- Home
- Security, Compliance, and Identity
- Microsoft Defender Threat Intelligence Blog
- What's New: MDTI Intel Reporting Dashboard and Workbook
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Strategic threat intelligence involves gathering and analyzing information to identify potential threats to an organization's security. This proactive approach helps companies anticipate and mitigate potential security risks. Reporting plays a crucial role in strategic threat intelligence by providing insights and data-driven recommendations to decision-makers. Threat intelligence reports are designed to deliver accurate and actionable information, enabling organizations to take appropriate measures to protect against potential threats.
In this blog post, we are excited to announce the launch of a new dashboard that enhances Microsoft's threat intelligence reporting capabilities. This dashboard provides a user-friendly interface that enables organizations to easily access and analyze threat intelligence data. With this new tool, decision-makers can make informed decisions to strengthen their security posture and protect against potential threats. In this post, we'll delve into the features of this dashboard and explore the benefits that each of the intelligence reporting it enables.
Deploying the Solution
Before beginning the installation process, it's crucial to confirm that you have met the following prerequisites:
- Read the APIs in the Microsoft Graph Blog.
- You have enabled the MDTI API license on your tenant.
- You have created an application with a corresponding APP ID and Secret.
- You possess the necessary permissions to deploy resources in the designated resource group.
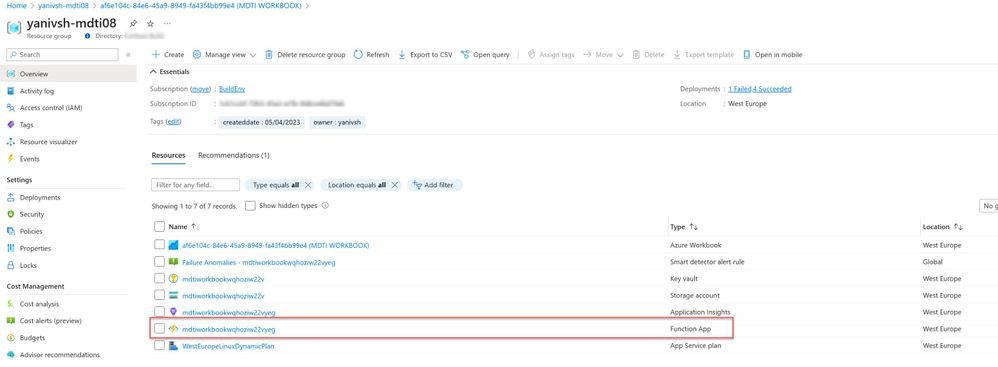
The above solution will deploy these resources into the target resource group:
- Azure function –This will act as a middle layer between the workbook and the API.
- Key vault – This will store the API key and Secret.
- Workbook – This serves as the presentation layer.
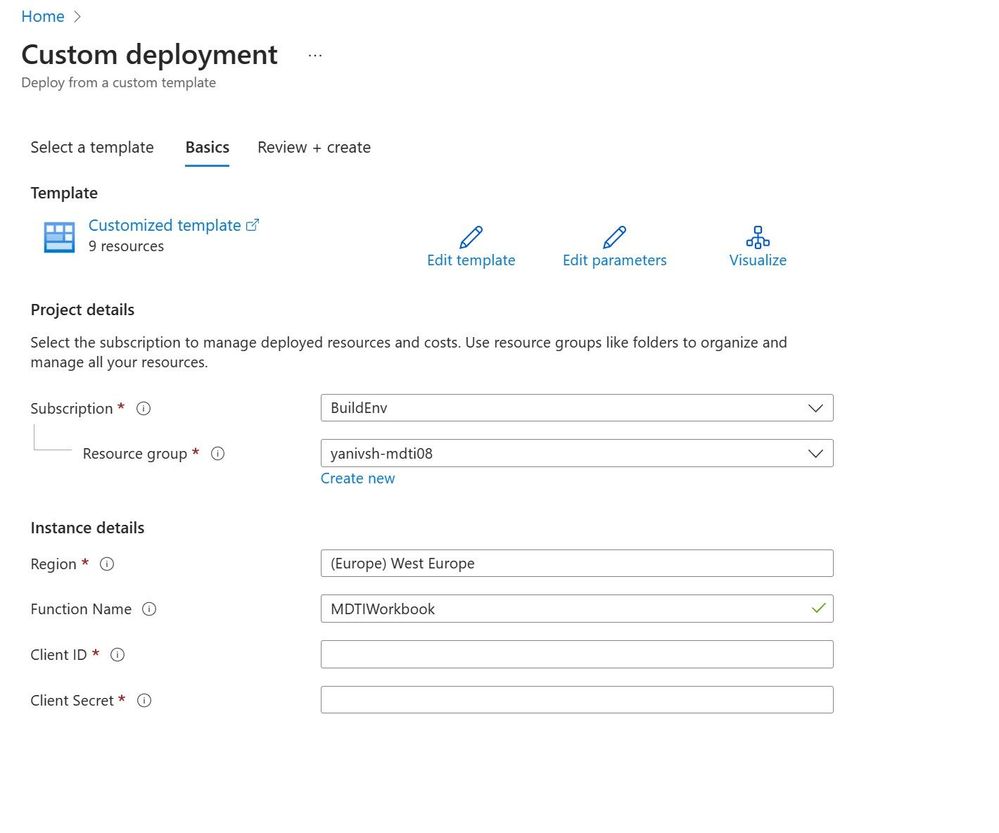
To install the solution, navigate to this GitHub repository and press Deploy to Azure. Be sure to add the client ID and app secret you created in the custom deployment screen. This information will be saved in an Azure key vault.
Workbook Configuration
Post installation, navigate to the target Resource Group you deploy the solution and copy the Azure function name.
Open the workbook and in the “Deployed-AzureFunction.” Select the name you copied in Step one.
To set up the MDTI Sentinel Incident View tab, choose the subscription and workspace for the Sentinel instance. Remember that although the remaining sections of this workbook do not depend on Sentinel data, you must still select a workspace in this tab.
How to use the Workbook
The workbook enables SOC analysts, threat hunters, and SOC operators to easily have a 360-degree view of adversaries and helps them identify the underlying infrastructure.
