- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Maintain visibility more effectively with updates to alert policies and insights
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
We have heard from customers that in today’s modern workplace and threat landscape, alerts and insights are a key tool to maintain visibility and control in your environment. Office 365 alert policies and insights in Security & Compliance Center are effective tools for organizations to detect threats, monitor anomalous activities and enhance protection in Office 365. This month, we are rolling out new capabilities to enhance your alert and insight experience in Office 365.
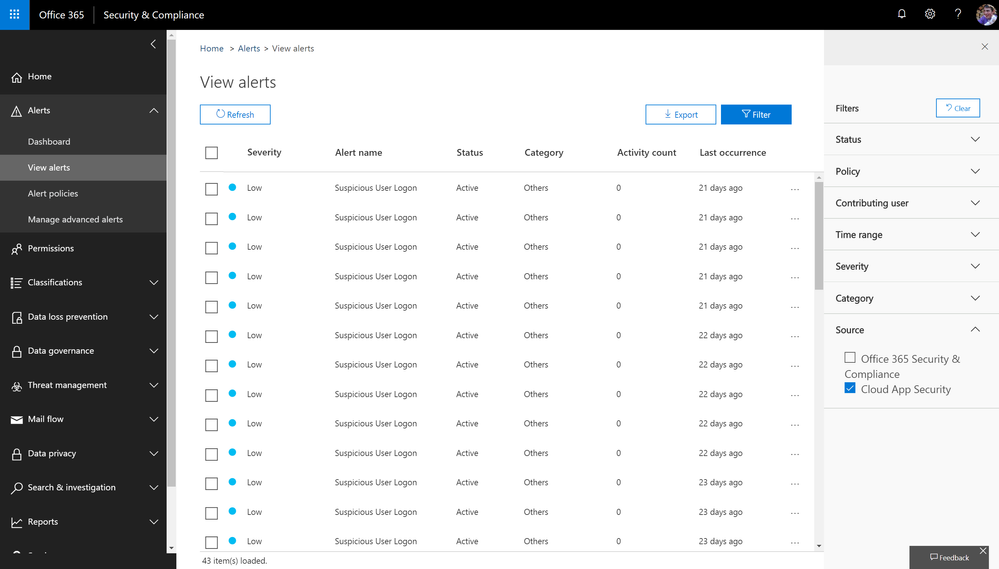
Consume Cloud App Security alerts in Office 365 Security and Compliance center
Microsoft Cloud App Security alerts related to Office apps and services are now available in the Office 365 security and compliance center on the view alerts page. With the addition of these alerts in the compliance center, you now have a central view within one portal. In addition, these same alerts are now available via the Management Activity API.
For more details, please refer to this section in documentation.
Alerts signal available in Management Activity API
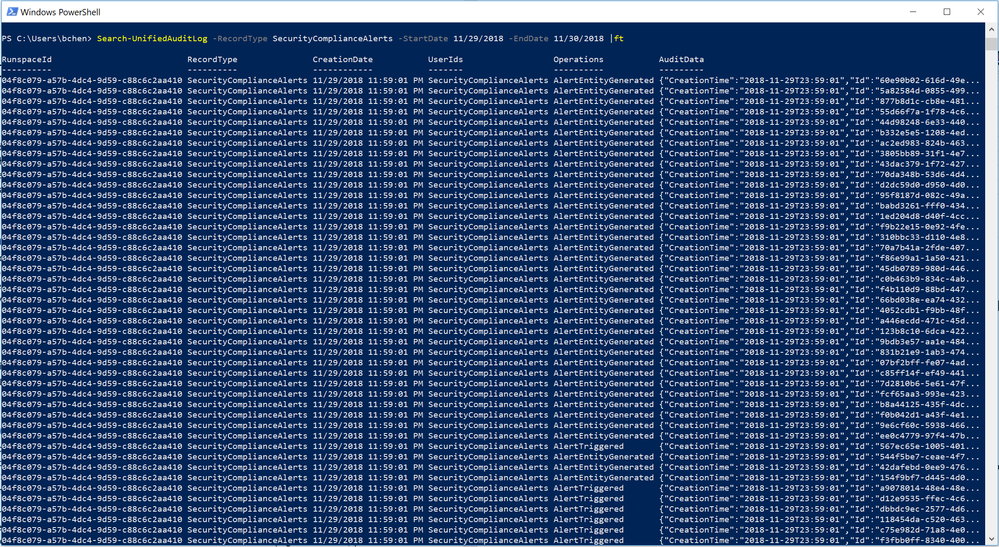
Availability of the alerts signal in the Management Activity API has been one of the top feature requests from both customers and partners. Starting now, Office 365 Security & Compliance Alerts can be retrieved from Management Activity API as a signal. This means that you can now consume Office 365 alerts in your own way by simply integrating it with your SIEM or self-created solution.
