- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Speed up time to detect and respond to user compromise and limit breach scope with Office 365 ATP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Attackers are driven by the desire to cause damage or build their brand. They focus on gaining access to sensitive data to expose it, use it, sell it or hold it for ransom. Or they focus on impacting critical infrastructure – whatever will increase their bottom line, be it financial gain or notoriety. Regardless of their goals, attackers often look to achieve them by first gaining a foothold in the organization through a compromised user, device, or application. And then exercising a variety of steps in the ‘kill-chain’ of their attack to achieve their intent.
A compromised entity in an organization can therefore have serious repercussions. And the longer a compromise goes undetected, the larger the potential for widespread impact and cost to the organization, their customers, and partners. Early detection and remediation of compromise is therefore critical to limit the scope of a breach.
To speed-up that time to detection, limit the scope of the breach and help security teams more effectively and efficiently detect and respond to compromised users, I’m excited to announce the preview of new enhanced compromise user detection and response capabilities in Office 365 ATP
Let me give you a quick look at what these enhanced detections look like, the alerts we raise in the Office 365 Security Center and the insights and powerful automation we offer security teams to investigate and respond to end-user compromise to limit the spread of the attack across the organization.
Figure 1: Office 365 ATP auto-investigation into user suspected of being compromised
Improving detections across the kill chain
In the past few years, attacks targeting users using identity-based attacks, like password spray attacks, or social engineering attacks, like phishing, to try and compromise credentials has become increasingly common and sophisticated. For instance, over the past year across Office 365 we’ve seen a 60 percent increase in phishing attacks.
Attackers target users to land their exploit and then look to expand their attack scope. They compromise users and then leverage the victim’s contacts, accessible resources, applications they use, and more, to launch a variety of internal attacks to spread across the organization. These can include internal phishing campaigns orchestrated through emails and other collaboration tools to target other users, systems and data repositories inside the organization or in partner organizations.
Internal detections of such attacks are therefore a key piece of an organization’s protection and detection strategy. Paired with advanced investigation and response mechanisms, this can help ensure that compromised entities are detected quickly, and the breach does not prove too costly.
The attacker’s activities when using a compromised account are often atypical or anomalous relative to the user’s regular behavior. For instance, there is no good reason for trusted users to be sending any phish or spam emails to other recipients. Being able to detect anomalies in user activity is therefore a key signal source for detection. Office 365 ATP is able to detect these anomalies in email patterns and collaboration activity within Office 365.
The attacker may or may not trigger a suspicious login. And often suspicious login alerts, when viewed in isolation can be noisy. However, by pairing these O365 detections with other identity and endpoint-related suspicious signals we can greatly enhance the speed and accuracy of compromise detection
We’ve also built-in automation to investigate the source of the breach, determine if there are other potentially impacted users, and to the analyze the impact of the compromise. Further recommendations are then provided the security teams to remediate and ultimately reduce their attack surface.
Alerting security teams to potential compromise
A common attack technique is to use a compromised account to ‘spray’ a phishing campaign and target other users. The compromised mailbox is used to send phishing messages to a large number of users inside and outside the organization with the intent of compromising these other recipients.
When Office 365 detects suspicious email or anomalous activity patterns it will raise an alert to call out the suspicious activity. For example, figure 2 below shows an alert that was raised because of suspicious sending patterns of a user.
Figure 2: Office 365 alert raised when suspicious email sending patterns were observed for a user
Office 365 also allows security teams to define sending limits for users in advance to limit the scope of a possible breach. As shown in Figure 3 below, the admin can set hourly and daily sending limits for users and also specify the action to take if those limits are hit. And when these thresholds are breached, admins are alerted.
Figure 3: Office 365 policy for internal and outbound email sending thresholds configuration with notification options
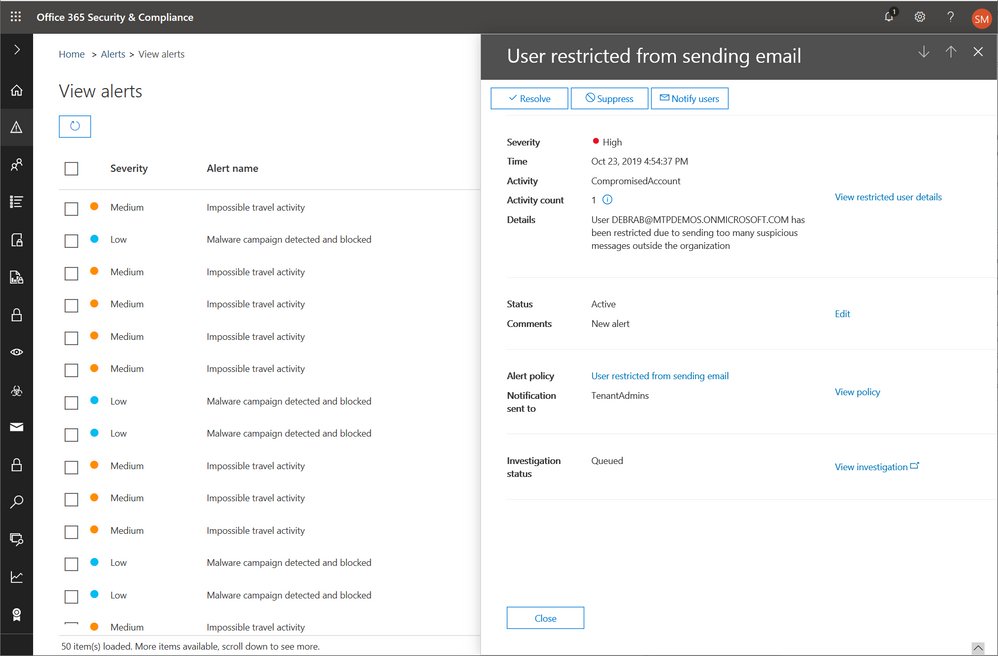
In some cases, as shown in figure 4 below, Office 365 will automatically restrict the user from sending any more emails and raise the alert below.
