- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- New Threat Intelligence features in Microsoft Sentinel
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
As the digital footprint of organizations is on an all-time rise, Microsoft Sentinel (our cloud native SIEM solution) allows customers to import security event data to find actionable threats. Threat intelligence (TI) is embedded in Microsoft’s security solutions, such as SIEM+XDR to identify and detect security alerts and incidents in your environment. Threat Intelligence can be anything from tactical TI such as observables (IP’s, domains, filehashes, URL’s etc.) to operational and strategic TI like threat actor motivation, TTP’s, infrastructure, and security reports.
Indicators of compromise (IOC’s) are the most actionable form of threat intelligence in the context of a SIEM solution as they can be used for matching with event data. Microsoft Sentinel offers many ways to import threat intelligence, including the Threat Intelligence – TAXII and Threat Intelligence Platforms data connectors.
Microsoft Sentinel is making continuous investments in threat intelligence to make the import, management and dissemination of TI simple. Today we are announcing several new TI capabilities in Microsoft Sentinel.
Microsoft threat intelligence matching analytics
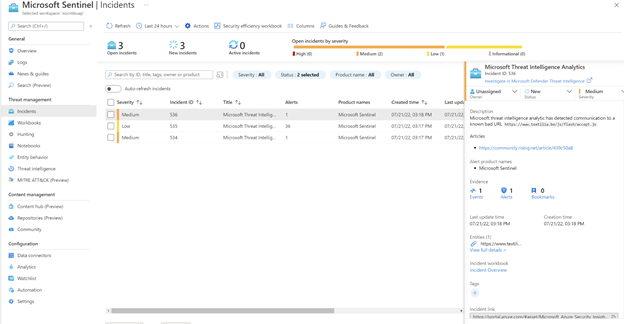
Microsoft Sentinel provides the capability to reference premium threat intelligence data produced by Microsoft for detection and analysis using the Microsoft threat intelligence matching analytics. This analytic rule matches your logs with Microsoft’s TI and generates high fidelity alerts and incidents with appropriate severity based on the context of the log. For example, if a match is received with firewall logs and it is “allowed” traffic, high severity is assigned to the incident and if it is “blocked” traffic, low severity is assigned to the incident. Once a match is generated, the indicator is published to your threat intelligence repository in Microsoft Sentinel.
In our blog “Microsoft Threat Intelligence Matching Analytics” dated July 27, 2021 and “Microsoft Threat Intelligence Matching Analytics: IP Detections” dated June 16, 2022 we stated that this matching analytics matches IP and domain indicators from Microsoft with CEF, DNS and Syslog events. Today we are announcing the addition of data from Microsoft Defender Threat Intelligence (MDTI) to this analytic. MDTI is a dedicated threat intelligence portal available from August 2, 2022 based on the internet-mapping capabilities from our acquistion of RiskIQ a little over a year ago.
Indicators generated by MDTI can now be used for matching with CEF events. Many of the indicators from MDTI come from articles published in the MDTI portal. The incident will have the link to the article in MDTI for additional context during investigation.
Import of indicators from a flat file
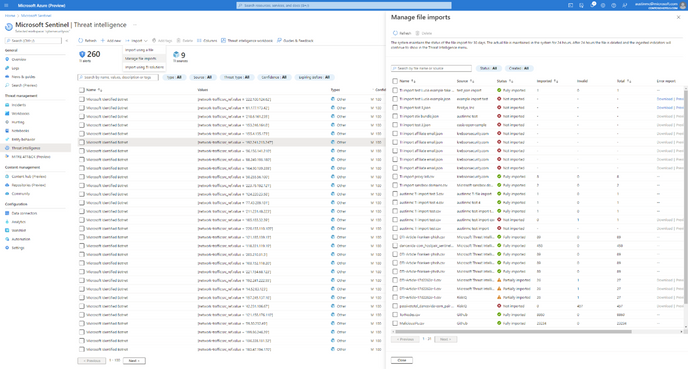
Although STIX/TAXII is the industry adopted standard for sharing threat intelligence data, a lot of threat intelligence sharing still happens across emails and other informal channels during an ongoing investigation. To import these indicators into Microsoft Sentinel, we are announcing a new capability that allows you to import indicators from a flat file in CSV or JSON format.
Microsoft Sentinel provides easy to use templates for you to quickly import your indicators of compromise. Once imported, these indicators get added to your threat intelligence repository in Microsoft Sentinel and can be used for matching with event data using analytic rules, investigation, hunting, and automation. These indicators show up both in the ThreatIntelligenceInidcator table of log analytics as well as in the Threat Intelligence menu of the product.
For step-by-step instructions on how to import threat intelligence indicators from a flat file and manage your imports in Microsoft Sentinel, follow the documentation here.
Conclusion
Hopefully, this article will help you in exploring the new threat intelligence capabilities within Microsoft Sentinel. Over the coming months, you will see additional threat intelligence features added to Microsoft Sentinel as we continue to invest in this critical area of the product.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.