- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune Blog
- Microsoft Endpoint Manager simplifies deployment of Microsoft Defender ATP for macOS
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Endpoint Manager is excited to announce support for simplified deployment and configuration of Microsoft Defender Advanced Threat Protection for macOS. Microsoft Defender ATP helps organizations prevent, detect, investigate, and respond to advanced threats using next-generation protection and endpoint detection and response across multiple platforms.
Expanding to remote worker scenarios introduces new challenges not only for the end users and the IT enablement teams, but also in terms of increased cyber security threats. Whether you are enabling BYOD, adjusting security policies to ensure productivity from home, supporting broader SaaS application usage, securing sensitive data, or bring additional devices onboard, Microsoft Endpoint Manager helps you deploy, manage, and secure work data on all your endpoints from a single platform.
Deploying Microsoft Defender ATP for macOS with Microsoft Endpoint Manager
With this release, Microsoft Defender ATP for macOS is available as a new app type in Microsoft Endpoint Manager. This eliminates the manual process required earlier and makes deploying Defender ATP for macOS as simple as a few clicks! Please use the new Endpoint Manager admin center at https://endpoint.microsoft.com to deploy this feature.
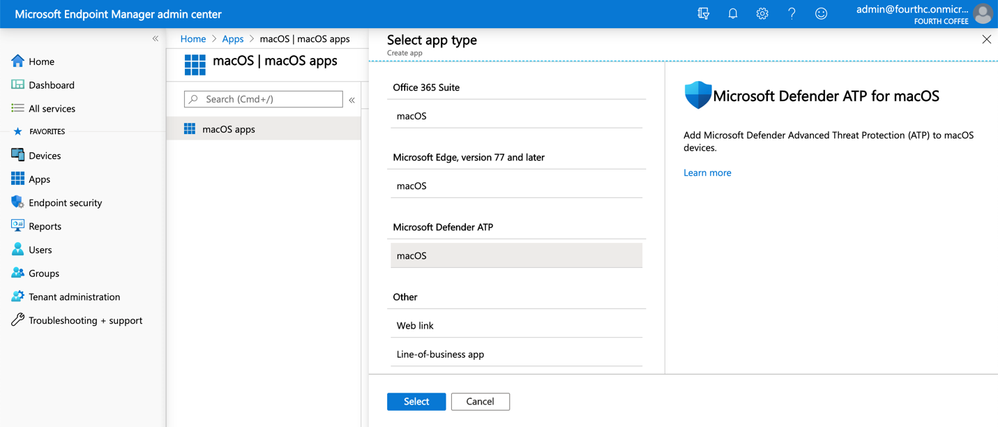
You can add Microsoft Defender ATP by signing in to the Microsoft Endpoint Manager admin center and selecting the App type as macOS under the Microsoft Defender ATP field.
Adding Microsoft Defender ATP in your tenant
To ensure automatic approval of the Microsoft Defender ATP kernel extension, deploy the Microsoft Defender ATP kernel extension profile to your users before the Microsoft Defender ATP app is assigned.
Expanded configuration for Microsoft Defender ATP
Microsoft Endpoint Manager is a unified platform that includes Microsoft Intune and Configuration Manager. Microsoft Endpoint Manager makes it easier to configure the most used settings within Microsoft Defender ATP. There are eight settings in total: four drop down controls and four tables where you can configure items to exclude from the Microsoft Defender ATP scan on the device as shown below. This article explains each setting when configuring the profile.
Configure Microsoft Defender ATP
IT admins can see these settings and configure them right from the Endpoint Manager console. They no longer need to manually set and upload key value pairs in a preference file or edit *.plist files, eliminating complexity and saving precious time.
To check out the new configuration settings, head over to the Endpoint Security portion of the Endpoint Manager admin console: Endpoint security > Antivirus (preview) > Create policy > macOS Antivirus > Create. Here, there are 8 settings that you can use to configure the Microsoft Defender ATP app on macOS 10.13 (High Sierra) or later.