Figure 4: Office 365 alert when user is restricted from sending email detecting compromise
These alerts are meant to raise the awareness of security teams so they can quickly contain and investigate the issues.
Containing and investigating the threat
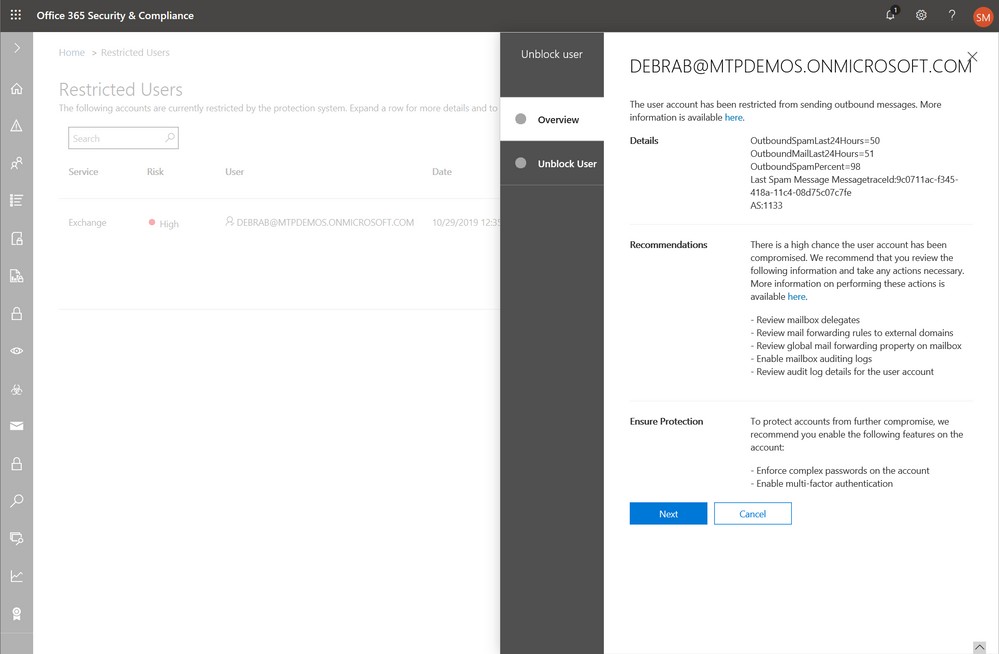
As called out above, there are cases where Office 365 will automatically block the user’s ability to send further emails to contain the impact. While an alert is raised, the user is also put on a “restricted” user list, as shown in figure 5 below. Admins can then unblock the user’s ability after investigating the user and assessing impact of the compromise.
Figure 5: Users suspected of compromise and therefore restricted from sending email
O365 also offers recommendations to guide security teams through the process of unblocking a user manually. As shown in figure 6 below, specific recommendations are offered to check relevant user settings and activity logs to assess the potential impact of the breach. And specific remediation steps are recommended to ensure that the user is secured before re-enabling mail flow. O365 ATP P2 customers get the benefit of automation (covered in next section) where these investigation steps automatically carried out by the system.
Figure 6: Admin workflow for mitigating and containing compromised users detected by Office 365
Automating investigation and response
Office 365 ATP P2 customers get the added benefit of automation to help with quick investigation and response. When any of the above alerts are raised, they are automatically investigated using detailed, built-in playbooks to determine the scope, impact and cause of the attack. The playbook intersects signals from identity sources, mail flow, DLP and mailbox settings and other O365 events to investigate and analyze the alert.
Doing the analysis above quickly and comprehensively is critical to reducing the cost of breach to the organization and preventing data theft or exfiltration. And automating the process achieves this.
Figure 7: Office 365 ATP auto-investigation into user suspected of being compromised
Figure 7 below shows the automatic investigation results summary. The other tabs in the investigation offer up more details. The ‘Alerts’ tab, includes the other alerts aggregated into the investigation. The ‘Email’ tab includes details of how the automation looked for other emails matching the suspicious emails sent to see if there were other users impacted. The analysis also includes looking for the source of the compromise. The ‘users’ tab highlights other user activity anomalies detected. All the detailed steps of the playbook are captured in the ‘Log’ tab.
These details capture a comprehensive analysis of the alert to determine cause, scope and impact. And offer ways for security teams to verify the investigation steps and results should they choose to. Best of all, because it is the system doing this analysis, it can save security teams a lot of time and effort.
The ‘Actions’ tab, shown in figure 8, captures the list of recommended actions for the security teams to take based on the investigation results. This gives security teams the opportunity to review the recommendations prior to taking action.
Figure 8: Office 365 ATP recommended response actions as a result of the investigation.
Try if for yourself!
These new updates are available in preview worldwide. If you’re not signed up for Office 365 Advanced Threat Protection, check it out here to experience the full security benefits and built-in protection, detection, response and automation capabilities of Office365 ATP.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.