- Home
- Security, Compliance, and Identity
- Microsoft Defender for Identity
- Clearing audit logs from Domain Controller
Clearing audit logs from Domain Controller
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Jul 22 2019 02:01 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 02:01 PM
Hi there,
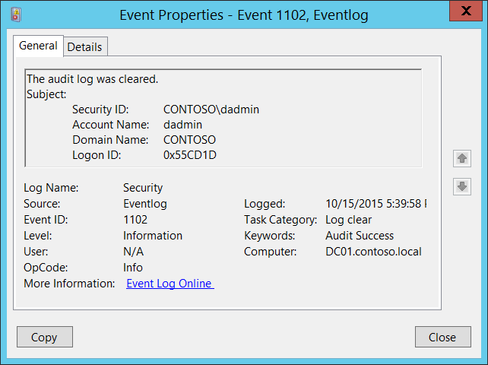
Clearing the event logs from the Domain Controller or workstation could be a sign of malicious behavior.
Does Microsoft ATA currently alert on this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 02:05 PM
@Deleted , No, there is no detection for this.
@Tali Ash , did we ever consider this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 09:01 PM
If you consider adding it to ATA. You might add Event 1100 to it as well.
This event shows up when someone shuts down the event logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 23 2019 12:24 AM
Thanks @Deleted , we will look into it, currently are not planning at add such detection.
Thanks,
Tali
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 24 2019 05:04 AM - edited Jul 24 2019 05:04 AM
I think this should be triggered from the SIEM. Especially if you're collecting logs from all servers in to the one source. AATP/ATP would only trigger this from a DC, but your SIEM would trigger it from anywhere that is sending the logs.