- Home
- Security, Compliance, and Identity
- Microsoft Entra
- Re: Conditional Access for Azure AD ONLY joined devices
Conditional Access for Azure AD ONLY joined devices
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 14 2022 01:48 AM
All my user mobile devices (Windows based) are Azure AD joined (no hybid)
The requirement is to allow access to online resources from these devices ONLY & if external to trusted location then do MFA)
Internally (trusted location) allow access without MFA
There is NO combination of CA conditions that I can get it working this way
There is no option to specify AAD ONLY joined devices
I can NOT just chose in Grant "Require device to be marked as compliant" because some devices will not be compliant (due to how odd Sophos works from time to time, and the compliance is simply not quick enough to report correctly)
In Conditions/Filter for device I can select isCompliant, device Ownership, trustType but the whole process gets thrown out of the window based to Grant
So no matter what I set users still can access services from personal PC, as long as MFA is executed (which is already configured in separate policy anyway)
- Labels:
-
MFA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 14 2022 02:27 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 01:02 AM
And what would that do to my Conditional Access in Azure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 01:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 01:43 AM
But as explained, I can NOT chose just the compliance condition (because that does not work 100% every time, for reasons mentioned).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 02:19 AM
I haven't heard of your third-party compliance issue before. Perhaps check with Sophos...
If filtering of any kind is not an option perhaps you need to look at Defender for Cloud Apps using an Access policy with a Block action.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 02:23 AM
I think you are replying whatever comes to mind, without actually reading the original post.
I do not trust the compliance being 100% always every time. So cannot use this as one & only defining condition.
All I need is CA where access from AAD joined machine or do NOT access at all
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 03:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 04:46 AM
Logically that does not convince me. And that is one place where there is no tester available
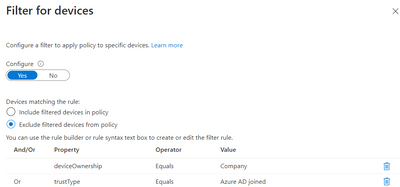
To me for Block in Grant, in Device filtering this would make more sense:
Include device that "deviceOwnership Not equals Company" & "trustType Not equals Azure AD joined"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 04:56 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2022 05:06 AM
I been through the report-only, but real life just works faster
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 04 2023 11:10 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 06 2023 05:14 PM
@Sebastian Cerazy Do you have any SSO enterprise applications? The CA you recommended works great but during the SSO there is NO device information so that login is blocked
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 07 2023 05:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 07 2023 09:34 AM
Office365 Shell WCSS-Client
Office 365 SharePoint Online
Are the stored windows creds getting passed through like the SSO app i added to the list. I dont want to exclude SPO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 08 2023 02:19 AM
Office365 Shell WCSS-Client
Office 365 SharePoint Online
Browser Edge 119.0.0
Operating System Windows10
Compliant Yes
Managed Yes
Join Type Azure AD joined
Maybe users are using Chrome without Microsoft 365 add-on?
Seb