- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
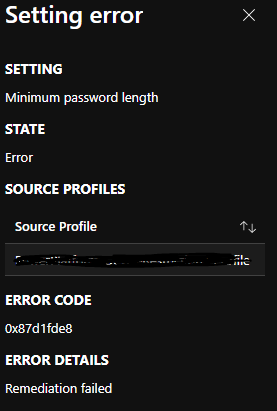
- Re: -2016281112 (Remediation failed) - Minimum Password Length
-2016281112 (Remediation failed) - Minimum Password Length
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2021 09:20 AM
Hi all,
I have been applied the Intune policy about minimum password length, to more than 100 clients but for 20 of them.
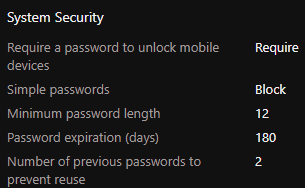
My password policy has a minimum of twelve characters, one Upper case, one Lower case, one number & one special character. The user password meets the policy but, I'm still getting the device as non-compliant.
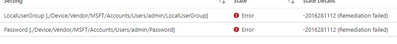
I'm getting the error message below :
Thanks in advance
- Labels:
-
Intune
-
Mobile Device Management (MDM)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2021 11:04 AM
COuld you disable the "special character" as test? to see what happens .
Take a look at this uservoice..
https://microsoftintune.uservoice.com/forums/291681-ideas/suggestions/38371480-intune-device-profile...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2021 12:15 PM - edited May 02 2021 12:16 PM
Hi,
Thank you for your response.
I tested it last week, but it didn't work for my case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 02 2021 10:38 PM - edited May 02 2021 10:46 PM
HI
I suspect it has to do with the set and get commands
The problem is that this CSP only supports Add Operation, which means the Get Operation will always fail because it has not been implemented.
We are getting the same error when we are pushing a device configuration policy to set the Password... Of course, this succeeds, but getting the result.... most of the times it fails
But you are mentioning non-compliant errors? Could you show your device securitycompliance requirements?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 03 2021 01:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 03 2021 01:07 AM - edited May 03 2021 02:01 AM
Hi,
Just wondering ( I am setting up a test vm right now) did the problem users also tried to change their password themself on the device itself and trying to check the compliance status in the company app?
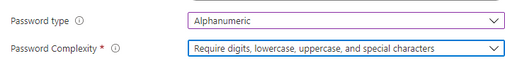
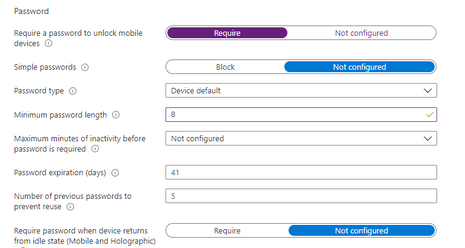
I am missing the password type and password complexity in your screenshot? Or did you leave it on default?
And are the devices:
azure ad joined or domain/hybrid joined
Did you also disabled Windows Hello?
And did you also read the docs from microsoft about this topic
Policy CSP - DeviceLock - Windows Client Management | Microsoft Docs
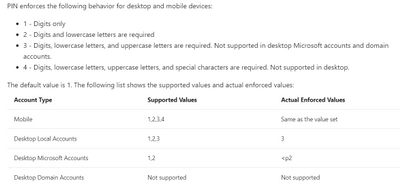
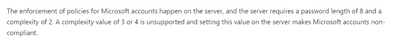
The enforcement of policies for Microsoft accounts happen on the server, and the server requires a password length of 8 and a complexity of 2. A complexity value of 3 or 4 is unsupported and setting this value on the server makes Microsoft accounts non-compliant.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 03 2021 04:30 AM
Hi,
One user changed his password but, he is having the same issue.
The Password type setting is the default one.
The devices are joined to an Azure AD.
The Windows Hello for some of the devices is enabled and for some others disabled.
The password has a minimum of twelve characters, x1 Upper case, x1 Lower case, x1 number & x1 special character.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 04 2021 07:42 AM - edited May 05 2021 05:42 AM
Hi. As you know I sent you a private message with some tips.
For anyone else reading this question:
Hi,
I guess when I need to troubleshoot this. I would change one setting at a time.
If you take a look at the Microsoft doc I linked to...
*
I guess you have got 2 options.
*Remove that part of the compliance policy as it is not working (uservoice says the same?)
*Change the password compliance policy to require only 8 characters and digits and lowercase
characters --> check if that works
if it works --> add uppercase
if that works --> change policy to 12
If that works --> add complexity requirement
Also beware Users with passwords that meet the requirement are still prompted to change their passwords.
I know it can take a lot of time... but troubleshooting always does :( ..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 05 2021 04:15 AM
I tried all the ways, but I'm still getting the device as non-compliant, and the error message is the same. I also test it with the assigned compliance policy without any result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 05 2021 04:40 AM - edited May 05 2021 04:46 AM
Solution
Hi
So even only specifying: Require
Password type --> Default
Minimum password --> 8
Is giving you non compliant errors in a new device compliance policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 15 2021 08:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 15 2021 11:56 PM
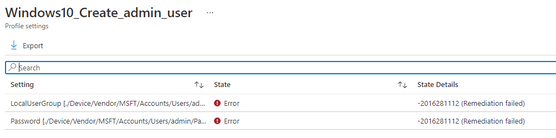
What I am trying to say. Is that when you create some device configuration policies like this example to create a local admin user and a corresponding password.
It will always fail... (the reporting) even when the user and the password were created.
To quote someone (have it in my internal docs... but.. not sure who said it )
The error here is due to the status check mechanism that is implemented within. In general, when Intune tries to determine if the policy takes effect on the target device, it calls Get Operation of the interested OMA-URI, which basically queries the registry key value from the client. And then compare the result with the policy value.
The problem is that this CSP only supports Add Operation, which means the Get Operation will always fail because it has not been implemented. That's why we get the error even if it successfully applied.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 30 2021 09:30 AM
Did you, by any chance, read or heard when they will implement the Get? It kind of makes Intune Password Compliance Policy useless as we do not know what is compliance or not?
Thank you.
Don
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 30 2021 11:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 12 2023 04:21 AM
@Rudy_Ooms_MVP Do you know if this has been remediated or when it will as I am having similar challenge (error message).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 12 2023 04:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 27 2023 05:50 AM
I bet it's caused by MSA passwordless sign-in and onboarding, meaning the personal profile effectively has a password length of "zero" - although the work profile's password / Hello PIN is fully compliant.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 05 2021 04:40 AM - edited May 05 2021 04:46 AM
Solution
Hi
So even only specifying: Require
Password type --> Default
Minimum password --> 8
Is giving you non compliant errors in a new device compliance policy