Meanwhile, this also means that these signals can be searched from “Search-UnifiedAuditLog” for Cmdlet based log access.
For more details, please refer to the schema documentation for Office 365 Security & Compliance alerts in Management Activity API.
Manage access to alerts with role-based permissions
Admins with various roles come to the Security and Compliance center to consume alerts. Until now, the permission for viewing alerts has been universal across the entire organization, creating a challenge for access to alerts for specific scenarios such as data loss, or privileged access. As we expand the scenarios that alert policies support across Security & Compliance, the necessity for a more granular permission model emerges. This month, we will start to roll out the role-based access to alerts. For example, a Compliance admin will no longer have permission to see Threat management alerts in “View alerts” page. Read more about this update here.
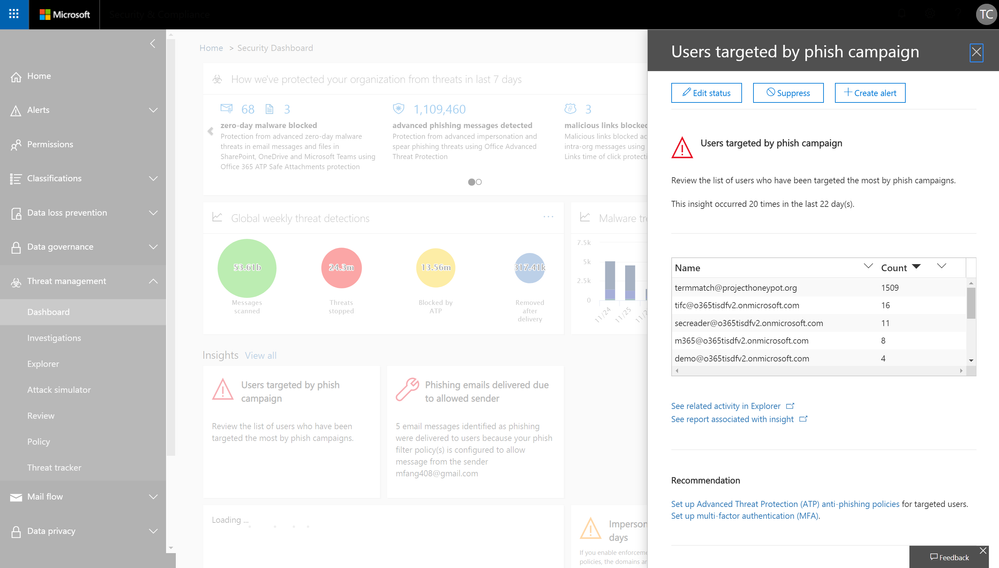
Insights signal available in Management Activity API
In various places in Security & compliance Center, Office 365 provides you with insights about potential threats or configuration issues that we have identified on your behalf, such as “Users targeted by phishing campaign” or “Spam mails delivered due to allowed IP”, along with actionable recommendations for you to resolve or mitigate these issues.
To date, we have introduced about 30 such insights. And now, we are excited to share that these insight signals can also be retrieved via the Management Activity API. This update will start to roll out later this month.
Alert policies based on S&CC insights
Along with the availability of insight signals in Management Activity API, we are also allowing admins to configure alert policies and receive email notifications based on these insights from S&CC. Certain insight based alerts will be rolled up as on-by-default alert policies.
This capability is also starting to roll out later this month. Check back for updates on related documentation.
- Binyan Chen, Sr Program Manager, Microsoft 365 Compliance Solutions
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.