- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- App Protection Policy is not working when i have Company Portal app is installed and signed in.
App Protection Policy is not working when i have Company Portal app is installed and signed in.
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 12:52 AM
Hi Team,
In android, I am facing an issue where on my app, App Protection Policy is not working when i have Intune company portal app is installed and signed in. In the app i get the success callback as "ENROLLMENT_SUCCEEDED" but still it does apply the policy.
Where as if i have only installed Intune company portal app not signed in, policy gets applied.
Could please anyone helps me to understand this scenario, Any idea is appreciated.
Thanks,
Swati
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 02:01 AM
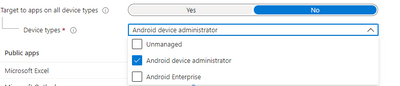
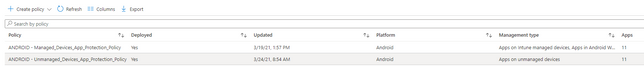
Hi, it looks like your app protection policy. How did you target the devices? All devices or did you specify specific types?
Because when you signing in in the company portal, you are enrolling your devices so its managed by intune.
If you don't sign in your device is unmanaged
I always create multiple app protection policy to make sure all devices types are protected
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 03:40 AM
@Rudy_Ooms_MVP So what is the right option i shall choose ? so that it applies on both (managed and unmanaged devices). I checked the policy it was "targeted the all devices" and now i tried to target only "Android device administrator" but still facing same issue.
Would appreciate you help here. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 04:51 AM
You could simple configure target to apps on all devices types to yes. If it's set to yes... it applies on all device types...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 05:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 05:28 AM
SolutionApp protection could really take some time to apply
https://docs.microsoft.com/en-us/mem/intune/apps/app-protection-policy-delivery#:~:text=Application%....
I did some deep dive into app protection policies some weeks ago...sometimes it really took some time before changes in an existing app protection policy applied.
You also could create a conditional access policy to require app protection
Here is the link:
https://call4cloud.nl/2021/03/app-protection-resurgence/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 05:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 05:35 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 05:35 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 05:38 AM - edited Apr 23 2021 05:45 AM
Hi,
I thought the same thing... But if you take a look at the blog I mentioned ... Requiring approved apps OR app protection is also working with Teams . So you can require approved apps and for the app that do support it... app protection(even when Microsoft docs tells us something else)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2021 01:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2021 05:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 29 2021 01:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 29 2021 05:02 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 30 2021 08:09 AM - edited Apr 30 2021 08:16 AM
It may be working, but it is not supported. There are 3 Apps that do not support the OR Grant:
Note
Microsoft Teams, Microsoft Kaizala, Microsoft Skype for Business and Microsoft Visio do not support the Require app protection policy grant. If you require these apps to work, please use the Require approved apps grant exclusively. The use of the or clause between the two grants will not work for these three applications.
This is a road block for us. I have the "OR" policy set up and ready to move users to it. It requires stacking policies. I have one that does MFA and TOU with the "AND" grant, and then a policy with the approved app and app protection grants appled with an OR grant. But until Teams offically supports this, I am stuck with my current policies. I do not care about Skype, Visio, or Kaizala. However Teams is a much used app for us. And until it is supported we will not go down that route. This is also great if you only need one or the other, But stacking on MFA and TOU adds complexity. It can be done, by stacking policies, however it is more complex.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 23 2021 05:28 AM
SolutionApp protection could really take some time to apply
https://docs.microsoft.com/en-us/mem/intune/apps/app-protection-policy-delivery#:~:text=Application%....
I did some deep dive into app protection policies some weeks ago...sometimes it really took some time before changes in an existing app protection policy applied.
You also could create a conditional access policy to require app protection
Here is the link:
https://call4cloud.nl/2021/03/app-protection-resurgence/