- Home
- Security, Compliance, and Identity
- Microsoft Defender for Identity
- Re: Microsoft ATA - Detecting ''Passwordless'' attacks
Microsoft ATA - Detecting ''Passwordless'' attacks
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Jul 22 2019 11:37 AM - edited Jul 22 2019 01:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 11:37 AM - edited Jul 22 2019 01:18 PM
Howdy,
After taking a look at the Microsoft ATA suspicious activity guide. I had some questions about some malicious use-cases and I was mainly curious if you guys do detect these kind of activities.
https://docs.microsoft.com/en-us/advanced-threat-analytics/suspicious-activity-guide
If the answer is ''no'', which is fine. It means that we can work together on improving it.
- Password Downgrading
Microsoft ATA has a section called ''Encryption Downgrade''
Do you guys also detect when someone is downgrading the password length by modifying the minpwdLength attribute at the AD Root?
In this case everyone could create an AD account without a password or reset their password to <blank>
- (Service) Account with no password required
Well, service account is just an example. This can also be a normal user account, but back to the case study.
Service accounts barely get a password reset, but do (often) contain high-privileges in the domain.
Account Operators is a group that is used a lot and has wide permissions in the domain.
What if we DENY Read userAccountControl for Everyone in the domain and then just decide to modify the userAccountControl value to 544, which is equal to PASSWD_NOTREQD.
Now when looking in ADUC or through PowerShell, we won't find the output of the user XYZ has a PASSWD_NOTREQD value. So now someone can reset the password to <blank> and authenticate without password.
Even from a Domain Admins perspective, we don't see any value on the userAccountControl attribute, which can make it incredible difficult to find users without password, if ATA can't detect this of course. But it actually has the 544 value. Password not required!
Would you guys detect users logging in without any password? - You can detect this in the Windows Event Logs, but it is pretty difficult to monitor on it, if you don't really have the resources for it.
And what about hiding the userAccountControl value for everyone. How would you detect this kind of stuff?
- Granting user permissions to modify password policy
Granting an unauthorized user on the AD Root and give him the following permissions.
Allows the user to change his password to <blank> or modify the password policy, so it can downgrade the password length for example or disable the lockout policy. Would Microsoft ATA flag this as well?
These were my questions about the ''passwordless'' attacks ;)
Hope to hear back from you guys,
Regards,
H
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 23 2019 02:09 AM
Hi @Deleted,
I am suggesting you to look at Azure ATP, as it is the new updated service for ATA.
And most of our new detections and capabilities are inserted into Azure ATP.
Thank you very much for the interesting ideas, I think most of it is related to security admins and can be monitored as part of our identity security posture reports - @Or Tsemah
Will check about identifying a user logon without a password, if it will be relevant and possible to detect will add it to the backlog.
Thanks,
Tali
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 23 2019 02:14 AM
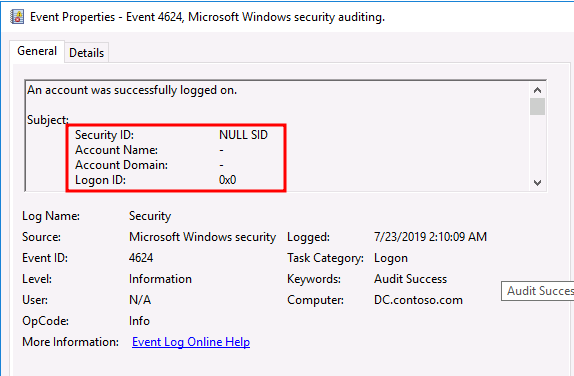
This is the closet event that will be generated when users authenticate without password.
I think you definitely should take a look at!