The solutions provided in the workbook:
Sentinel Incident View
This solution combines the indicators of compromise (IOCs) obtained from various MDTI feeds, curates information on alerting and incidents for the MDTI analytics engine, and presents a geographical visualization of some of these IOCs. This approach streamlines the data consolidation and enhances the MDTI analytics engine's threat detection capabilities by providing a comprehensive overview of IOCs' spatial distribution on Microsoft Sentinel.
Actions:
- Prereq: Ensure the MDTI Sentinel Data connector and MDTI analytics engine are set up to bring IOC feed, alerts, and incidents into Sentinel.
- Select the subscription, workspace, and duration for your sentinel workspace with MDTI feeds on the workbook page.
- Leverage the information to pivot to incidents from MDTI and geographically identify potential IOCs that may impact your organization.
Figure Sentinel Incident View on MDTI Workbook
Hostname Information
The Hostname information tab in the MDTI workbook facilitates the following functions:
- It allows the user to ascertain the threat intelligence details, location, and reputation of a Hostname in relation to Intel Profiles and underlying information (Part of a blocklist, infrastructure exhibiting suspicious behavior).
- It displays tracker information.
- It displays cookie information.
- It displays component information.
Actions:
- Search for the hostname on the workbook.
- It should proceed to display content about Threat intelligence.
Figure MDTI workbook ~Hostname Information Tab
IP Information
The IP address information tab in the MDTI workbook facilitates the following functions:
- It allows the user to ascertain the threat intelligence details, location, and reputation of an IP address in relation to intelligence profiles and underlying information (Part of a blocklist, infrastructure exhibiting suspicious behavior).
- It displays tracker information. Trackers can correlate a disparate group of websites to a central entity. Often, actors copy the source code of a victim’s website they are looking to impersonate for a phishing campaign. Seldom will actors take the time to remove these IDs that allow users to identify these fraudulent sites using Microsoft’s Trackers data set.
- It displays cookie information. MDTI highlights and indexes cookie names observed when crawling a website and allow users to dig into everywhere we have observed specific cookie names across its crawling and data collection. Malicious actors also use cookies to keep track of infected victims or store data to be utilized later.
- It displays Web component information. Web components are details describing a web page or a server infrastructure. This data is generated by performing web crawling and port scanning. These components allow a user to understand the makeup of a webpage or the technology and services driving a specific piece of infrastructure.
