- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune Blog
- Announcing Tamper Protection for Configuration Manager Tenant Attach clients
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Matt Shadbolt (@ConfigMgrDogs) - Principal Program Manager | Microsoft Endpoint Manager
Last year, the Defender for Endpoint team and Microsoft Endpoint Manager team collaborated on a new feature called Tamper Protection.
Tamper Protection protects against malicious actors modifying the configuration of Microsoft Defender on Windows 10 clients to disable AV protection, real-time protection, behavior monitoring, cloud-delivered protection, or to remove security intelligence updates. Endpoint Manager and Defender for Endpoint uniquely enable Enterprise administrators to enable and disable Tamper Protection in a secure manner.
Before today, Tamper Protection controls were only available for Windows 10 clients being managed via Intune cloud management or ConfigMgr co-management.
Today we’re excited to announce Tamper Protection has been extended to ConfigMgr 2006-only clients on both Windows 10 and Windows Server 2019, delivered via Tenant Attach. (Windows Server 2016 coming soon!)
Tenant Attach allows you to sync your on-prem only ConfigMgr clients into the Microsoft Endpoint Manager admin center, and deliver Endpoint security configuration policies to your on-prem collections/clients.
You can easily enable Tenant Attach by following these instructions.
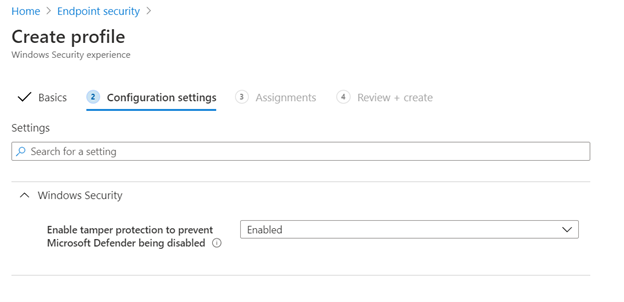
Once enabled, browse Endpoint security > Antivirus in the Microsoft Endpoint Manager admin center to create and deploy the Tamper Protection setting.
Next, configure the Tamper Protection setting and deploy it to a Configuration Manager collection of devices.
The policy syncs down to the ConfigMgr site, and applies to all devices in the target collection. You can view the policy status in the Monitoring > Deployments section in ConfigMgr, and can also be found in the policy status in the Endpoint Manager Admin center

Clients now have the Tamper Protection feature On, and you can validate in on the client by viewing the Windows Security app > Virus & threat protection > Virus & threat protection settings

Tamper Protection is a unique Microsoft 365 feature, utilizing the deep integration we deliver to enable both Security and IT management teams to keep their organization secure.
To learn more, please visit our Endpoint security docs.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.