Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Microsoft Defender for Identity
- Azure ATP brings you 2 new preview detections on DcShadow attack
Azure ATP brings you 2 new preview detections on DcShadow attack
Discussion Options
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 24 2018 11:26 AM
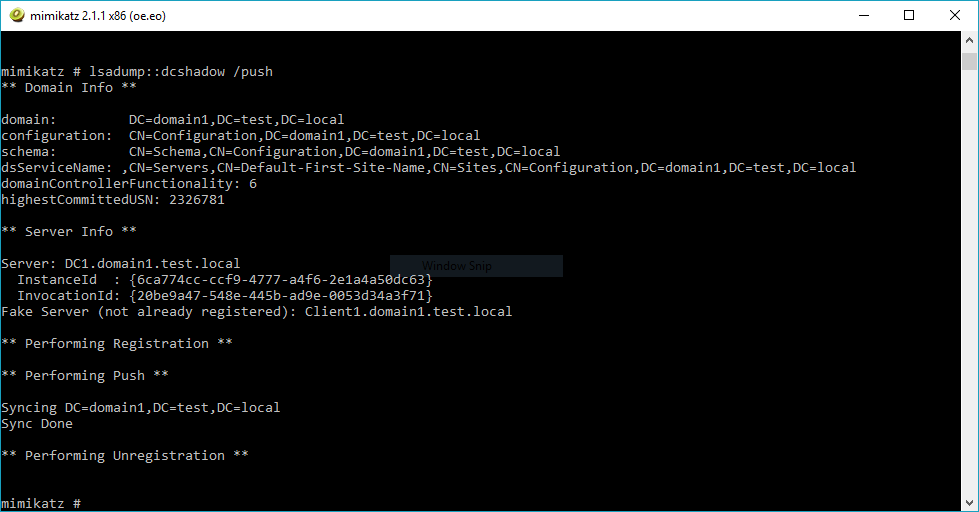
A domain controller shadow (DCShadow) attack is an attack designed to change directory objects using malicious replication. This attack can be performed from any machine by creating a rogue domain controller using a replication process.
DCShadow uses RPC and LDAP to:
- Register the machine account as a domain controller (using domain admin rights), and
- Perform replication (using the granted replication rights) over DRSUAPI and send changes to directory objects.
Azure ATP detects the attack by 2 security alerts:
- Suspicious domain controller promotion (potential DCShadow attack)
- Suspicious replication request (potential DCShadow attack)
Stay tuned. Your feedback is welcome.
0 Replies