- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Introducing the integrated Microsoft Threat Protection solution (public preview)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Every day, attackers compromise endpoints, identities, and email to infiltrate and quickly expand their foothold in an organization. Customers need protection across these attack vectors to defend against evolving threats. Microsoft Threat Protection is an integrated solution that’s built on our best-in-class Microsoft 365 security suite: Microsoft Defender Advanced Threat Protection (ATP) for endpoints, Office 365 ATP for email and collaboration tools, Azure ATP for identity-based threats, and Microsoft Cloud App Security (MCAS) for SaaS applications.
Within the suite we’ve been expanding our threat detection and automated investigation and response capabilities, as well as adding cross-product visibility, with additions such as automated incident response in Office 365 ATP, integration of MCAS and Microsoft Defender ATP for deep insight into cloud app usage, integration of Azure ATP with Microsoft Defender ATP, and more.
Starting today, across the threat landscape security teams can correlate alerts to focus on what matters most, automate investigation and response and self-heal affected assets, and simplify hunting for indicators of attack unique to an organization. They can also use Microsoft Threat Protection to centrally view all detections, impacted assets, automated actions taken, and related evidence.
Move from alerts to incidents
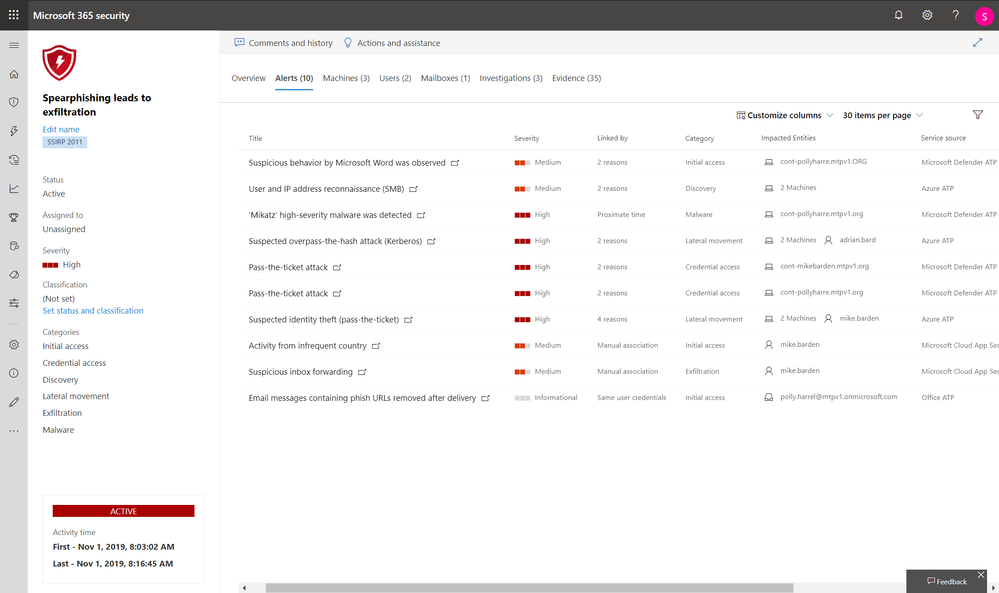
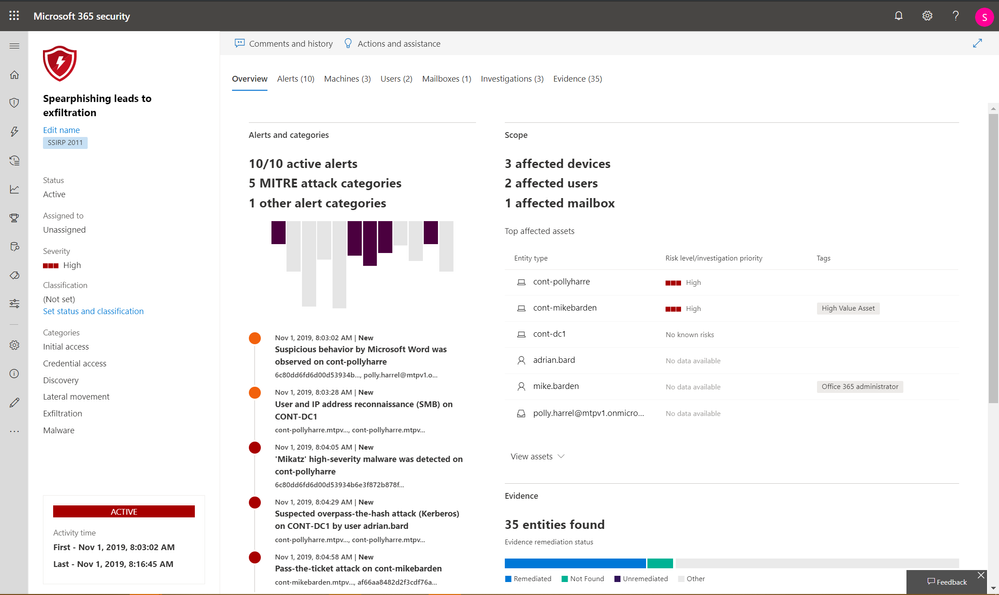
We are introducing the concept of “incidents,” previously available only for endpoints. These incidents correlate alerts across threat vectors to determine the full scope of the threat across Microsoft 365 products.