Please visit the product documentation for updated information on pre-requisites. The three most recent major releases of macOS are supported. Currently, this supports:
- macOS 10.15 (Catalina)
- macOS 10.14 (Mojave)
- macOS 10.13 (High Sierra)
Recommendations for successful deployment and configuration
Here are some best practices for successful deployment. First, ensure the kernel extension profile and settings are sent down to the device before the ATP app is deployed. After you've enabled the service, you may need to configure your network or firewall to allow outbound connections between the cloud service and your endpoints. It is important to deploy the settings before the app, and not the other way around, because the app configuration takes effect immediately.
Here’s a troubleshooting tip: If, for some reason, the kernel extension is not present when the Microsoft Defender ATP app is installed, users will see “System extension blocked" message. In that case, users must approve the extension by going to Security Preferences or System Preferences > Security & Privacy on their macOS and select Allow.
Deployment scripts for Microsoft Defender ATP for macOS
In addition to deploying and configuring Microsoft Defender ATP using the Endpoint Manager admin center, the following PowerShell scripts are available in the Microsoft graph GitHub repository to help with the deployment:
|
Script Name |
Function |
|
MacOS_MDATP_Deployment_Add.ps1 |
Creates all profiles and applications for Microsoft Defender ATP for macOS in Endpoint Manager but does not assign them to any groups. |
|
MacOS_MDATP_Deployment_Add_Assign.ps1 |
Creates all profiles and applications for Microsoft Defender ATP for macOS in Endpoint Manager and assigns them to the group that is specified. |
Each script deploys the same four profiles:
|
Profile |
Type |
Purpose |
|
macOS MDATP Kernel Extension |
Custom |
This is a custom macOS | Configuration profile that configures macOS to trust kernel extensions signed by Microsoft’s developer certificate. |
|
macOS MDATP Notifications |
Custom |
This is a custom macOS | Configuration profile that configures macOS to allow Microsoft Defender ATP to show the end user critical notifications when necessary. |
|
macOS MDATP Full Disk Access |
Custom |
This is a custom macOS | Configuration profile that configures macOS to allow Microsoft Defender ATP full access to the disk. |
|
macOS MDATP Onboarding |
Custom |
This is a custom property list macOS | Configuration profile which tells the Microsoft Defender ATP application which tenant to connect to. |
|
macOS Microsoft Defender ATP |
Application |
This is a macOS | app profile that configures the client to download and install the Microsoft Defender ATP binaries. |
The scripts take the following command line parameters
- OnboardingXMLFilePath < file path>
- This is the path to your Microsoft Defender ATP WindowsDefenderATPOnboarding.xml file. To obtain this file, perform the following steps.
- From a browser, go to https://securitycenter.windows.com/dashboard
- Sign in with an administrator account
- Click Settings > Onboarding
- Select macOS from the dropdown for onboarding process
- Select Mobile Device Management / Microsoft Intune from the deployment dropdown
- Click Download onboarding package
- Inside the WindowsDefenderATPOnboardingPackage.zip make a copy of the WindowsDefenderATPOnboarding.xml file within the Intune folder.
- This is the path to your Microsoft Defender ATP WindowsDefenderATPOnboarding.xml file. To obtain this file, perform the following steps.
- AADGroup <AzureAD Group Name>
- This is the name of the Azure Active Directory Group Name. This value is case sensitive.
- Example: Create and Assign profiles for Microsoft Defender ATP for macOS in Endpoint Manager
- This is the name of the Azure Active Directory Group Name. This value is case sensitive.
