- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Re: Prevent Teams to save files to Dropbox on iOS and Android
Prevent Teams to save files to Dropbox on iOS and Android
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 11 2021 12:41 AM - edited Sep 11 2021 12:51 AM
Hello!
All of our mobile devices are Azure AD registered.
We have configured two app protection policies, one for iOS and one for Android.
You can find the configuration of the app protection policy below. The problem is, that the users can still save files from Microsoft Teams to Dropbox.
How can I prevent the users to save files from MS Teams to private storages?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 11 2021 08:36 AM
You may consider AIP, take a look at:
https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection
Take a look at:
https://docs.microsoft.com/en-us/microsoft-365/solutions/configure-teams-three-tiers-protection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 12 2021 01:28 AM - edited Sep 12 2021 02:06 AM
Hi
Are you 100% sure the devices has received the app protection policy? Normally when configuring the save copies to block but looking at the ms docs
https://docs.microsoft.com/nl-nl/mem/intune/apps/app-protection-policy-settings-ios?WT.mc_id=Portal-...
This settings is supported by Microsoft Excel, OneNote, Outlook, PowerPoint en Word. I guess I am missing teams. I am noticing the same thing..
UPDATE: decided to write a blog about this issue and which options you have to block it.
I guess for now. Compliance policy to block the device when dropbox is installed... or using MCAS and sanction dropbox as non approved app...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 12 2021 02:39 AM
@Rudy_Ooms_MVP Hi Rudy! First thank you for your reply. The app protection policy is doing the stuff, for example the apps in scope require the pin/biometrics to start them and also on iOS i cannot save the files direct to the Files app (ootb iOS app for iCloud and local storage).
The problem is, that I can still save the files from Teams on DropBox, Google Drive etc.
Is there any way to check what kind of policies are working when opening an app on a mobile device? (like the "what if?" tool for the conditional access policies)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 12 2021 02:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 12 2021 03:59 AM - edited Sep 12 2021 10:30 AM
I did a blog about mam sometime ago ... https://call4cloud.nl/2021/03/the-chronicles-of-mam/
But just like you experienced.. when dropbox is installed you can copy file to it... even when its app protection policy is on block...
You could configure the send org data to other apps to none... but ... i guess that's something you don't want
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 12 2021 10:50 PM - edited Sep 13 2021 12:36 AM
I tested some things last afternoon
Policy managed apps: Only allow sending org data to other policy managed apps --> will give you the possibility to send data to whatsapp/dropbox even when all the docs are telling us it shouldn't ?
Configuring that option to none.... removes all the options.... (like expected) The same goes with the onedrive app.... setting the send data to ... to none... removes all options...
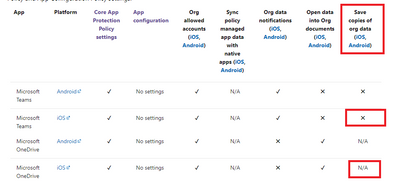
I guess we need to climb up the ladder to find out why...
It looks like this picture from the ms docs tells us why ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 13 2021 05:24 AM - edited Sep 14 2021 02:11 AM
For your information :)...
When configured: Policy Managed Apps --> dropbox is visible and you are able to save it to dropbox. But at the same time the data is encrypted... so the data is "worthless"
If you configured policy managed apps with os sharing on mdm enrolled devices your data will be unencrypted and you could save it to dropbox
If you configured Policy managed apps with Open-In/Share filtering the option to save to dropbox is gone.... like you would expect with policy managed apps... :)
App Protection: Attack of the OS-Sharing - Call4Cloud