- Home
- Security, Compliance, and Identity
- Microsoft Defender for Identity
- Re: Enable Unconstrained Kerberos Delegation
Enable Unconstrained Kerberos Delegation
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Jul 22 2019 10:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 10:28 PM
Hi there,
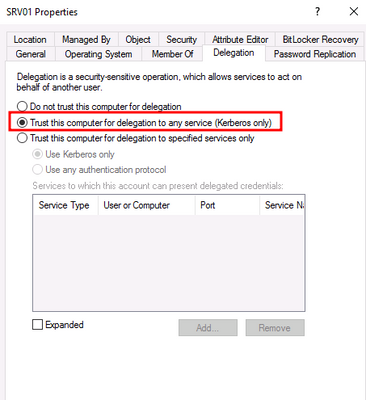
By default the group ''Account Operators'' is often used, despite that Microsoft recommend it to keep it empty, but this group has wide permissions in the domain. All the users in Account Operators could enable the Unconstrained Kerberos Delegation on servers, because they are granted the GenericAll permission on these computer objects.
I tried to find some additional information about it to see if ATA picks this up. I couldn't find it, but there could be a chance that I just overlooked it. So I was wondering if you guys would detect, when someone decided to turn this setting on?
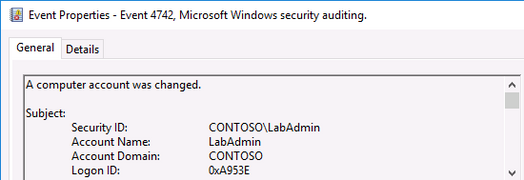
Here is the event log that will be generated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 11:47 PM
@Deleted , as far as I know there is no such detection.
@Tali Ash , Can you confirm?
you can find a list of alert types in this link:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/suspicious-activity-guide
This is updated from time to time when we add more detections.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 11:48 PM
@Eli OfekDo you consider to add this detection rule to it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 11:52 PM
I will let @Tali Ash comment on that as this is a product decision, and she might know if this is somewhere in the roadmap.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 11:55 PM
@Or Tsemah Can you please share with @Deleted the relevant identity security posture reports?
Huy, what you are suggesting is covered by reports and not alerts, as it is more relevant for dangerous configurations in the environment,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 23 2019 12:14 AM
@Deleted I can confirm that this feature (Exposing which entity has an unsecure kerberos delegation such as Unconstrained or some variations of constrained\resource based delegations) is in private preview and i hope to share some information about its release soon.
If you would like to know more, you can contact me directly.