- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Re: Difference between "Devices > Configuration Profiles" and "Endpoint Security &
Difference between "Devices > Configuration Profiles" and "Endpoint Security > Manage"
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 18 2022 03:09 AM
Our organization is digging deeper into Intune and one thing that confuses us are the multiple places where you can configure the same thing and how that leads to conflicts, e.g. Folder Protection.
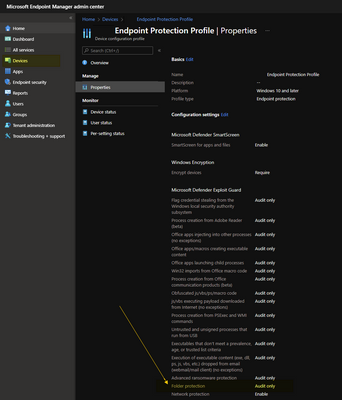
Folder Protection can be enabled through a configuration profile under Devices > Configuration profiles > Create profile > Endpoint Protection:
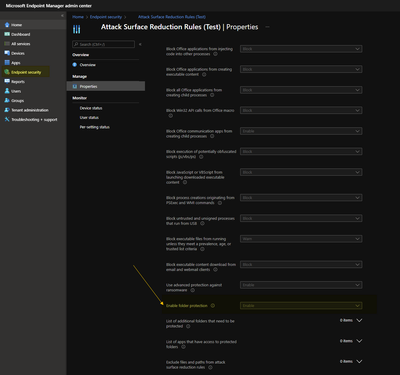
The same thing can be accomplished by using "Endpoint Security> Attack Surface Reduction":
Which of both approaches should be used? Why do conflicts appear when one option is set to Audit Only and Option is set to Enable - should the more the secure option be considered?
- Labels:
-
Intune
-
Mobile Device Management (MDM)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 18 2022 04:59 PM - edited Mar 21 2022 04:48 PM
A conflict arises when more than 1 policy is available and applicable of the same setting. Intune is just a delivery service. It doesn't decide which setting is best and enforce on its own. With that said, if your sole purpose is to target the security settings, then use endpoint security profiles as they are tailored specifically keeping device security in mind. For everything else, you can use device configuration profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 21 2022 07:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 21 2022 04:54 PM
Solution- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2022 08:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 25 2022 08:31 AM
@KirilThat's completely correct.
I'll make it even more precise for you... there's a specific order to this madness and it all comes down to Settings Catalogs. You see, almost everything under Endpoint Security (including baselines) boils down to a Settings Catalog template with a fancy GUI. It looks like this is where Intune is moving, as more and more stuff gets added in this form.
Microsoft actually has an order of preference for you configurations:
- Endpoint Security > Security baselines
- Endpoint Security > Other templates
- Devices > Configuration profiles > Settings Catalog
- Devices > Configuration profiles > Other templates
- Devices > Scripts
This opens up a whole new can of worms when it comes to conflict resolution. All these things can cause conflicts with each other and to make things worse Settings Catalogs (or derivatives) tend to use different names for settings than other configuration profiles.
Luckily though, MEM is getting better and better at telling you when and where a conflict arises.
For more information about Settings Catalogs and the options they give you:
Create a policy using settings catalog in Microsoft Intune | Microsoft Docs
Configuration service provider reference - Windows Client Management | Microsoft Docs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 25 2022 08:42 AM
I actually noticed another feature of the order of preference: I had a policy in Endpoint Security > Attack surface reduction about Attack surface reduction rules. I set them to block, but it was not working. There were no conflicts, but no rules were applied to any of the configured devices.
Then I noticed that I had another Endpoint protection profile in Devices > Configuration profiles, which set all ASR rules to "Audit mode". So this profile was preferred, which is fine, but I expected at least to get a conflict when I enabled the policy in Endpoint security. After setting the Device configuration profile to "Not configured", the Endpoint Security policy worked as expected.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 21 2022 04:54 PM
Solution