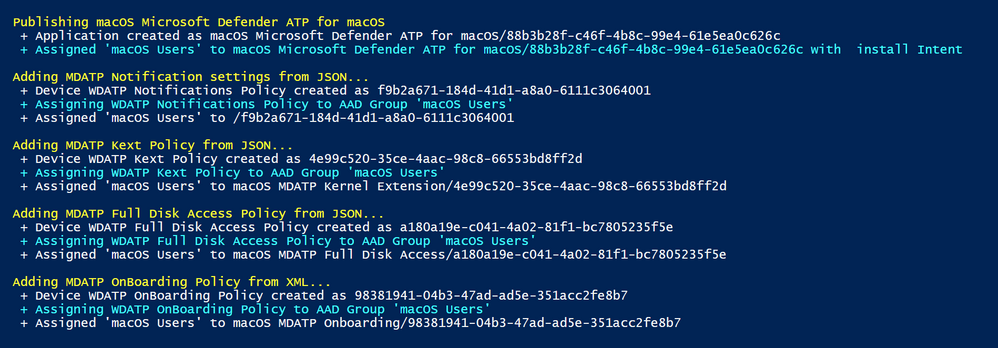
In this example I have saved my WindowsDefenderATPOnboarding.xml file in the same directory as the MacOS_MDATP_Deployment_Add_Assign.ps1 script. Once the script is run it will create all five policies and assign them to the group provided.
Important: If any users or devices are in the Azure AD Group they will begin receiving policies at their next check-in.
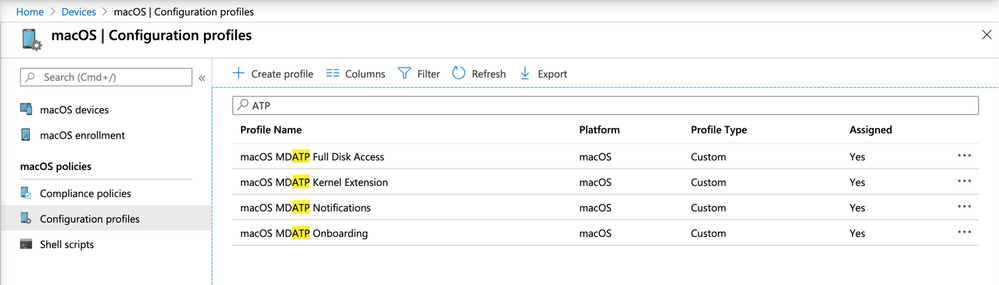
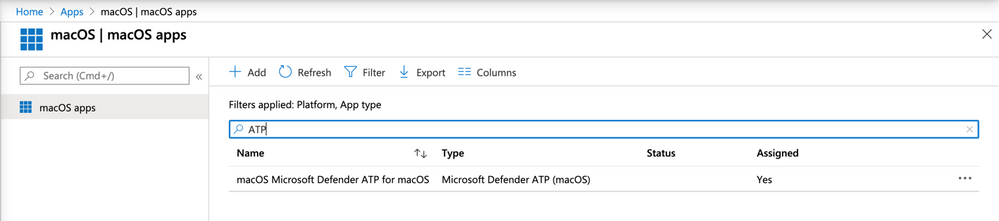
Once done, the following policies will appear in your Endpoint Manager console:
Configuration profiles
macOS Apps
Next steps:
We are very excited about empowering Microsoft 365 administrators to deliver the reliable next-generation protection and endpoint detection and response to all their users, whether on Windows or macOS devices. Unified endpoint security management in Microsoft Endpoint Manager provides a single pane of glass to save time and energy for the busy IT admin. We hope you will find value in the automation and scripting described in this article, compared to the manual deployment method used previously which continues to remain supported.
Learn more:
Microsoft Endpoint Manager continues to build first-class support for macOS management, including recently added support for Apple Mac scripting and expanded app management support on macOS. Bookmark the product documentation to stay up-to-date on What’s New and What’s Coming in Microsoft Intune.
Follow @MSIntune on Twitter
(This blog post is authored in collaboration with Neil Johnson, Anya Novicheva and Arnab Biswas from the Microsoft Endpoint Manager engineering team)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.