- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- Transferring Microsoft Sentinel scheduled alert rules between different workspaces using PowerShell
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In this article we are going to explain the process to transfer scheduled alert rules between different workspaces. This process can be useful when you have more than one Log Analytics workspace and you need to transfer your alerts from one workspace to another. It can also be useful to have a backup of all your alerts in case of a disaster.
This blog post is intended for a technical audience to support and troubleshoot the export/import process of these types of alerts from Microsoft Sentinel and therefore it is assumed that you have a technical knowledge base in both Microsoft Sentinel and PowerShell.
A PowerShell script with the functions explained is provided at the end of this article.
Pre-requisites
- PowerShell version 5 or higher
- Az.Resources
- Az.OperationalInsights
- Azsentinel
We can install Az.OperationalInsights from PowershellGallery or with the next command:
Install-Module -Name Az.SecurityInsights -AllowClobber -Scope CurrentUser -Force
There are several ways to transfer Microsoft Sentinel alerts using the Export-Import commands in PowerShell. One of the most important topics is the JSON file format and the Sentinel root schema.
This are the three types of alerts based on the Microsoft Sentinel root schema:
{
"Scheduled": [
...
],
"Fusion": [
...
],
"MLBehaviorAnalytics": [
...
],
"MicrosoftSecurityIncidentCreation": [
...
]
}
We are going to create a simple script called example1.ps1 in which we will load the mentioned modules and export our alerts using the Get-AzSentinelAlertRule cmdlet. and obtain this Json file with the alerts exported.
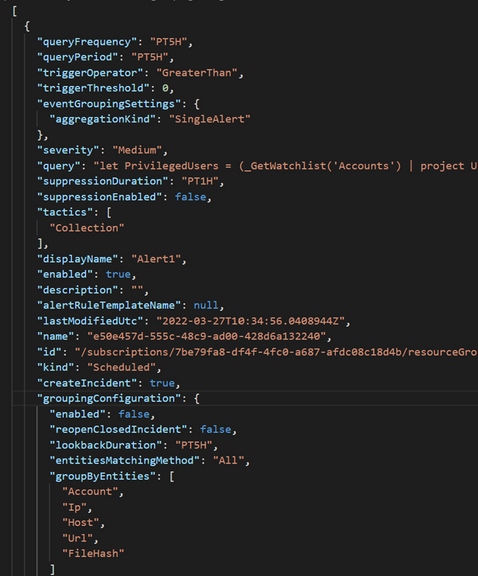
The first thing we have to pay attention to is that with this method we are not obtaining the structure of the root schema inside the file. Let's see what happens if we try to import these alerts:
We will use the command:
Import-AzSentinelAlertRule -WorkspaceName [Worskpacename] -SettingsFile "C:\tmp\Alerts.json"
now we have the following error, as shown in the screenshot below:
To fix this issue we will use the next command to export all the rules:
Export-AzSentinel -workspace $workspaceName -Outputfolder $ruleExportPath -Kind All
With the Export-AzSentinel command executed we will get three files:
- AlertRules
- HuntingRules
- Templates
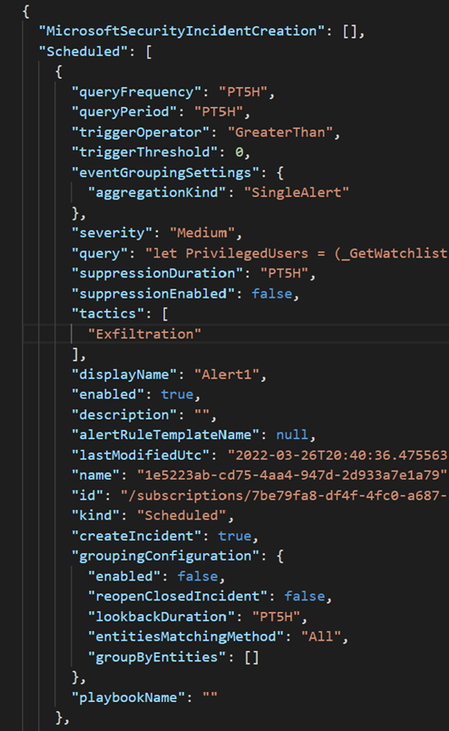
Let's focus on the AlertRules file and take a look at its structure. Now we have the scheduled root schema inside of the JSON code and with this structure now we can import this alert rule to another Workspace.
but before we can import our alerts, we need to solve another issue related to the Tactics within the rule.
Tactics
The current version of the Import-AzSentinelAlertRule command does not recognize all the tactics that can be associated with an alert. This is a current list of tactics that are recognized:
- Initial Access
- Persistence
- Execution
- Privilege Escalation
- Defense Evasion
- Credential Access
- Lateral Movement
- Discovery
- Collection
- Exfiltration
- Command And Control
- Impact
To fix this issue we need to add a piece of code before importing the alert rules in the final import script: all that we need to do is one of the accepted tactics in the tactic's properties inside of the JSON file. To do this we can create an array with accepted tactics and then we replace the not accepted tactic within the JSON file.
##### Fix Tactics issue #############
$content = get-content -Path $ruleExportPath
$jsonfile = $content | ConvertFrom-Json
$alerts = $jsonfile.Scheduled
$tactics_ok = "InitialAccess","Persistence","Execution","PrivilegeEscalation","DefenseEvasion","CredentialAccess","LateralMovement","Discovery","Collection","Exfiltration","CommandAndControl","Impact"
$random_tactic = get-random -InputObject $tactics_ok
foreach($alert in $alerts)
{
if($alert.tactics -eq "reconnaissance" -or "ResourceDevelopment")
{
#Write-host "Tactic:" $Alert.tactics "Not accepted"
$alert.tactics = $random_tactic
}
}
$jsonfile | ConvertTo-Json | Set-Content -path $ruleExportPath
##### End of Fix Tactics issue ################
Now we have the schema referenced in the header and we have the tactics issue solved and we are going to proceed with importing the alerts:
Import-AzSentinelAlertRule -WorkspaceName $workspaceName -SettingsFile $ruleExportPath
You can see in the screenshot below that we now have the alerts successfully imported into the second workspace:
We can also build a PowerShell script to automate this procedure and additionally we can include a piece of code to create our new workspace where we will import the Alerts.
try {
$AuxWorkspace= Get-AzOperationalInsightsWorkspace -Name $WorkspaceName -ResourceGroupName $ResourceGroupName -ErrorAction Stop
$ExistingLocation = $AuxWorkspace.Location
Write-host "Workspace named $WorkspaceName in region $ExistingLocation Already exists." -ForegroundColor Green
} catch
{
Write-host "Creating new workspace named $WorkspaceName in region $Location..."
New-AzOperationalInsightsWorkspace -Location $Location -Name $WorkspaceName -Sku "PerGB2018" -ResourceGroupName $ResourceGroupName
Set-AzSentinel -Workspacename $workspaceName
}
And build the script:
1 - Function install modules and cmd selection message for the menu
2 - Build the Switch with export function
3 - Build Switch with option 2 for import Alerts
3 - Finally the option for create a new workspace
Summary
For a couple of closing comments, it's important to note that this process was tested only for scheduled alerts. If you have other artifacts associated into the scheduled alerts such as a Watchlist or a playbook you must create them separately.
If you need more information about the Microsoft Sentinel PowerShell module can be found here. You can also visit the Sentinel community on GitHub where you can find new solutions and use cases for Microsoft Sentinel.
Please test this process and if you have any questions or feedback on it, I would be happy to help you further.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.