- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Re: Set 'Account lockout threshold' to 1-10 invalid login attempts
Set 'Account lockout threshold' to 1-10 invalid login attempts
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 05 2022 09:45 AM - edited May 05 2022 09:51 AM
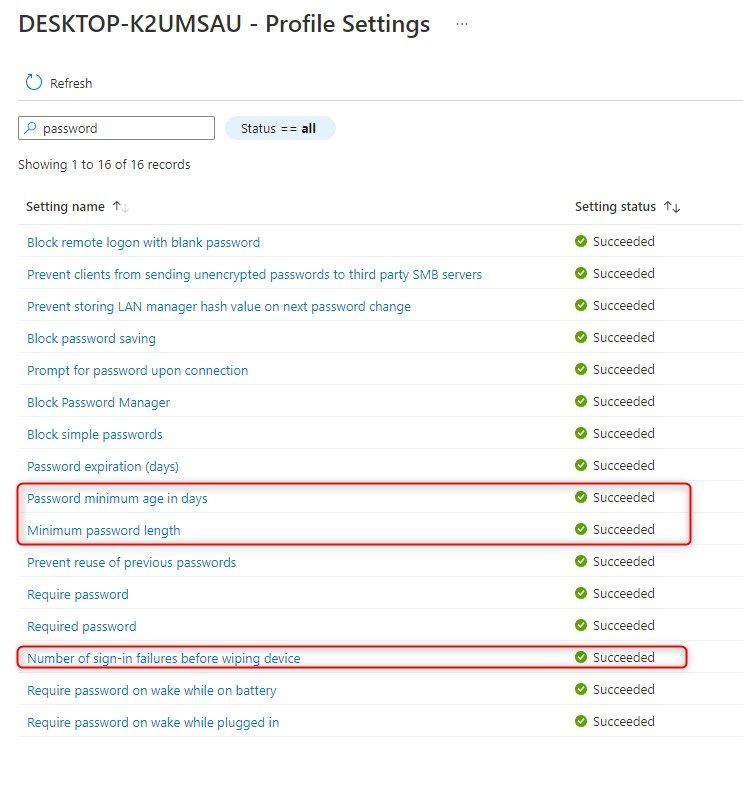
In the security baseline for Windows 10 and later I have configured the Device Lock part.
Number of sign-in failures before wiping device = 10
I have also this set on the Device Restriction policy under Password.
Number of sign-in failures before wiping device = 10
Now in security recommendation on my test device I still get the recommendation to Set 'Account lockout threshold' to 1-10 invalid login attempts.
My question, is this not hitting the same settings?
Same goes for the
Set 'Minimum password age' to '1 or more day(s)'
Set 'Minimum password length' to '14 or more characters'
- Labels:
-
Intune
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 05 2022 02:05 PM
Hi @JimmyWork,
Both the security baseline and the device restriction policies configure the Policy CSP - DeviceLock
- DeviceLock/MaxDevicePasswordFailedAttempts
- DeviceLock/MinDevicePasswordLength
- DeviceLock/MinimumPasswordAge
It's not recommended to configure the same settings from 2 different policies. Or did you have a good reason?
Check the reports (for both policies) to see if the settings are in error. I'm wondering if these settings actually apply successfully because an error in applying these settings could explain the security recommendation message.
Perhaps have a look at this techcommunity post, where I dive a little deeper in Security baselines vs other policies. Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 05 2022 10:44 PM
As long as you set the exact same settings then there will be no issue with the policy's, you will get no error and it will work on the device, I checked Intune logs and registry on the device.
If I look at the security recommendation it refers to this setting.
Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Account Lockout Policy.
This seems not to be found in any policy or OMA-URI available in Intune.
Any suggestion other then creating a remediation script?
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/account...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 05 2022 11:07 PM
Set the following Group Policy:
Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Account Lockout Policy\Account lockout threshold
To the following value: Between 1 and 10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 06 2022 12:50 PM
@JimmyWork this is interesting. The only thin I can find about the GPO you are referring to (Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Account Lockout Policy\Account lockout threshold) and it's azure counterpart is Azure Smart Lockout. Have a look at this doc and in particular "verify on-premises account lockout policy" This is where they refer to your GPO Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Account Lockout Policy.. A little below that "Manage Azure AD smart lockout values"
So...If I had to guess, it looks like that the security recommendation is not about your baseline or device configuration profile, but about Azure smart lockout. Can you have a look at that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 06 2022 12:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 06 2022 01:42 PM
But this seems more related to On-prem devices and this is a fully cloud device so not sure why security recommendations are bringing this up as there is currently no way to set this in Intune
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 07 2022 01:07 AM
@JimmyWork I agree. It does look like this does not exist with MEM yet. I think your best bet is to reach out to Intune support at this stage (frustrating....) I'm not sure what they can do... besides point you in the direction of a remediation script (which you already know), but who knows... I do hope that custom ADMX/ADML import (in development) will become available with the next Intune release because I think that can solve your problem.
Please keep us informed about your findings. Sorry couldn't help you out yet, but if I do have news to share, I'll give an update here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 07 2022 01:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 12 2022 11:40 AM
SolutionReceived the following from MS support.
(I have reported them as inaccurate recommendations)
We can confirm that the configuration options at the moment are not available to set from Intune. This looks like an invalid recommendation originating from Microsoft Defender for Endpoint.
Right now in Intune, the ones below are the settings most similar to the account lockout threshold policy (screenshots with descriptions):
Device configuration profiles (Win 10) > Templates > Administrative templates > Computer Configuration > System > Trusted Platform Module Services
- Standard User Individual Lockout Threshold
- Standard User Total Lockout Threshold
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 12 2022 03:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 25 2022 11:58 PM
Yep discovered the same thing, a bit stupid that their cloud managed anti-virus, reporting to their cloud managed security platform requires changes made to group policy which isn't available in their cloud managed device platform....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 19 2022 04:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 19 2022 05:26 AM - edited Aug 19 2022 05:32 AM
Did you check the security center? Will this apply to that settings because security center is pointing on other settings.
Device lock is it in the security baseline or where did you find this? Just to be clear the setting will not hit the correct configuration. Device lock will not set lockoutthreshold that Secure Score recommends.
Just checked and we always had Device Lock set and this was why I reported it to MS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 26 2023 02:25 AM
Still having some security recommendations that I cannot get rid of because Exposure Score recommendations is looking for GPOs to be in-place...
Set 'Account lockout duration' to 15 minutes or more
Set 'Reset account lockout counter after' to 15 minutes or more
Set 'Minimum password length' to '14 or more characters'
Set 'Enforce password history' to '24 or more password(s)'
Set 'Minimum password age' to '1 or more day(s)'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 26 2023 02:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 26 2023 02:32 AM
Yep...It still shows up in a cloud only environment.
Just reported all that recommendations has "inaccurate".
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 12 2022 11:40 AM
SolutionReceived the following from MS support.
(I have reported them as inaccurate recommendations)
We can confirm that the configuration options at the moment are not available to set from Intune. This looks like an invalid recommendation originating from Microsoft Defender for Endpoint.
Right now in Intune, the ones below are the settings most similar to the account lockout threshold policy (screenshots with descriptions):
Device configuration profiles (Win 10) > Templates > Administrative templates > Computer Configuration > System > Trusted Platform Module Services
- Standard User Individual Lockout Threshold
- Standard User Total Lockout Threshold