Actions:
- Search for the IP address on the workbook.
- It should proceed to display content about Threat intelligence.
Figure: IP information on MDTI workbook
MDTI Articles
MDTI articles are designed to help security professionals understand the latest cyber threats and take proactive measures to protect their systems. Within the workbook, MDTI articles aim to assist security experts in comprehending current cyber hazards and implementing proactive strategies to safeguard their systems. The article view offers a comprehensive view of MDTI articles, enabling one to obtain insight into each Article's indicators and information. Using the search article ID method, users can also explore articles in detail and pivot through them by searching for specific case scenarios, industries, countries, and more.
Actions:
- Get visibility of the articles published in the last 60 days.
- Using the Search Bar, type any Keyword about your need, and it should display available articles; alternatively, select any article. Once you do this, it shall display.
- Single article details (You can pivot to the URL for the Article)
- IOCs within the Article
Figure MDTI Articles view within MDTI Workbook.
Vulnerabilities Information
By utilizing CVEs (Common Vulnerabilities and Exposures), it is possible to conduct threat hunting by detecting system or network vulnerabilities, assessing their severity using the CVSS framework, ranking them according to risk level, and taking measures to mitigate them to minimize the likelihood of exploitation. Moreover, it is also possible to identify infrastructure components that are associated with the searched CVE.
Action:
- Search for Vulnerability via CVE ID.
- It will display the Vulnerability detail to entail information on CVE, Components affected by the vulnerability, MDTI Articles in relation to the vulnerability, and Tags.

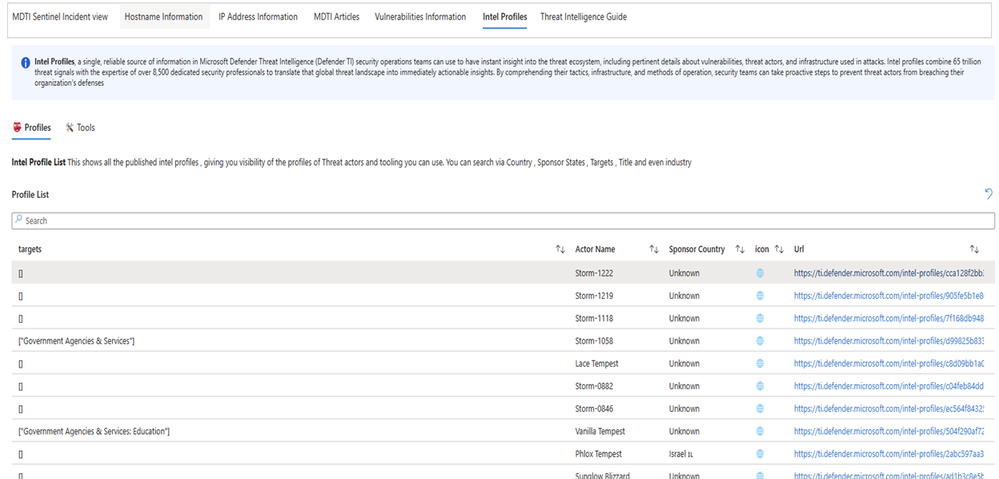
Intel Profiles
Intel Profiles, a single, reliable source of information in MDTI security operations teams, can use to have instant insight into the threat ecosystem, including pertinent details about vulnerabilities, threat actors, and infrastructure used in attacks.
Action:
- Select a threat actor through a list of Threat actors and tools; it should proceed to detail the intel profile information (Targets, sponsor states, etc.) and the intel profile indicators.
Figure Intel Profiles on MDTI Workbook
Sign Up for a Trial
- Please reference our “Getting Started with MDTI” blog for details regarding setting up your MDTI Premium trial.
MDTI Support
For any support-related issues regarding Microsoft Defender for Intelligence, please access this portal https://support.serviceshub.microsoft.com/supportforbusiness/create and select Security -> Microsoft Defender for Intelligence.
We Want to Hear from You!
Be sure to join our fast-growing community of security pros and experts to provide product feedback and suggestions and start conversations about how MDTI is helping your team stay on top of threats. With an open dialogue, we can create a safer internet together. Learn more about MDTI.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.