- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Join and manage Windows 10 device in different tenant than home tenant
Join and manage Windows 10 device in different tenant than home tenant
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 22 2022 08:43 AM
Hi,
A customer who owns an International Enterprise, has multiple regional AD forest domains syncing to one Azure AD tenant/ O365. He now has a special request.
The customer would like to join the Windows 10 devices to Azure AD, but to a different tenant than the home tenant, where all users are synced towards.
Is this a possible scenario, where autopilot or self registration (no hybrid join), can join another Azure AD domain than the current tenant where O365 has been configured for all users.
The customer in this case would like to separate device management from the existing tenant.
- Labels:
-
Azure AD Join
-
Intune
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 22 2022 09:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 22 2022 09:19 AM
@andrew1810
Thanks for your answer.
The problem is that regions IT management wish to enroll and administer their own devices in Intune. A role which is currently limited by the global admins as the tenant is mostly managed by one region. It is correct that tagging and granular RBAC could allow them to do this in the same tenant.
However if global admins mistakenly enforce a policy to all devices in Intune, the regions experience impact on their machines and that is what they want to avoid. They have no control whatsoever and now they want to be in control.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 22 2022 09:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 25 2022 08:37 AM
@andrew1810
To clarify the (requested) situation a bit more, I would like to show the current environment and the requested design.
The current situation is as indicated underneath
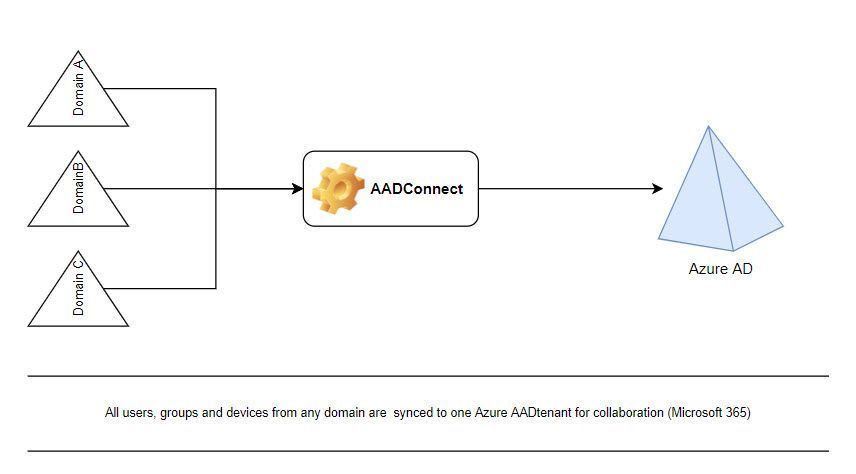
The customer would like to keep the Microsoft 365 which are shared between the domains in the first tenant.
To avoid the Global Admins or Intune administrators to damage endpoints managed for users which are synced from domain C, they would like to have a separate tenant that holds their users and devices. So in other words they would like to join their devices to the 2nd tenant, managed them on the tenant while not removing any functionality built in tenant 1
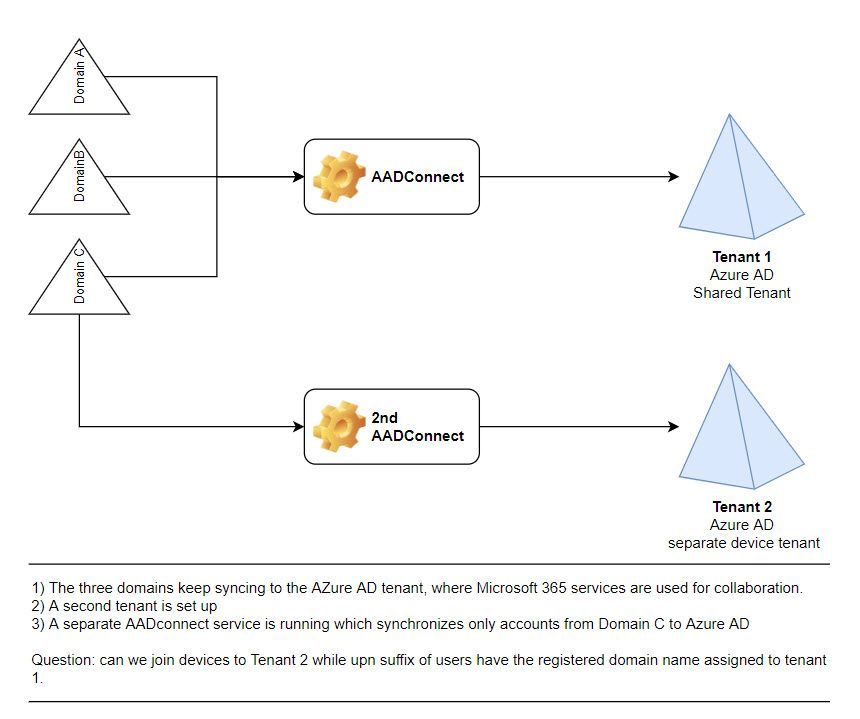
I hope the design clarifies this a bit more.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2022 01:43 AM
@StanMorisse You can't have a custom domain on two different tenants, it won't let you add to a second without removing from the first. You're also restricted to AAD sync to one tenant only.
You could potentially add a new UPN for the extra tenant and then another AAD Connect server pointing to that one, but I have never tried it myself. It would effectively be a completely separate instance at that point though.
You also have to consider O365 apps which would then need to be logged in with their other UPN presumably so any SSO is no longer an option
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2022 02:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 16 2022 01:01 AM
Then you can join it partly like that to get what you want. But it would make no sense to do so, due to licencing and ongoing management costs.
You could enrol all the devices into their own tenant, then use Lighthouse and Rbac/ PIM to restrict each region to their devices based on tags / scopes for management. However, each user would end up using a guest account (b2b) when logging onto the device if you still want to get the best licensing from one main tenant for the users. This would mean you would not be using part of the entitlement for Intune in your main tenant but paying for extra licenced in the device management tenant
However, using the B2b access you lose all the benefit of using SSO and it create whole from the point of security so I would not recommend it. Unless you fully understand these risks
You could move to fully custom Rbac roles that way a user could have almost all of the GA roles but the Intune could be taken out.
The main part of the problem here is trust and training for the process that you are training to setup. If you do not feel the Global administrator can be trusted to understand the impact they may have. Then you have an internal process problem that needs to be addressed more than chaining the design of the management of the system.
If it is a case that the device will be managed by different third-party e.g different party in each region for the devices. Then that makes more sense to what you are trying to do. But if you give a user global admin you need to make sure they have adequate training and understanding of what they are doing if they are making changes. Otherwise you should be looking at what roles they need and limiting to just that
AAD is designed to be global and scale. so you really do need to try and remove the limiting legacy boundary's that where always in place with AD onprem and why you would end up with multiple logon accounts.
I would suggest getting a workshop with Microsoft to fully iron out key principles of your design around permission and requirements from the top of the organisation down for how to manage the permission and limit impact of Intune policy's, as licensing is best under one larger pool then individuals pools