- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint
- Windows Defender Application Control - Intune Management DLL's
Windows Defender Application Control - Intune Management DLL's
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 24 2021 03:52 AM
Hi,
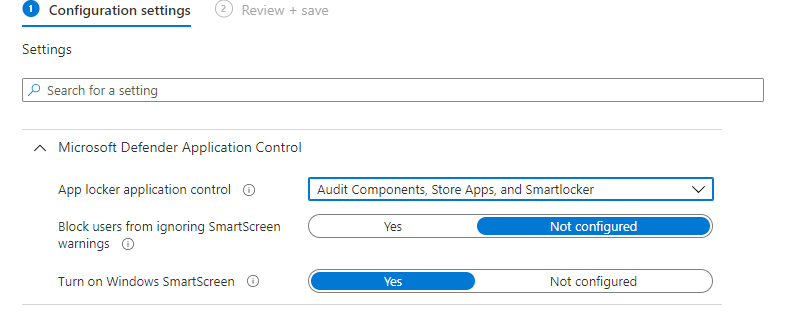
I'm busy deploying WDAC via Intune, and I was curious about the options and settings in the "Endpoint Security - Attack Surface Reduction - Application Control"-profile. This to check if it would offer some basic protection without having to implement additional profiles using xml files and to keep management simple.
Off course I started in Audit mode to see the results:
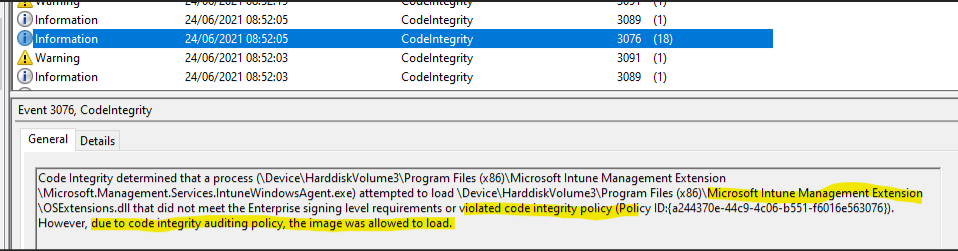
After applying and using my machine, I notice some logs which don't seem to be normal... You would expect the Intune Management Components would be trusted. Since, if you put in block mode you would still want to be able to manage your machine. Apparently, this isn't the case. For example, the OSExtentions.dll would be blocked because the file is not correctly signed. (Same for the GAC...)
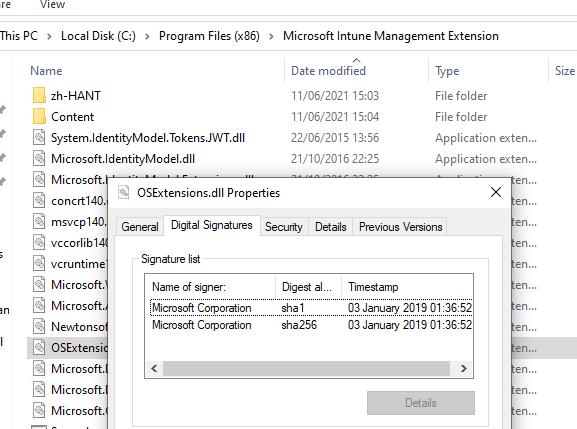
When checking the signature of the dll, it seems to be correctly signed....
So I don't know if this is by design or not...
(This was tested on Windows 10 Enterprise v21H1 - OS Build 19043.1052)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 24 2021 04:25 AM
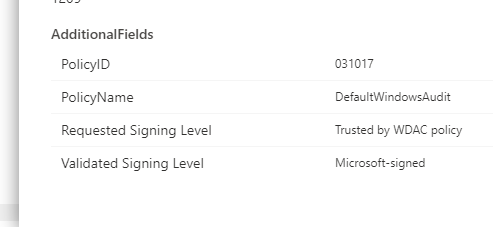
After some further investigation, it seems the "Default Windows" policy is applied and is causing this block... Still don't know why since it is signed by Microsoft....