- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Re: No user affinity - conditional access
No user affinity - conditional access
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 17 2021 09:45 AM
I have a conditional policy that require the device to be compliant. But I have devices that have no user affinity so there is no compliance evaluted. Will they still fit in under compliance, so the CA policy don´t kick them out as they don´t have any compliance evaluated?
- Labels:
-
Intune
-
Mobile Device Management (MDM)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 18 2021 07:00 PM - edited Feb 18 2021 07:01 PM
When you say "No user affinity" do you mean, they are NOT logged in by any user or logged in with a common account like "Device Enrollment Manager (DEM)"?
In both these cases, CA will not be evaluated, so compliance is not calculated on them due to which it is not considered non-compliant.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 18 2021 10:52 PM
So all devices that have a system account should not be part of conditional access polices? - there is no workarround on this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 19 2021 04:21 AM
Can see that my devices with a system account fails the compliance, so also fails the conditional access.
So how can I either add those devices to a compliance policy - or how can I exclude them?
I could easily make a device group, but this will not work as exclusion in Conditional access, as it must be user based. And the user "system account" is not a azure account, so wondering what can be done.
Guess that also non-user devices, should be able to be verified with compliance ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 19 2021 12:05 PM
1) Please clarify "System Account" here. Did you mean Windows system account? if not what is it?
2) From your description, you have targeted CA policy to user group. Is it correct?
3) Which OS are you focusing here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 22 2021 06:12 AM
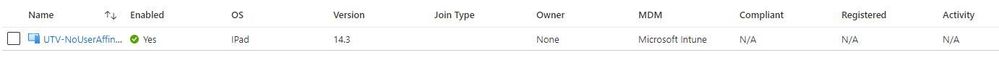
@rossonero Hi I have just been doing some testing with Intune, no production environment. I have an iOS device with no user affinity. I can assign a compliance policy to the device in Endpoint Manager and have it report as compliant. However, under devices in Portal Azure, it doesn't report as compliant. Is this the same scenario you are having?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 22 2021 07:21 AM
Hi @rossonero
Can you elaborate what exactly are you trying to do?
I think devices without users will not be impacted by Conditional Access even if their group is added as Target in the policy.
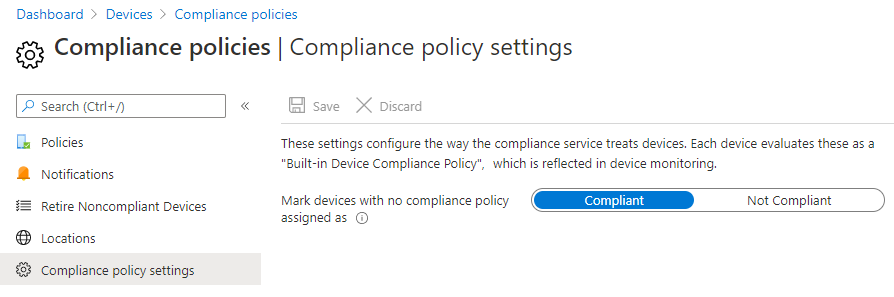
You can make those device appear as compliant by configuring the build-in compliance check, find Docs here: Device compliance policies in Microsoft Intune
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 22 2021 12:28 PM
Yes exactly that is the issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 25 2021 12:50 AM
Hi @Alo Press
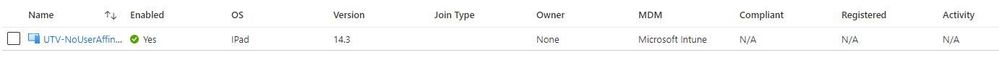
what confuses me in this scenario is why a device with no user affinity can show as Compliant in Endpoint Manager Center if it has a compliance policy assigned, and the same device will still show as N/A in compliance in Portal Azure.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 25 2021 01:58 AM - edited Feb 25 2021 02:05 AM
@ThoDeutschmann Hmm, right. Ok, I think I get the core of the issue now and here is my humble hunch on it. First Azure AD displays more states for devices than Intune and comes into play before even getting your devices enrolled - that can be the N/A state that you guys are reporting. My take utilises credentials but the logic itself should be similar to unaffiliated devices. Read more about the Device Identity here and about Azure AD registered devices here.
So to first recreate the N/A state for a device you can do the following with a new device:
- Install Company Portal on mobile device
- Sign into the Company Portal app but do not enrol
- From Azure AD > Devices, you can see a device without Compliance
The potential fix may vary depending on the exact scenario (and there are more I am sure):
- If the device isn't already managed, enrol it into Intune
- After enrolment make sure that you do not get a notification under your Devices menu
- Sync the device and note the change in Azure AD device list
Although this scenario applies to new devices it should have similarities to the existing devices, I just checked my test tenant and in there I did have a device that reported a similar state, where in Azure AD I had a N/A compliance and in Intune it was ok.. to dig deeper I opened my impacted device and checked the Company Portal app, it was reporting not being Registered even though my device was already in Intune.. unfortunately I was unable to get a screenshot of that before it resolved itself and that also resolved the incorrect reporting in Azure AD.
Alternatively you can check if the devices that you have in N/A state are actually the devices you have in Intune, in some cases there can be multiple entries for one device, this can be verified by comparing the Azure AD Device ID for AAD and Intune.
And for more destructive testing you could unenrol the device, delete its Intune record and then Azure AD record, most likely the new enrolment would result in both records reporting correct information.
Sorry for the long post, hopefully it helps.