- Home
- Security, Compliance, and Identity
- Microsoft Defender for Office 365
- Re: Advanced Delivery for third party phishing attack scenario
Advanced Delivery for third party phishing attack scenario
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 24 2021 12:35 AM
Hello MSFT Team,
Normally every quarterly we perform the third party phishing attack simulator in the Organization to educate the end user's but this time all the phishing testing emails are getting quarantined by marking as high phishing.
After searching on the google found below link to use O365 advanced delivery policy for third party phishing. In the advanced delivery policy we have added:
Domain : added sending domain
Sending IP : added sending IP
Simulation URLs to allow : added simulation URLs as well
Followed the above msft blog and added the rule successfully but still the testing phishing emails are getting quarantined and marked as high phish.
But one thing has been observed that third party phishing simulator is hosted on amazonses.com and sending domain is different but we have added only the sending domain.
Do I need to add the amazonses.com domain as well in advanced delivery policy.
Please can someone shed some light on it as I searching lot of blogs on advanced delivery policy but found nothing.
Any help really appreciated.
Regards
Anand Sunka
- Labels:
-
Phishing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 26 2021 08:39 AM
Hi @ANAND_SUNKA, please open a support case so that our engineering team can investigate further, look at the configuation of your tenant and provide our recommendation here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 28 2021 08:26 AM
Thanks for the reply.
I have resolved the issue by looking at 5321.fromadress and whitelisted that address and issue got resolved.
But now we are facing different issue with url's getting blocked by using ATP policies.
I have whitelisted the urls in Advanced delivery as well as in ATP safe links policy.
But still no luck.
Why does the adavanced delivery urls whitelisted is not working.
Any help really appreciated.
Regards
Anand Sunka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 08 2021 08:09 AM
You can't bypass malware filtering or ZAP for malware
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/configure-advanced-deliv...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 10 2021 12:07 AM
Thanks for the update in my scenario I was using third party phishing simulation hosted at amazonses.com and it got 2 From addresses where I was blocking only the single from address.
That's why the issue was happened.
But after whitelisting the second from address my issue was resolved.
Yes as you said we can't bypass malware filtering or ZAP as they implemented secure by default.
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/secure-by-default?view=o...
Anyways thank you.
Regards
Anand Sunka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 10 2021 10:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 22 2022 02:58 PM
The Microsoft Defender for Office (MDO) Advanced Deployment Guide in the M365 Admin Center has configuration steps that cover this Attack Simulator topic area.
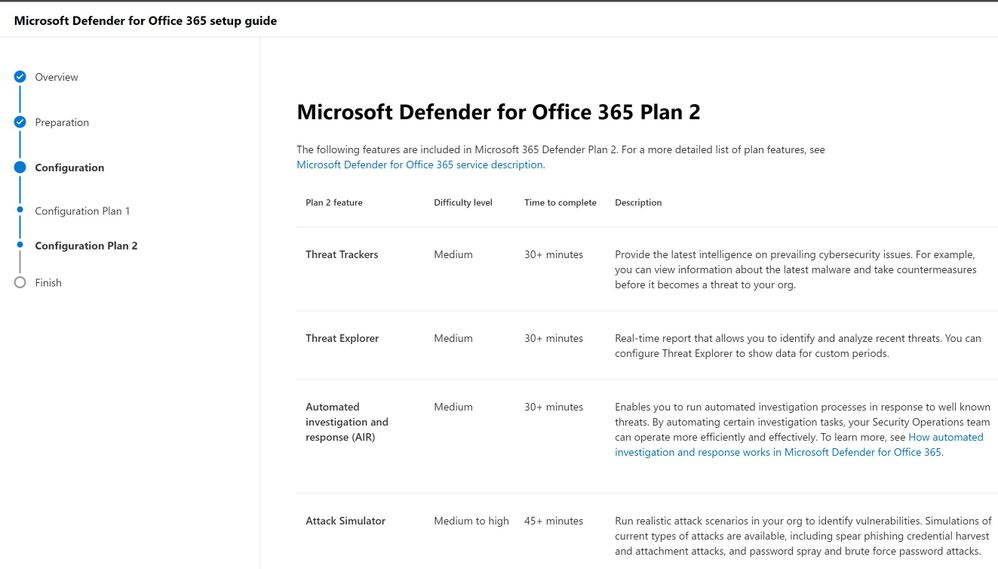
Please note that you will need to have Tenant Admin login permissions to the M365 Admin Center to view the MDO Advanced Deployment Guide.