- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Gain transparency of your IaaS solutions with Microsoft Cloud App Security (Part 1)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In this 2-part series we will discuss the security risks that IaaS solutions can pose on your organization and explore how Microsoft Cloud App Security, Microsoft’s Cloud Access Security Broker (CASB), can help you detect vulnerabilities, govern existing security gaps and ensure ongoing visibility into the exposure and overall security of Amazon Web Services (AWS) and Azure environments. In part 1 we will take a closer look at AWS and more specifically S3 buckets.
AWS S3 buckets continue to be a security gap in 2018
In 2018, we saw major news items about misconfigured AWS S3 buckets nearly every month. One of the most recent cases was the misconfiguration by a Virginia-based campaign and robocalling company, which left hundreds of thousands of voter records publicly exposed. This year alone, these misconfigurations have led to more than 50 million exposed records.
In these cases, the exposure was not a result of cyber-attacks, instead these companies misconfigured their AWS S3 buckets, leaving highly sensitive data like scanned IDs, user accounts and passwords, vulnerable and publicly accessible.
Understanding the risk for exposure in S3 buckets
AWS S3 buckets provide scalable cloud storage, but the ease of management and deployment can also be a pitfall for the security of this solution.
S3 buckets are set to “private” by default when they are created, but for varying reasons AWS admins will configure to expose data publicly and make it accessible through the web. A good example is the hosting of a website, where a bucket must have public read access to make the website accessible to anyone. In the cases of the recent headlines however, this configuration was done mistakenly.
One of the liabilities is that the URLs of S3 buckets can be guessed, because the bucket names are chosen by the user and if the right URL is known, anyone with access to the internet can retrieve the data that was made publicly accessible. For example, if a bucket is named “Contoso”, an attacker only needs to guess http://contoso.s3.amazonaws.com to gain access.
Detect and Protect your cloud storage with Microsoft’s CASB solution
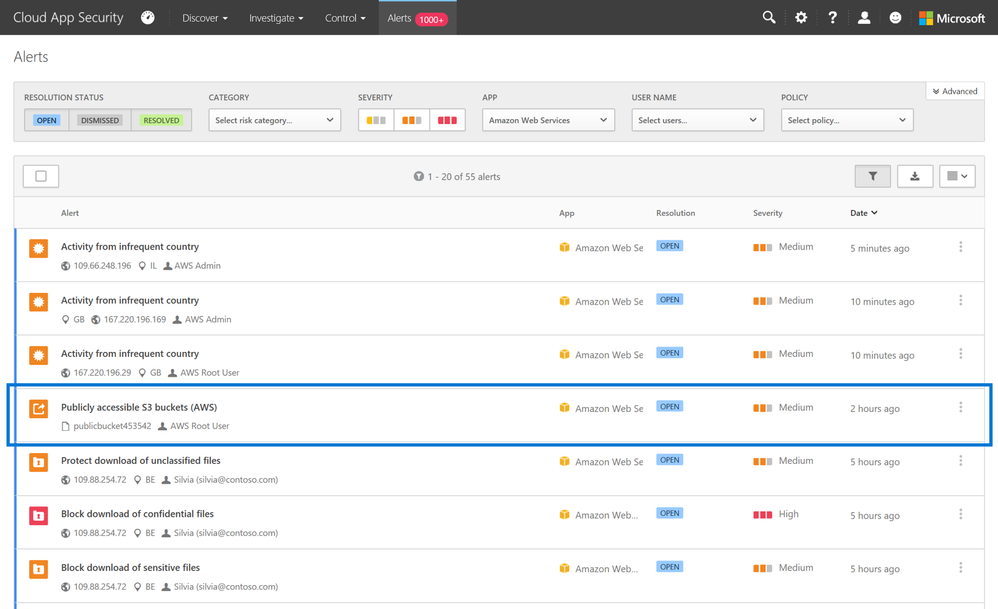
Microsoft Cloud App Security (MCAS) is a CASB solution that gives you visibility into- and provides controls for your environment of cloud apps and services. Using the AWS App Connector, you can gain insights into the activities across your environments, such as log-ons or administrative activities.
For AWS, Microsoft Cloud App Security can also detect publicly exposed S3 buckets and you can leverage MCAS to ensure the right access levels for your AWS S3 buckets are in place and help prevent the exposure of your data. When open S3 buckets are detected, you can choose to either automatically apply governance actions, or to evaluate the details of an alert, before adjusting the access levels manually.
More info and feedback
Learn how to connect Microsoft Cloud App Security to your AWS environment with our detailed technical documentation. Don’t have Microsoft Cloud App Security? Start a free trial today!
As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.
Sources:
Octoly AWS S3 exposure (February 2018)
MBM AWS S3 exposure news (March 2018)
Localbox AWS S3 exposure (April 2018)
L.A. country AWS S3 exposure news (May 2018)
Honda India AWS S3 exposure (June 2018)
Virginia based campaign and robocalling company (July 2018)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.