- Home
- Microsoft Search
- Microsoft Graph
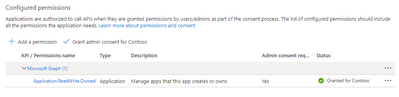
- Application.ReadWrite.OwnedBy: List all applications owned by the calling application
Application.ReadWrite.OwnedBy: List all applications owned by the calling application
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 29 2021 03:07 PM
Hi, I am trying to get only the applications that my app owns using Graph, and on the documentation it shows that I should be able to only list the applications where my app is owner. (This is to limit the content I have access to with my app)
Microsoft Graph permissions reference - Microsoft Graph | Microsoft Docs
Application
- Application.Read.All: List all applications (GET /beta/applications)
- Application.ReadWrite.All: Delete a service principal (DELETE /beta/servicePrincipals/{id})
- Application.ReadWrite.OwnedBy: Create an application (POST /beta/applications)
- Application.ReadWrite.OwnedBy: List all applications owned by the calling application (GET /beta/servicePrincipals/{id}/ownedObjects)
- Application.ReadWrite.OwnedBy: Add another owner to an owned application (POST /applications/{id}/owners/$ref).
NOTE: This may require additional permissions.
However, if I create an app that has owner permissions on another app and I query against the Graph API "Applications" I am still able to list all applications in the tenant.
I thought having me added as owner, on an application and having only that permission on my app, would limit my result ? Am I missing something here?
Adding the app as an owner in the following way:

When I query the Graph through PowerShell, I was hoping to get a 403 when querying all applications...
Anyone tried to limit the result you get back using this permission ? It is not a wanted solution to give permissions to read all applications for this app, therefor we need to limit the access...
- Labels:
-
API
-
App
-
Office 365
-
Office Graph
-
PowerShell
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 30 2021 10:37 AM
@Tore_Melberg Could you please ask this question on Microsoft Q&A as it is not to do with Search but broader Microsoft Graph? There are teams there that monitor those forums https://docs.microsoft.com/en-us/answers/topics/microsoft-graph-users.html