoft Sentinel with RISE with SAP and is listed in the SAP Certified Solutions Directory, elevating our profile for SAP customers in search of a security solution.
Expanded coverage for SAP includes a limited preview of the Microsoft Sentinel solution for SAP Business Technology Platform (SAP BTP). SAP BTP brings together application development, data and analytics, integration, automation, and AI capabilities in one unified environment. Business users can automate tasks, create fast, flexible workflows, and personalize interfaces without coding. The Microsoft Sentinel solution for SAP BTP collects audits and activity logs from Cloud Foundry infrastructure and apps of SAP BTP to monitor suspicious activities. If you are interested in participating in the preview program please sign up here.
Other highlights for SAP software protection include new data exfiltration detection rules to help teams monitor activities. These include such activities as files downloaded from a malicious IP address, and sensitive data saved or exported to a USB drive. This helps ensure that internal and external actors do not misuse large volumes of confidential or sensitive information. New collaboration features will allow SOC to permission access to SAP team to specific data to assist in investigation and remediation of issues.We have also released an SAP log audit workbook to publicly preview, designed to give customers a bird's eye view of user audit activity, which will help them secure their SAP systems and gain quick visibility into suspicious actions.
New Incident Management, Investigation and Response Features
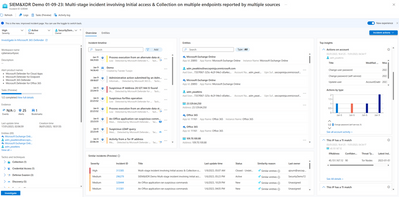
We’ve released a new incident experience to public preview, along with many new features for investigation & response and incident management. These new capabilities offer analysts more information and tools for quick and efficient triage and coordinated remediation. Analysts can better understand an incident, its details, its context, and the scope of breach with minimal context switching and easier navigation.
Some of the new incident management features currently in public preview include:
- Top insights selected by Microsoft security experts in the overview tab for quick information on crucial entity information.
- The new activity log keeps comments and audits of incidents, both manual and automated. This makes it easier to collaborate and ensure adequate handling of an issue.
- Log Analytics querying window that allows customers to query tables with incident details still visible, allowing for minimal context switching and more efficient workflows.
- Incident tasks provides a central checklist to handle the process of incident triage, investigation, and response. This feature allows SOC engineers and analysts to document, update and align the standard of incident response across analysts teams and shifts.
Customers are already enjoying these new capabilities:
“The combination of most of the incident data in one page, without forcing the creation of a separate view, enabled us to streamline our response by limiting the need to open and close the items pages.” Brett Paradis – Director of Cyber Threat and Intelligence – Keyavi Data
Connections to Microsoft Defender Threat Intelligence
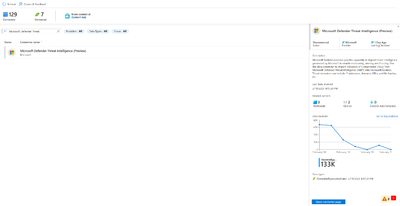
We are bringing Microsoft Defender Threat Intelligence (MDTI) into Microsoft Sentinel through a new connector and content. With more threat intelligence in Microsoft Sentinel SOCs can stay ahead of the latest threats and identify suspicious activity quicker. Microsoft has an unparalleled view of threats, tracking over 65 trillion signals daily and MDTI is unique in its continuously updating map of the external threat landscape and infrastructure.
With the MDTI data connector, now in Public Preview, customers can get high fidelity feeds of indicators of compromise (or IOCs) from MDTI. The IOCs from this data connector are shown on the threat intelligence blade inside Microsoft Sentinel. Microsoft Sentinel also matches high fidelity nation state indicators with customer logs using Microsoft Defender Threat Intelligence analytics. These insights can be used to enrich security operations with more insightful analytics, investigations, and hunting capabilities.
We are also releasing enrichment playbooks from MDTI. Customers will be able to find a set of playbooks in the Content Hub that enables them to enrich entities within an incident raised in Microsoft Sentinel in the form of comments inside of an incident. With this content, customers can enrich an incident with external context and understand how it's linked to known threat infrastructure and activity across the world.
Increased Multi-Cloud Protection
Companies operate on multiple clouds, and the ability to monitor all of them in one place makes it easier to identify issues and understand how threats are moving across vectors. We are expanding support for Amazon Web Services (AWS) and Google Cloud Platform (GCP) cloud data, ensuring customers can protect more of their digital estate, in a unified solution.
We are introducing support for CloudWatch logs as an additional predefined log supported by a data connector, bringing in critical operational information from AWS sources to allow customers to better understand and secure AWS systems and applications. This release builds on our existing AWS coverage that includes CloudTrail, VPC flow and Guard Duty (all currently in public preview). Additionally, we are announcing better self-help diagnostics for the AWS connector. See documentation for AWS integrations here.
We are transitioning to a new infrastructure based on Pub/Sub for GCP connectors that will offer better scalability, robustness, and flexibility for exporting logs. The first connector we will implement using this new infrastructure will be for Audit Logs (in public preview), with new connectors for Security Command Center (SCC) coming soon.
Learn More
Microsoft is committed to empowering our customers with modern security tools and platforms to enable critical protection for your organization and users. To learn more about Microsoft Sentinel capabilities and new announcements see:
- Microsoft Sentinel: https://aka.ms/microsoftsentinel
- Blogs: Microsoft Sentinel Blog - Microsoft Tech Community
- Protect critical systems within SAP systems: Protect critical information within SAP systems against cyberattacks - Microsoft Tech Community
- Connect Microsoft Sentinel to Amazon Web Services to ingest AWS service log data | Microsoft Learn
- Microsoft Customer Stories
- Microsoft Sentinel documentation | Microsoft Learn
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.