- Home
- Security, Compliance, and Identity
- Microsoft Entra
- Cross tenant SQL Server Authentication using B2B Collaboration
Cross tenant SQL Server Authentication using B2B Collaboration
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 21 2023 02:52 AM
Introduction
The purpose of this article is to detail the proof of concept developed to showcase that existing SQL resources hosted in various Azure service models and leveraging Azure AD authentication methods (users, service principals, certificates, etc…) at Company A can have authentication succeed if such authentication methods are initiated by identities (Users) in the new company B tenant.
Architecture Overview
Company B has Azure SQL instances and SQL Server VMs hosted on tenant A
Company B needs to carve out, for business reasons, and move into their own Azure Tenant.
Company B cannot move those servers immediately because of on-premises dependencies that will cause unacceptable downtime during a move.
Company B needs to validate that if they migrate their users to their own Azure tenant and, as such, identities reside in the new Tenant B Azure tenant, those users will be able to authenticate to the Azure SQL instances and Azure SQL servers located in the Tenant A
B2B Collaboration
Configuring cross-tenant access settings for B2B collaboration will allow the Company B identities to be invited as guest users to the Company A tenant.
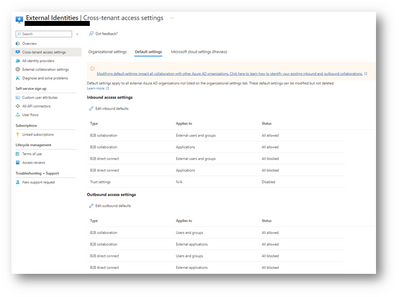
Using the external identities cross-tenant access settings to manage the collaboration between the two tenants.
These settings determine both the level of inbound access and the level of outbound access for invited users.
Default Settings
Default cross-tenant access settings apply to all external tenants for which you haven't created organization-specific customized settings.
Default settings for Company A
Default Settings for Company B
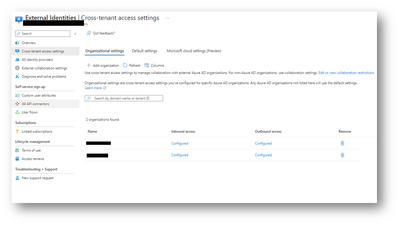
Organization Settings
Adding the organization will configure a specific Azure AD organization. Any Azure AD organizations not listed here will use the default settings.
Adding Company B as an organization to Company A will override the default settings and the defined settings for inbound and outbound settings will take precedence.
Adding Company A as an organization to Company B will override the default settings and the defined settings for inbound and outbound settings will take precedence.
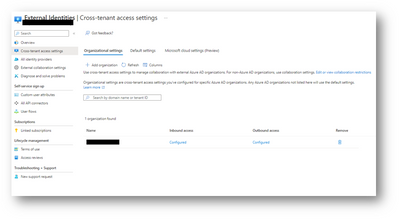
Organization settings for Company A
Organization settings for Company B
Inbound Access Settings
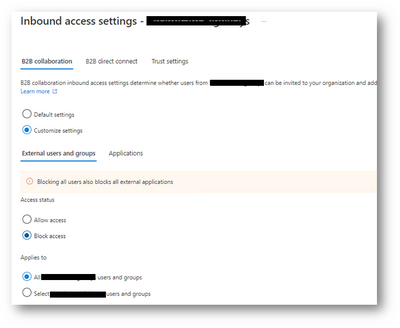
With inbound access settings, you select which external users and groups will be able to access the internal applications you choose.
Specify the users that will be allowed to be invited from the Company B tenant to be added as guests in the Company A tenant.
Define the users by adding the Object ID of each user.
Define a group by adding the Object ID of the group.
Any user not added in the inbound access settings cannot accept the invitation and will be blocked.
B2B Collaboration inbound settings for Company B organization on Company A tenant
As it’s a one-way trust from Company B to Company A. We will be blocking any inbound access coming from the Company A users.
Users from the Company A cannot be invited and added as guests in the Company B tenant.