For example, we can correlate the following attack sequence: Office 365 ATP observes a malicious email attachment. That attachment contains a weaponized Word document that is opened on the endpoint and observed by Microsoft Defender ATP. The attack then launches queries to the domain controller in search of user accounts to abuse, which is observed by Azure ATP. And, finally, corporate data is exfiltrated to a personal OneDrive account, which is observed by Microsoft Cloud App Security.
All related alerts across the suite products presented as a single incident (alerts view)
Cross-product incident (Incident overview)
Automate threat response
Critical threat information is shared in real time between Microsoft Threat Protection products to help stop the progression of an attack. The central Microsoft Threat Protection logic orchestrates and triggers actions on the individual products. This includes blocking malicious entities and initiating automatic investigation and remediation.
For example, if a malicious file is detected on an endpoint protected by Microsoft Defender ATP, it will instruct Office 365 ATP to scan and remove the file from all e-mail messages. The file will be blocked on sight by the entire Microsoft 365 security suite.
Self-heal compromised devices, user identities, and mailboxes
Leveraging the capabilities of the suite products, the integrated solution uses AI-powered automatic actions and playbooks to return all impacted assets to a secure state. Within the portal security teams can use the Action Center to centrally view results of all automated investigations and self-healing actions and approve or undo specific actions.

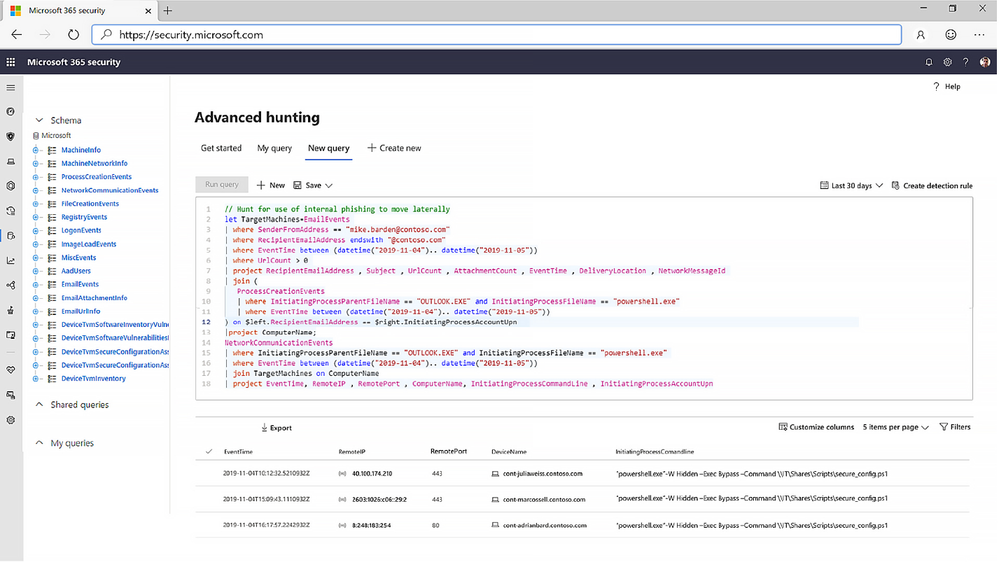
Cross-product threat hunting
Security teams can leverage their unique organizational knowledge like proprietary indicators of compromise, org-specific behavioral patterns, or free-form research to hunt for signs of compromise by creating custom queries over raw data. Microsoft Threat Protection provides query-based access to 30 days of historic raw signals and alert data across endpoint and Office 365 data.
Security professionals and customers with Microsoft 365 Security E5 and all M365 E5 licenses are invited to explore the integrated Microsoft Threat Protection solution public preview. (Eligibility Requirements).
Visit http://aka.ms/EnableMTP today to learn more.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.