- Home
- Security, Compliance, and Identity
- Microsoft Defender for Identity
- New! Extending user based exclusions for alerts
New! Extending user based exclusions for alerts
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 25 2019 08:19 AM
You asked, we listened!
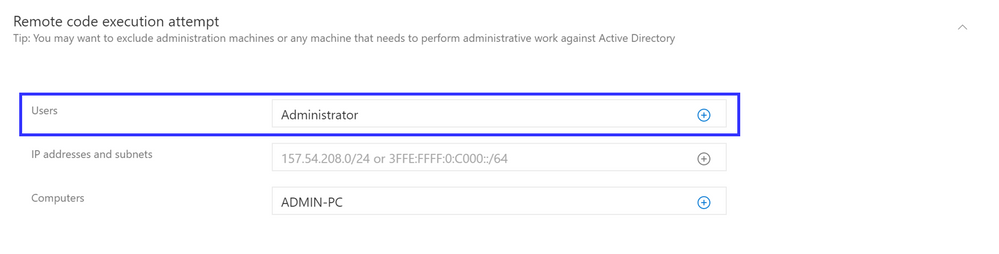
In an effort to improve and enhance your experience using Azure ATP, you can now set alert exclusions that include users, along with other entities such as IP addresses, subnets and computers.
For example, for the “Remote code execution attempt” detection, you can set an exclusion that is based on either a list of machines or an administrative account that is privileged to perform such activities.
User based exclusions were added to the following alerts:
- Suspected DCSync attack (replication of directory services)
- User and Group membership reconnaissance (SAMR)
- Suspicious service creation
- User and IP Address Reconnaissance (SMB)
- Remote code execution attempt
Stay tuned for additional alerts and updates. As always, your feedback is welcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 19 2021 05:42 PM
Hi @Tali Ash
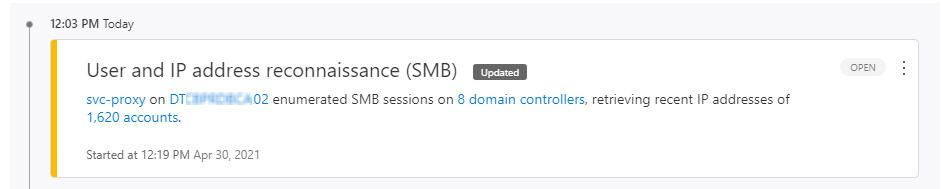
We have a proxy service running, with service account svc-proxy, on server DTxxxxxxxx02
These activities generates “User and IP address reconnaissance (SMB)” alerts.
We do not want future alerts.
We added the svc-proxy to user exclusion “User and IP address reconnaissance (SMB)”
After we closed the alert, we still get alerts "An actor on DTxxxxxxxx02 enumerated SMB sessions on..."
In the evidence details it shows An actor = svc-proxy
Why do we still get these alerts after we excluded the user?
It seems the user only based exclusion for alerts is not working...
Remark: if we exclude both the user "svc-proxy" and computer "DTxxxxxxxx02" it works fine, no more alerts. But we don't want to exclude the computer too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 26 2021 12:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2021 06:03 AM
Yes, they happen after I excluded the user and closed the previous alert.
The content of the new alert changed from "svc-proxy on" to "An actor on".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 30 2021 12:11 AM
@DanPan Please open a support case, export the alert data to excel and share with support.
Generally, if you excluded the user account and indeed it was the same user that did this, we should not have reopened this alert.
Note that in some cases we cannot tell who the user is, depending on exact traffic type, so in this case if the machine was not excluded, we will still fire the alert based on the machine.