- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Re: Restrict email access to Exchange Online
Restrict email access to Exchange Online
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 15 2016 03:15 AM
Hi all,
I have a situation of a customer without an on-prem Active Directory, only using some cloud apps, like Office 365.
They want to block access to (in first place) e-mail on non managed devices. I know I can use Conditional Access policies to set this up for mobile devices (the new Intune MAM) policies, but how can I block access to Exchange Online by using Outlook on non-managed devices? I`ve been reading articles about this, but that always ends up using ADFS and that is not possible for this customer.
The customer is running Windows 7 and 10, but t is ok if this solution is only going to work with Win10 (Azure AD joined/ Intune enrolled), than we upgrade al devices.
Is there anybody to advice me how to set this up, or point me in the right direction?
Thank you!
Regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 15 2016 07:17 AM
Hi Peter,
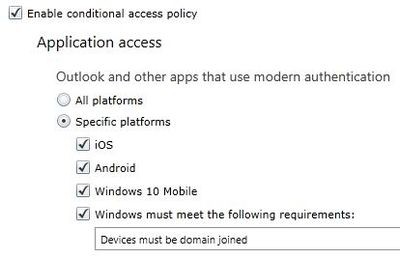
Have you tried this setting within Intune?
If you do not want to cover all platforms with generic policy you can also select specific platforms like below:
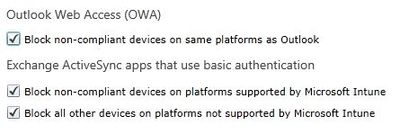
You also get a way to block OWA and ActiveSyn clients:
This will cover non-domain joined windows 7 also.
Let me know if this helps.
Regards,
Jasjit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 16 2016 01:30 AM
Hi Jasjit,
Thanks for the reply.
Yes tried that policy before, blocks OWA access and the use of the buildin mail app on Windows 10, but it still gives me access to Exchange Online by using Outlook 2016.
Also tried Conditional Access from the new Azure portal under Aure AD (in preview), same situation; blocking OWA and the buildin app, but still allows access via Outlook.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 16 2016 02:31 AM - edited Dec 16 2016 03:01 AM
I have enabled modern authentication for Exchange Online.
It now shows me a message access is blocked when I try to connect using Outlook, but is does that on domain joined Win10 devices as well.
I`m using Conditional Access from the new Azure Portal (https://blogs.technet.microsoft.com/enterprisemobility/2016/12/15/conditional-access-now-in-the-new-...).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 16 2016 04:23 AM
Hi @Peter Klapwijk,
Let me try that in my lab setup - that kinda sounds strange and I would think MS would have thought of this scenario you are trying to achieve - which is a common ask from other customers too I presume.
I will get back to you and let you know.
Regards,
Jasjit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 16 2016 07:03 AM
Hi @Jasjit Chopra Yes it sounds very strange. Was happy Outlook was blocked at an Win10 device which is not domain joined. But than I cleared all the credentials on the domain joined machine and setup Outlook again and it is now blocked as well.
Thank you for your time testing this setup!
regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 16 2016 09:38 AM
Ideally you should not test it on the same machine by clearing creds - but nonethelless will test and let you know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 23 2017 07:31 AM
Hey Peter,
We are trying to accomplish the same thing but from what we found you need ADFS. The problem with Conditional Access is it blocks clients that use Modern Auth. If the client tries using basic auth (Outlook 2010 and older only use basic and Outlook 2013 / 2016 can use modern or basic) it will get through. We are working on blocking basic auth w/ADFS externally to shore up this loop hole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 24 2017 05:19 AM
Hi @Chris Eckel
This is an cloud only customer. So part of my solution for this was blocking basic auth for Exchange Online. In this situaton that was no problem, customer is running only Outlook 2013/ 2016. Till now it is not yet implemented to the customer his tenant, was just running this in a lab.
But in your situation, with an On-prem AD, if you don`t want to use ADFS, have a look at the New Azure Portal. Below Azure Active Directory you find Conditional Access. You can create an policy to just allow Exchange Online access to Domain Joined devices, filter it on Windows devices and you can setup another solution for your mobile devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 03 2017 04:36 AM
The CA policies get you most of the way there - but I beleive you still need to set the ADFS claims rule to block the down-level clients. We found you still need basic to ensure mobile clients using EAS can connect and retireve content. Of course, if you are using Outloof for iOS/Android only, which no longer relies on the EAS channel, you could implement MAM+CA in this case.