- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Manage your authentication phone numbers and more in new Microsoft Graph beta APIs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks!
We’ve had a ton of requests for APIs to manage users’ authentication methods. That’s why it is so cool that today I get to announce that the first set of these APIs has reached beta in Microsoft Graph! Michael McLaughlin, one of our Identity team program managers, has written a guest blog post with information about the new APIs and how to get started.
As always, we’d love to hear any feedback or suggestions you may have. Please let us know what you think in the comments below or on the Azure Active Directory (Azure AD) feedback forum.
Best Regards,
Alex Simons
Corporate Vice President Program Management
Microsoft Identity Division
---------------------------------------
Hi everyone,
I’m thrilled to tell you about the new Azure AD authentication method APIs. These APIs are a key tool to manage your users’ authentication methods. Now you can programmatically pre-register and manage the authenticators used for MFA and self-service password reset (SSPR). This has been one of the most-requested features in the Azure MFA, SSPR, and Microsoft Graph spaces.
The new APIs we’ve released in this wave give you the ability to:
- Read, add, update, and remove a user’s authentication phones.
- Reset a user’s password.
- Turn on and off SMS sign-in.
We will be adding support for all authentication methods in the coming months.
These come at a crucial time. The shift to remote work driven by the COVID-19 pandemic has created unique complications for getting users registered for MFA and SSPR. Admins tell us that they don’t want users registering from potentially unsafe locations, but they do need to get users registered as soon as possible to get them protected. These APIs give you the ability to register your users and set them up to do MFA via SMS immediately without requiring them to register themselves from beyond your corporate network.
These APIs can be called by Global administrators, Privileged authentication administrators, Authentication administrators (recommended), and Global readers (can only use the read APIs). The ability to manage other users’ authentication methods is very powerful, so be sure to require MFA for these roles!
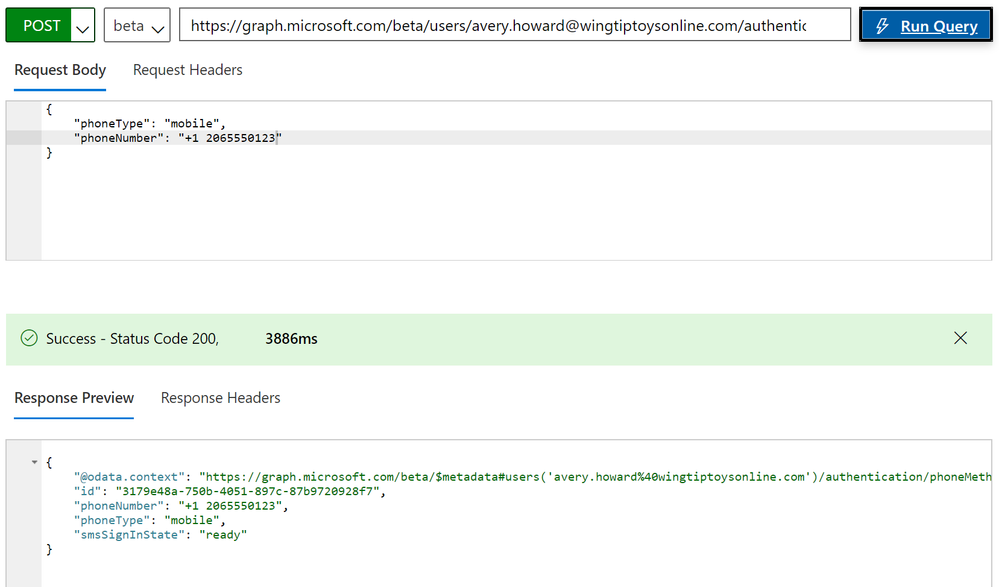
Here’s an example of adding a phone number for a user by posting to a user’s phone methods URL:
https://graph.microsoft.com/beta/users/<UPN>/authentication/phoneMethods
In the body, you pass in the type of phone (for example, “mobile”) and the number, and in the response you get back the full phone number entity:
Check out this tutorial to get you started, and to learn more, check out the Azure AD authentication methods API overview.
Thanks for reading. We hope these APIs help you in the work you’re doing today, and we’re hard at work expanding the range of authentication method APIs available to make them even more useful for you.
All the best,
Michael McLaughlin
Program Manager
Microsoft Identity Division
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.