B2B Collaboration inbound settings for Company A organization on Company B tenant
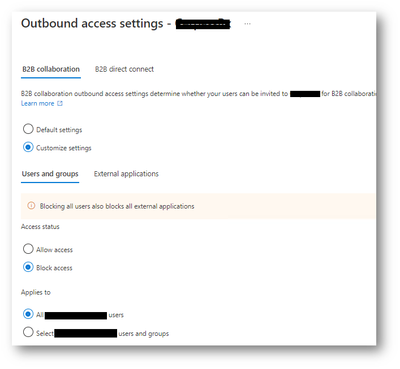
Outbound Access Settings
With outbound settings select which of your users and groups will be able to access the external applications you choose.
As it’s a one-way trust from Company B to Company A, outbound access will be blocked coming from the Company A users.
B2B Collaboration outbound settings for Company B organization on Company A tenant
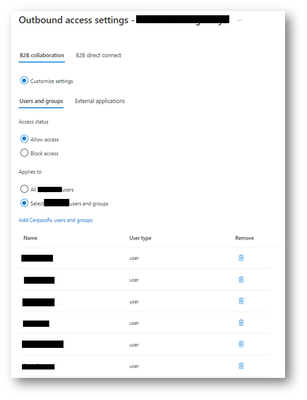
Specify the users that will be allowed to be invited from the Company B tenant to be added as guests in Company A tenant.
Any user not added in the inbound access settings cannot accept the invitation and will be blocked.
B2B Collaboration outbound settings for Company A organization on Company B tenant
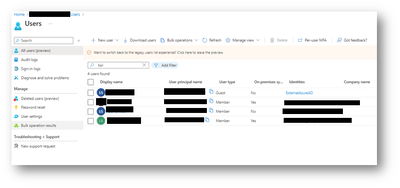
Guest Users
You can invite guest users (Company B Users) to the directory, to a group, or to an application. After you invite a user through any of these methods, the invited user's account is added to Azure Active Directory (Azure AD), with a user type of Guest. The guest user must then redeem their invitation to access resources using the invitation email they received.
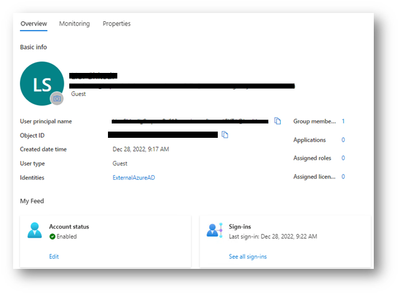
The guest user will appear on Azure AD with a UPN and an Identity as external Azure AD user.
SQL Cross-Tenant Permissions
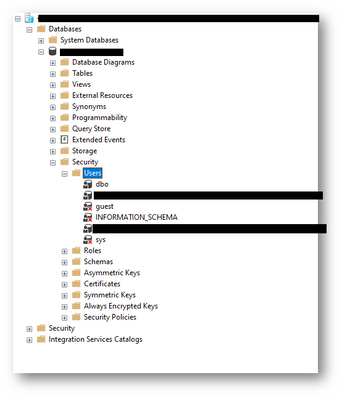
To grant your invited users’ permissions to access SQL databases, you can add them to a security group with access to the database(s).
Granting an individual invited user access to SQL databases can be done by connecting to the SQL database instance using SQL admin rights, selecting the database, and run the following query:
*Make sure to use the UPN of the invited user as it appears in Company A tenant.
The user is added to Company A directory with a user principal name (UPN) in the format emailaddress#EXT#@domain, for example,
user_CompanyB.onmicrosoft.com#EXT#@companyA.onmicrosoft.com, where:
- user_CompanyB.onmicrosoft.com is the email address invited from user_CompanyB directory
- #EXT# is the external identifier
- companyA.onmicrosoft.com is the organization from which you sent the invitations.
CREATE USER [user_CompanyB.onmicrosoft.com#EXT#@companyA.onmicrosoft.com] FROM EXTERNAL PROVIDER
And you user will appear in the Users security section of the database
Try to access the database using the invited user’s credentials, to verify a successful sign in
Summary
In summary, B2B collaboration access settings secured a trust relationship between the two tenants for successful cross-tenant SQL authentication.