- Home
- Security, Compliance, and Identity
- Microsoft Entra
- Conditional Access rule for Outlook Web exception
Conditional Access rule for Outlook Web exception
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Mar 30 2020
09:08 AM
- last edited on
Jan 14 2022
04:33 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 30 2020
09:08 AM
- last edited on
Jan 14 2022
04:33 PM
by
TechCommunityAP
Hi,
To access O365 apps like Outlook, Teams, OneDrive, SPO we require an enrolled and compliant Windows or iOS device. All external clients are Azure AD joined and Intune enrolled.
Now, we want to do an exception for Outlook web access. All computers (web browsers) should be able to access OWA from a non-enrolled computer with MFA. Restrictions for read-only according to the article Conditional Access in Outlook on the web for Exchange Online will be applied to prevent data leakage (but not yet configured)
It's not working as we want, we believe it used to work... If we except O365 Exchange Online App in our Desktop Conditional Forward, Web Access is indeed accessible as we want. But, then you can also use a mail client on a non-enrolled Windows 10 to access e-mail.- Only web access should be allowed unless you have an aad-joined and enrolled computer.
How do I fix this issue?
Thanks
/B
Conditional Access Rule
All users targeted (O365 emergency admin account excluded)
All Apps targeted (O365 Exchange Online excluded)
Client Apps
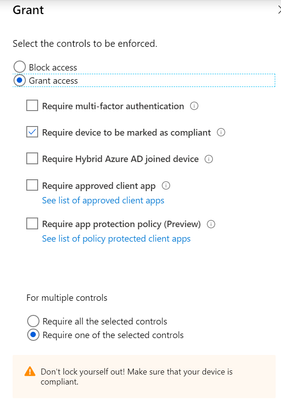
Grant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 16 2020 03:49 PM - edited May 16 2020 03:49 PM
Hi,
May you want to try to build 2 conditional access policies:
1. for OWA (Browser) and maybe you will also have to add mobile apps and desktop clients - grant access with MFA or compliant device (require one of the selected controls)
2. block access for everything else exept OWA (Browser) and desktop clients
Hope I could help you.